Question: 8. Answer the questions in the below table (6 marks) Answer Question Which of the hacking attack phases can be mitigated by a strong password
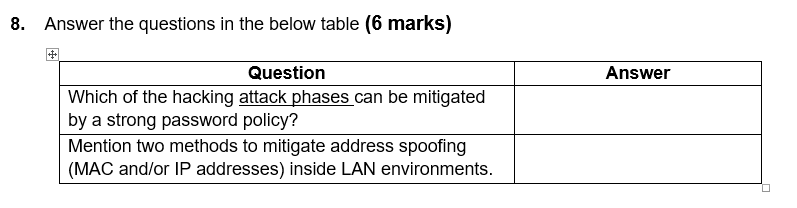
8. Answer the questions in the below table (6 marks) Answer Question Which of the hacking attack phases can be mitigated by a strong password policy? Mention two methods to mitigate address spoofing (MAC and/or IP addresses) inside LAN environments
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


