Question: A security analyst is using a recently released security advisory to review historical logs, looking for the specific activity that was outlined in the advisory.
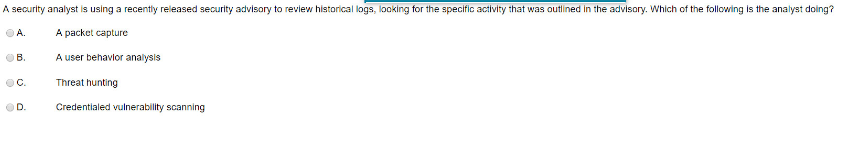
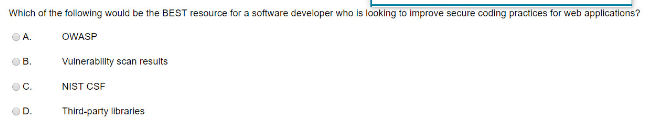
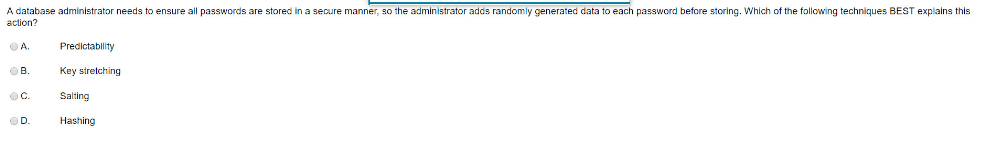
A security analyst is using a recently released security advisory to review historical logs, looking for the specific activity that was outlined in the advisory. Which of the following is the analyst doing? A. A packet capture B A user behavior analysis C Threat hunting D Credentialed vulnerability scanning Which of the following would be the BEST resource for a software developer who is looking to improve secure coding practices for web applications? A. OWASP OB Vulnerability scan results C NIST CSF OD Third-party libraries A database administrator needs to ensure all passwords are stored in a secure manner, so the administrator adds randomly generated data to each password before storing. Which of the following techniques BEST explains this action? Predictability Key stretching Salting Hashing
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


