Question: Alice designed a hash chain based authentication protocol as follows Step 1: The authentication server (i.e., verifier) chooses a cryptographic hash function h: {0,1}* {0,1}
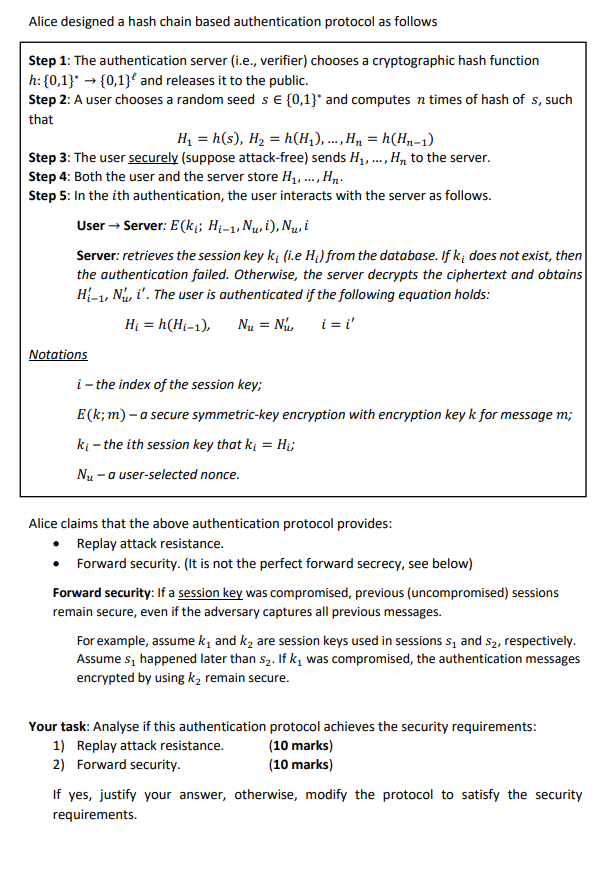
Alice designed a hash chain based authentication protocol as follows Step 1: The authentication server (i.e., verifier) chooses a cryptographic hash function h: {0,1}* {0,1} and releases it to the public. Step 2: A user chooses a random seed s {0,1}* and computes n times of hash of s, such that H4 = h(s), H2 = h(H2), ...,Hn = h(Hn-1) Step 3: The user securely (suppose attack-free) sends H1,..., Hy to the server. Step 4: Both the user and the server store H2, ..., Hn. Step 5: In the ith authentication, the user interacts with the server as follows. User Server: E(ki; Hi-1,Ni), Ni Server: retrieves the session key ki (i.e Hi) from the database. If ki does not exist, then the authentication failed. Otherwise, the server decrypts the ciphertext and obtains H-1, Nu, i'. The user is authenticated if the following equation holds: Hi = h(Hi-1), N = N i =i' Notations i - the index of the session key; E(k; m) - a secure symmetric-key encryption with encryption key k for message m; ki - the ith session key that ki = Hij Nu - a user-selected nonce. = = Alice claims that the above authentication protocol provides: Replay attack resistance. Forward security. (It is not the perfect forward secrecy, see below) Forward security: If a session key was compromised, previous (uncompromised) sessions remain secure, even if the adversary captures all previous messages. For example, assume kand ky are session keys used in sessions sq and Sy, respectively. Assume sy happened later than S2. If k, was compromised, the authentication messages encrypted by using k remain secure. Your task: Analyse if this authentication protocol achieves the security requirements: 1) Replay attack resistance. (10 marks) 2) Forward security. (10 marks) If yes, justify your answer, otherwise, modify the protocol to satisfy the security requirements. Alice designed a hash chain based authentication protocol as follows Step 1: The authentication server (i.e., verifier) chooses a cryptographic hash function h: {0,1}* {0,1} and releases it to the public. Step 2: A user chooses a random seed s {0,1}* and computes n times of hash of s, such that H4 = h(s), H2 = h(H2), ...,Hn = h(Hn-1) Step 3: The user securely (suppose attack-free) sends H1,..., Hy to the server. Step 4: Both the user and the server store H2, ..., Hn. Step 5: In the ith authentication, the user interacts with the server as follows. User Server: E(ki; Hi-1,Ni), Ni Server: retrieves the session key ki (i.e Hi) from the database. If ki does not exist, then the authentication failed. Otherwise, the server decrypts the ciphertext and obtains H-1, Nu, i'. The user is authenticated if the following equation holds: Hi = h(Hi-1), N = N i =i' Notations i - the index of the session key; E(k; m) - a secure symmetric-key encryption with encryption key k for message m; ki - the ith session key that ki = Hij Nu - a user-selected nonce. = = Alice claims that the above authentication protocol provides: Replay attack resistance. Forward security. (It is not the perfect forward secrecy, see below) Forward security: If a session key was compromised, previous (uncompromised) sessions remain secure, even if the adversary captures all previous messages. For example, assume kand ky are session keys used in sessions sq and Sy, respectively. Assume sy happened later than S2. If k, was compromised, the authentication messages encrypted by using k remain secure. Your task: Analyse if this authentication protocol achieves the security requirements: 1) Replay attack resistance. (10 marks) 2) Forward security. (10 marks) If yes, justify your answer, otherwise, modify the protocol to satisfy the security requirements





