Question: A company needs to address an issue with its external DNS servers that allows an attacker to perform a full zone transfer if the IP
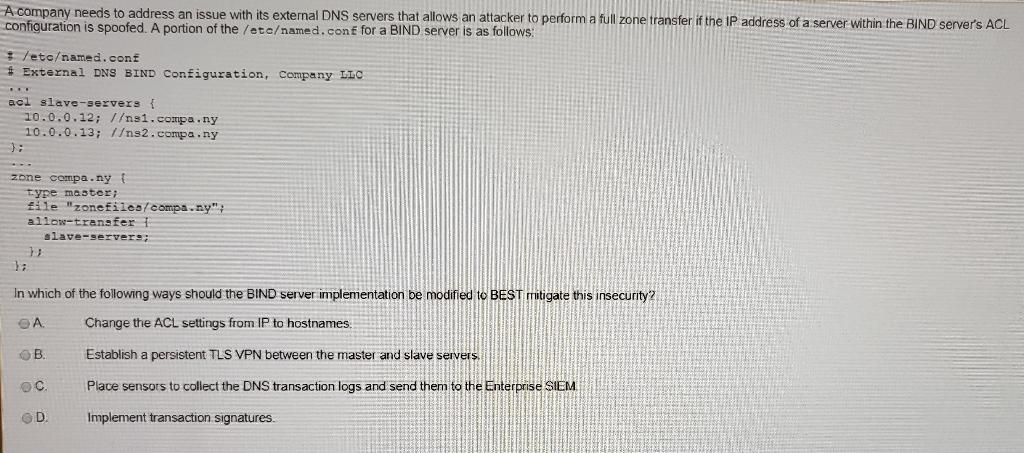
A company needs to address an issue with its external DNS servers that allows an attacker to perform a full zone transfer if the IP address of a server within the BIND server's ACL configuration is spoofed. A portion of the /eteamed.conf for a BIND server is as follows: ; /etcamed.conf # External DNS BIND Configuration, Company LLC acl slave-servers { 10.0.0.12; /s1.compa.ny 10.0.0.13; /s2.company zone compa.nyt type master; ile "zonefiles/company": allow-transfer 1 slave-servers; 1) In which of the following ways should the BIND server implementation be modified to BEST mitigate this insecurity? A Change the ACL settings from IP to hostnames OB Establish a persistent TLS VPN between the master and slave servers Place sensors to collect the DNS transaction logs and send them to the Enterprise SIEM OD Implement transaction signatures
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


