Question: Alice wants to send an encrypted message to Bob. Which of the following figures illustrates the REGULAR use of asymmetric cryptography to achieve this goal?
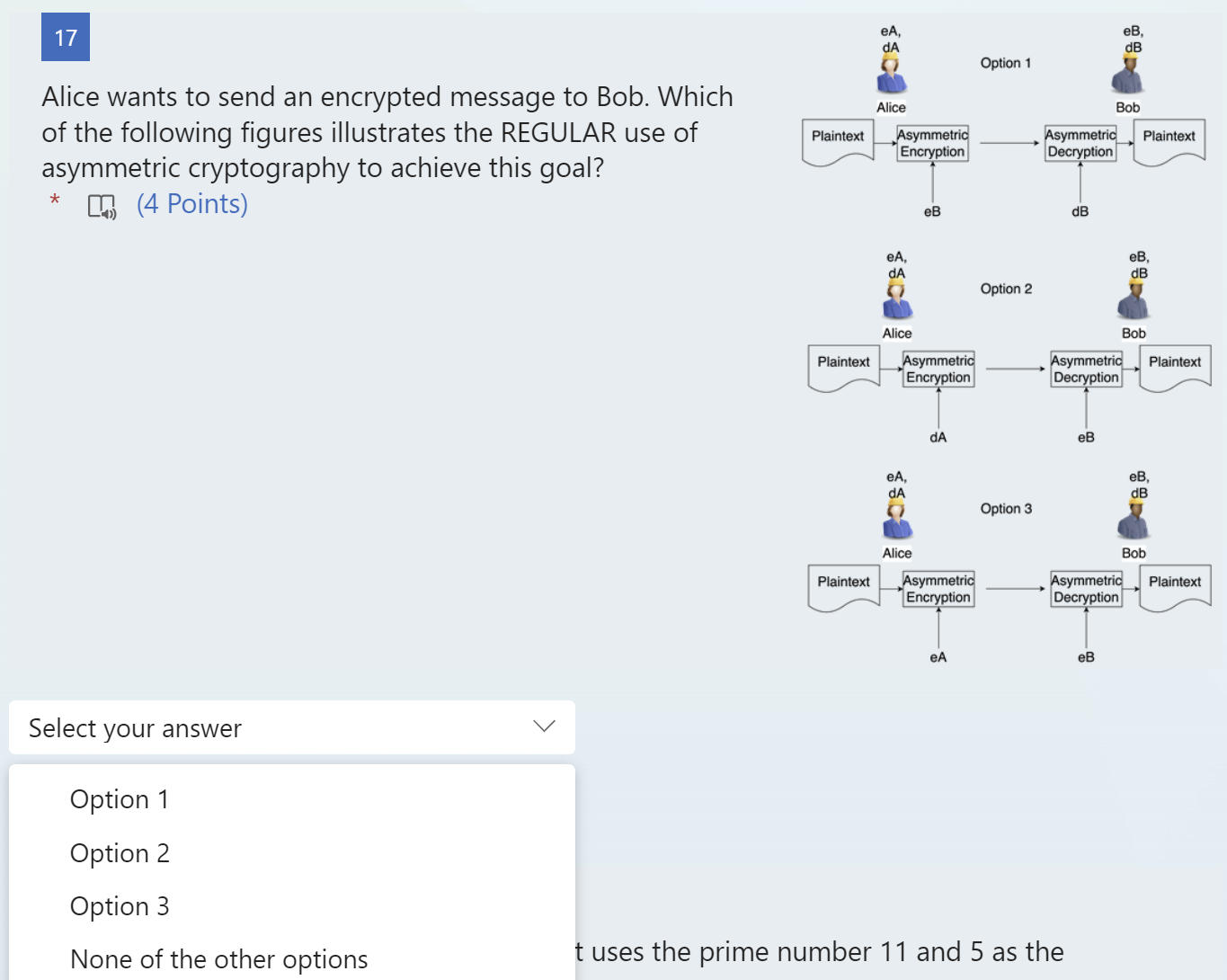

Alice wants to send an encrypted message to Bob. Which of the following figures illustrates the REGULAR use of asymmetric cryptography to achieve this goal? (4 Points) uses the prime number 11 and 5 as the What is the order of the cyclic subgroup that uses the prime number 11 and 5 as the generator? * 4) (8 Points) mit will be sent to the form owner. Microsoft is not respor s form owner. Never give out your password. 9 10 11
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


