Question: Alice and Bob meet and agree to use the code C:{,a,b,c,,z}{0,1,2,3,26},C()=0,C(a)=1,,C(z)=26 to map characters to integers and to use the function E:{0,1,2,3,26}>{0,1,2,3,26}E(x)=((5x)3)mod27 for encryption. The
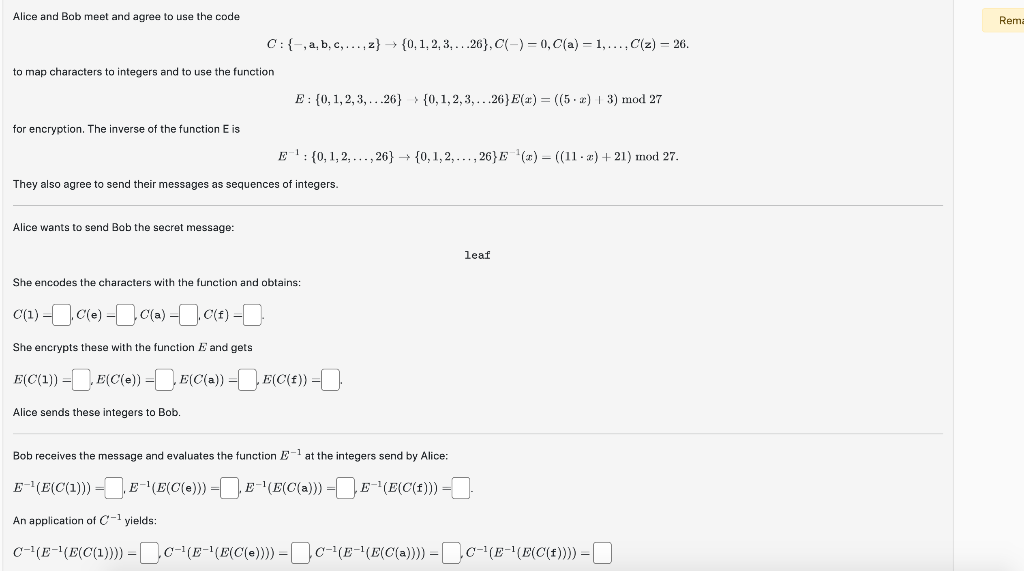
Alice and Bob meet and agree to use the code C:{,a,b,c,,z}{0,1,2,3,26},C()=0,C(a)=1,,C(z)=26 to map characters to integers and to use the function E:{0,1,2,3,26}>{0,1,2,3,26}E(x)=((5x)3)mod27 for encryption. The inverse of the function E is E1:{0,1,2,,26}{0,1,2,,26}E1(x)=((11x)+21)mod27. They also agree to send their messages as sequences of integers. Alice wants to send Bob the secret message: leaf She encodes the characters with the function and obtains: C(1)=C(e)=C(a)=C(f)= She encrypts these with the function E and gets E(C(1))=E(C(e))=E(C(a))=E(C(f))= Alice sends these integers to Bob. Bob receives the message and evaluates the function E1 at the integers send by Alice: E1(E(C(1)))=E1(E(C(e)))=,E1(E(C(a)))=E1(E(C(f)))= An application of C1 yields: C1(E1(E(C(1))))=C1(E1(E(C(e))))=C1(E1(E(C(a))))=,C1(E1(E(C(f))))=
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


