Question: = a) Consider the following SQL statement and answer the questions listed below. $conn= new mysqli (localhost, root, rootUser, Record); // $conn holds connection to
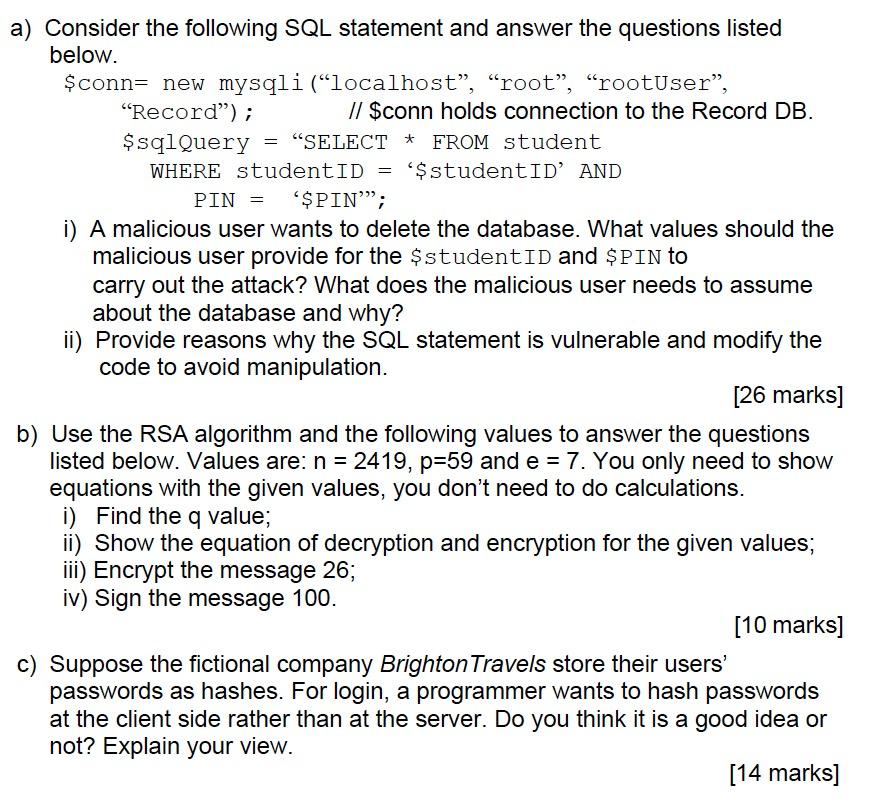
= a) Consider the following SQL statement and answer the questions listed below. $conn= new mysqli (localhost", "root, rootUser, Record); // $conn holds connection to the Record DB. $sqlQuery "SELECT * FROM student WHERE studentID = $studentID' AND PIN = '$PIN; i) A malicious user wants to delete the database. What values should the malicious user provide for the $studentID and $PIN to carry out the attack? What does the malicious user needs to assume about the database and why? ii) Provide reasons why the SQL statement is vulnerable and modify the code to avoid manipulation. [26 marks] b) Use the RSA algorithm and the following values to answer the questions listed below. Values are: n = 2419, p=59 and e = 7. You only need to show equations with the given values, you don't need to do calculations. i) Find the q value; ii) Show the equation of decryption and encryption for the given values; iii) Encrypt the message 26; iv) Sign the message 100. [10 marks] c) Suppose the fictional company Brighton Travels store their users' passwords as hashes. For login, a programmer wants to hash passwords at the client side rather than at the server. Do you think it is a good idea or not? Explain your view. [14 marks]
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


