Question: After reviewing the network system security plan and the network diagram, select a security objective ( confidentiality , integrity, or availability) as the focus for
After reviewing the network system security plan and the network diagram, select a security objective (confidentiality, integrity, or availability) as the focus for your analysis and recommendations. Then prepare a report to communicate the systems deficiencies and your recommendations to the organizations security team.
Specifically, you must address the critical elements listed below. The codes shown in brackets indicate the course competency to which each critical element is aligned.
- Identify a hardware-based deficiency in the system and explain why this is an issue, based on your selected security objective.
- Recommend a method to remediate the hardware-based issue and protect the system.
- Identify a software-based deficiency in the system and explain why this is an issue, based on your selected security objective.
- Recommend a method to remediate the software-based issue and protect the system
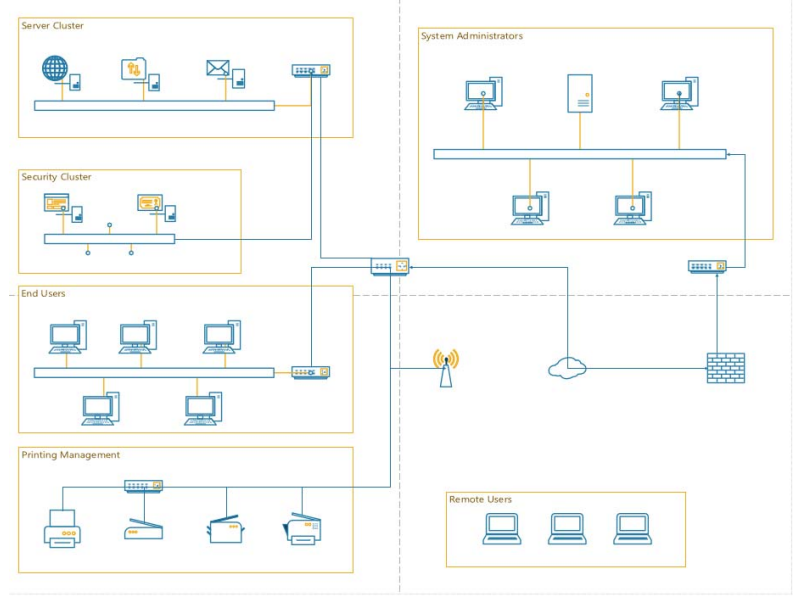
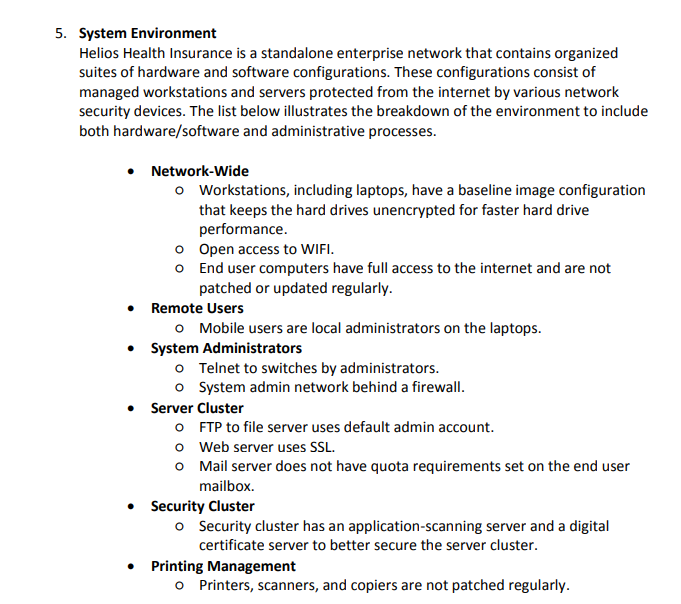
System Environment Helios Health Insurance is a standalone enterprise network that contains organized suites of hardware and software configurations. These configurations consist of managed workstations and servers protected from the internet by various network security devices. The list below illustrates the breakdown of the environment to include both hardware/software and administrative processes. - Network-Wide - Workstations, including laptops, have a baseline image configuration that keeps the hard drives unencrypted for faster hard drive performance. - Open access to WIFI. - End user computers have full access to the internet and are not patched or updated regularly. - Remote Users - Mobile users are local administrators on the laptops. - System Administrators o Telnet to switches by administrators. o System admin network behind a firewall. - Server Cluster - FTP to file server uses default admin account. - Web server uses SSL. - Mail server does not have quota requirements set on the end user mailbox. - Security Cluster - Security cluster has an application-scanning server and a digital certificate server to better secure the server cluster. - Printing Management - Printers, scanners, and copiers are not patched regularly
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


