A small company is using the topology shown below to secure its intranet while providing a less-secured
Question:
A small company is using the topology shown below to secure its intranet while providing a less-secured environment to its eCommerce DMZ server. The company is concerned that firewalls are not enough to detect and prevent network attacks. Hence, deployment of sensors to intrusion detection systems (IDS) and/or intrusion prevention systems (IPS) are needed in the network.
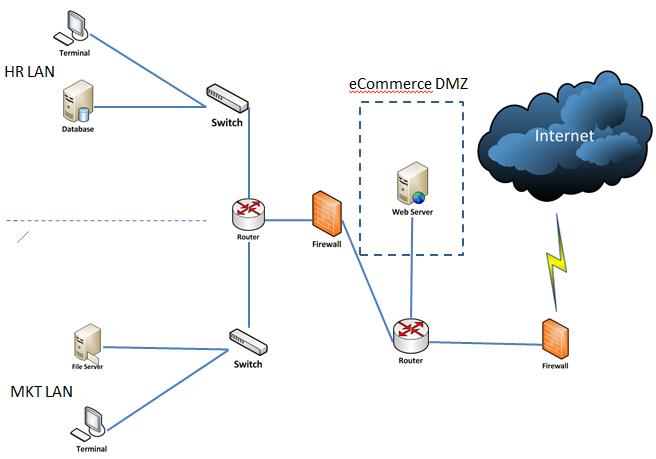
Company’s Requirements
Detect any malicious traffic entering the e-commerce server without performance penalty to traffic getting in the server from revenue-generating customers.
Stop any malicious traffic entering the human resources LAN (HR LAN).
Detect any malicious traffic entering the computer terminal in the marketing LAN (MKT LAN).
Stop any traffic entering the File Server in MKT LAN.
Deploy a centralized database and analysis console in the intranet to managing and monitoring both IDS and IPS sensors.





