Question: 8. Security technologies - Access Control. (10%) (1) What tool can be used to solve the security threats, unauthorized access? (2) What are the two
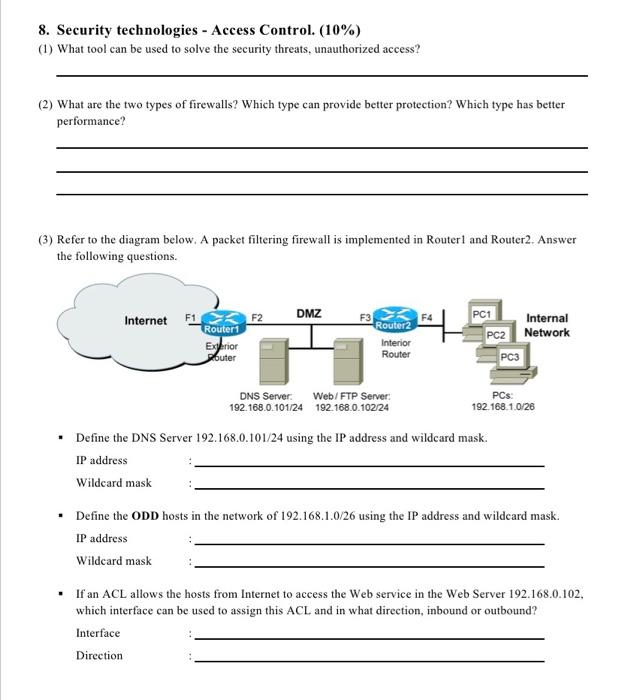
8. Security technologies - Access Control. (10%) (1) What tool can be used to solve the security threats, unauthorized access? (2) What are the two types of firewalls? Which type can provide better protection? Which type has better performance? (3) Refer to the diagram below. A packet filtering firewall is implemented in Router1 and Router2. Answer the following questions. F2 DMZ F4 Internet F1 Router1 Exterior outer F3 Router2 Interior Router PC1 Internal PC2 Network PC3 DNS Server: Web/FTP Server 192.168.0.101/24 192.168.0.102/24 PCs 192.168.1.0/26 Define the DNS Server 192.168.0.101/24 using the IP address and wildcard mask IP address Wildcard mask Define the ODD hosts in the network of 192.168.1.0/26 using the IP address and wildcard mask. IP address Wildcard mask If an ACL allows the hosts from Internet to access the Web service in the Web Server 192.168.0.102, which interface can be used to assign this ACL and in what direction, inbound or outbound? Interface Direction
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


