Question: A remote client C wants to prove to the server S that it knows its password without actually sending it across the internet. They
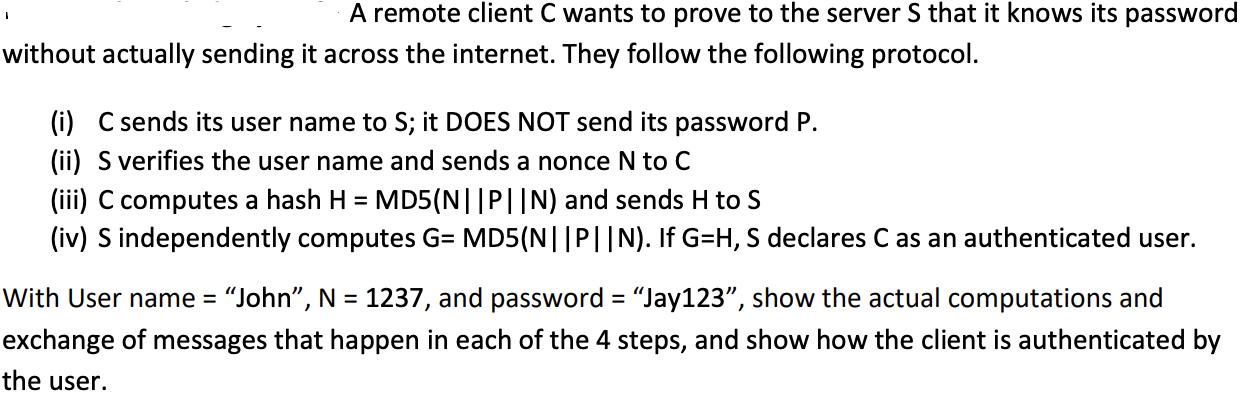
A remote client C wants to prove to the server S that it knows its password without actually sending it across the internet. They follow the following protocol. (i) C sends its user name to S; it DOES NOT send its password P. (ii) S verifies the user name and sends a nonce N to C (iii) C computes a hash H = MD5(N||P||N) and sends H to S (iv) S independently computes G= MD5(N||P||N). If G=H, S declares C as an authenticated user. With User name = "John, N = 1237, and password = "Jay123", show the actual computations and exchange of messages that happen in each of the 4 steps, and show how the client is authenticated by the user.
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


