Question: (a) What do you understand by the term 'shift register' commonly employed in PLC programs? (5 mar Implement a ladder logic PLC program for

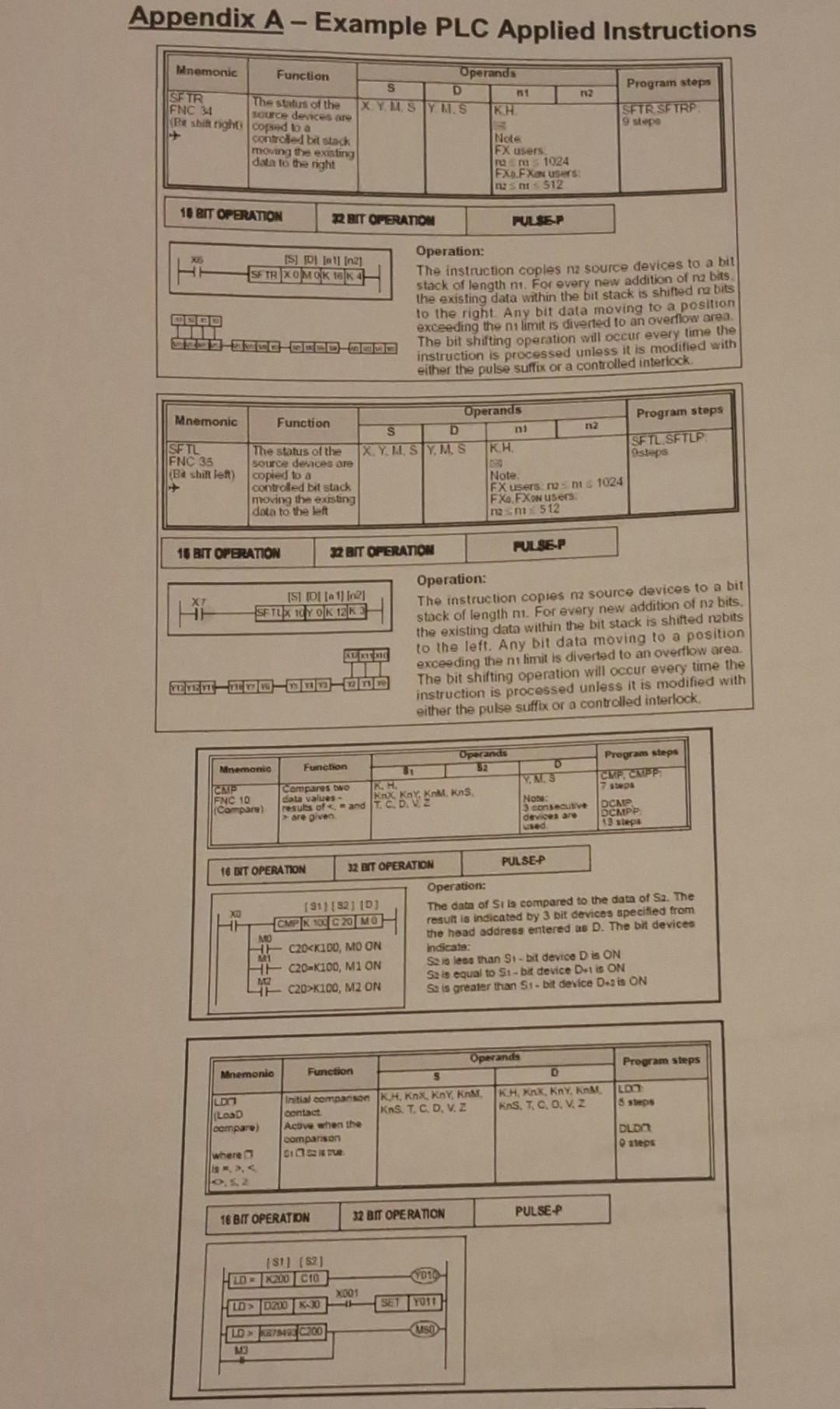
(a) What do you understand by the term 'shift register' commonly employed in PLC programs? (5 mar Implement a ladder logic PLC program for the problem, using a shift regis function (see Appendix A). Explain your solution. (25 mar Appendix A - Example PLC Applied Instructions Mnemonic Function The status of the Operands S D n1 112 SFTR XYMS YM.S K.H. FNC 34 (Be shift right source devices are copsed to a Note t FX users controlled bit stack moving the existing data to the right 18 BIT OPERATION ms 1024 FX FXa users: nzs mt512 PULSE-P Program steps SFTR SFTRP 9 stepe 22 BIT OPERATION [S] (0) [1] [2] FTR XOMOK 16K 4- Operation: The instruction coples nz source devices to a bit stack of length n1. For every new addition of n2 bits. the existing data within the bit stack is shifted na bits to the right. Any bit data moving to a position exceeding the ni limit is diverted to an overflow area. The bit shifting operation will occur every time the instruction is processed unless it is modified with either the pulse suffix or a controlled interlock. Mnemonic Operands Function S D 112 n SFTL The status of the XY. M. SY, M.S K.H. FNC 35 source devices are (Ba shift left) copied to a Note. + controlled bit stack FX users noms 1024 FXo. FXON users n2sm 512 Program steps SFTL.SFTLP 9steps moving the existing data to the left 16 BIT OPERATION 32 BIT OPERATION [S] [D] [1] [2] SF TLX 10Y OK 12K3 MUB-UHM MAN HAZIA Operation: PULSE-P The instruction copies nz source devices to a bit stack of length ni. For every new addition of n2 bits. the existing data within the bit stack is shifted nabits to the left. Any bit data moving to a position exceeding the nt limit is diverted to an overflow area. The bit shifting operation will occur every time the instruction is processed unless it is modified with either the pulse suffix or a controlled interlock. Mnemonic CAIP FNC 10 (Compare) Function Compares two data values- resuls of are given 81 Operands 52 D K.H. Y.M.S Program steps CMP. CMPP and Knx Kay, KnM. KnS T. C. D. VE steps Note: 3 consecutive devices are used 13 steps DCMP DCMPP 16 BIT OPERATION 32 BIT OPERATION XD MO A11 M2 [91] [92] [D] CMP K 100 C 20 MO C20
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


