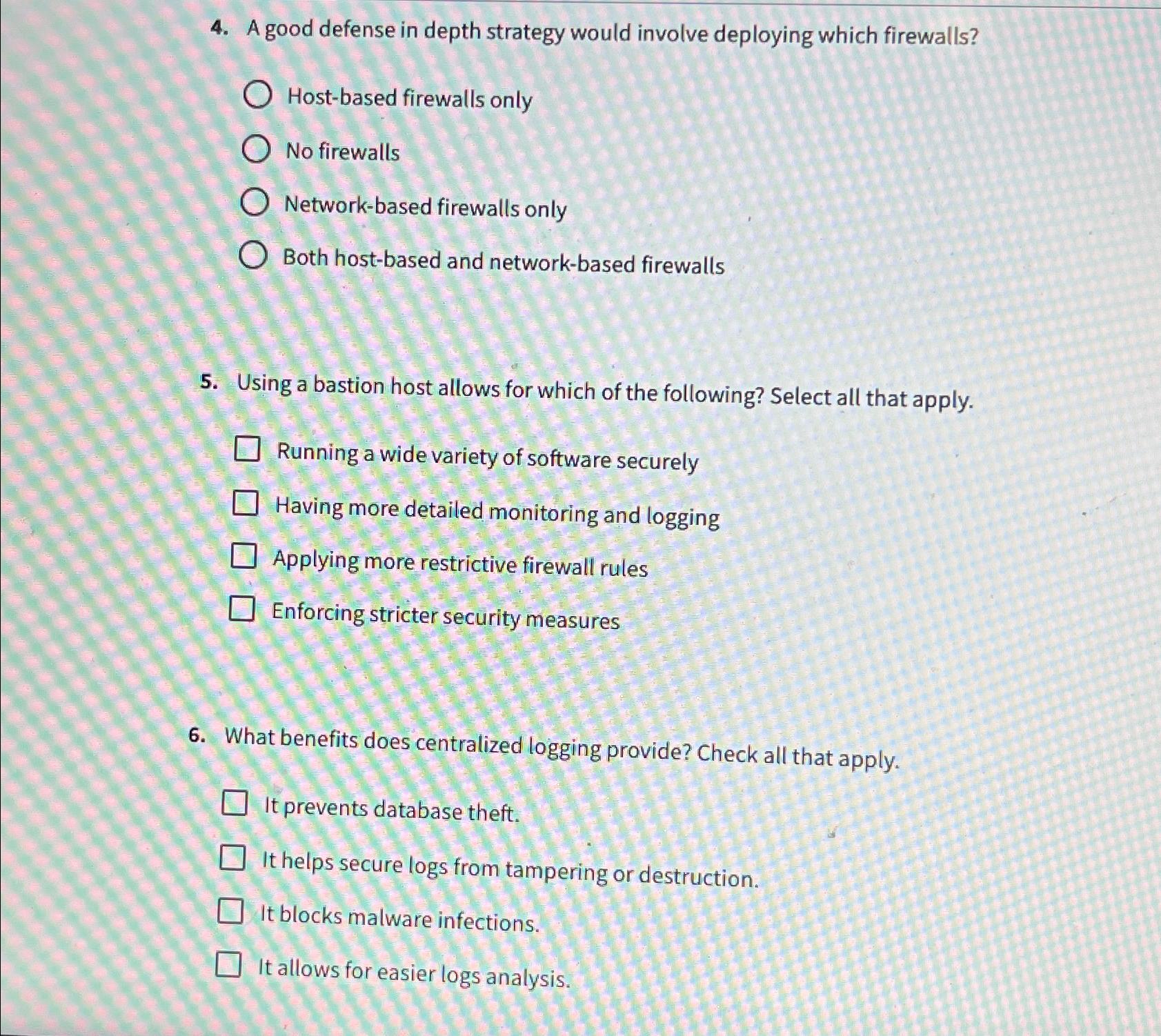
Question: A good defense in depth strategy would involve deploying which firewalls? Host - based firewalls only No firewalls Network - based firewalls only Both host
A good defense in depth strategy would involve deploying which firewalls?
Hostbased firewalls only
No firewalls
Networkbased firewalls only
Both hostbased and networkbased firewalls
Using a bastion host allows for which of the following? Select all that apply.
Running a wide variety of software securely
Having more detailed monitoring and logging
Applying more restrictive firewall rules
Enforcing stricter security measures
What benefits does centralized logging provide? Check all that apply.
It prevents database theft.
It helps secure logs from tampering or destruction.
It blocks malware infections.
It allows for easier logs analysis.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


