Question: AA learn.comptia.org 8 1 % C Login | Compt A CompTIA. Assessment / CompTIA Domain 4 . 0 Security Operations Assessment This Question: 0 2
AA
learn.comptia.org
C Login ComptA
CompTIA.
Assessment CompTIA
Domain Security Operations Assessment
This Question: :
Total: :
Complete
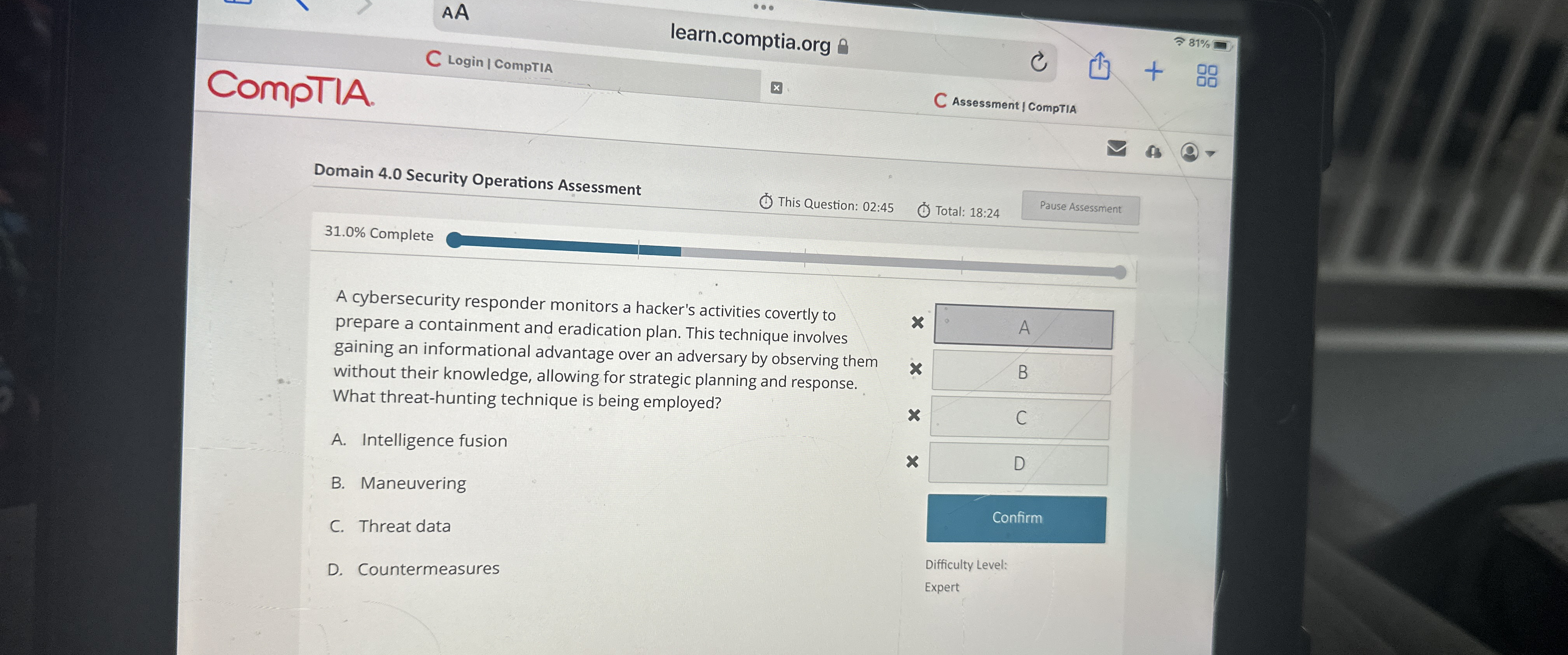
A cybersecurity responder monitors a hacker's activities covertly to prepare a containment and eradication plan. This technique involves gaining an informational advantage over an adversary by observing them without their knowledge, allowing for strategic planning and response. What threathunting technique is being employed?
A Intelligence fusion
B Maneuvering
C Threat data
D Countermeasures
Difficulty Level:
Expert
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


