Question: Answer all for a thumbs up! QUESTION 1 Information Systems Security Certification Consortium, Inc. (ISC)2 is the baseline for federal and DoD work-role definitions. True
 Answer all for a thumbs up!
Answer all for a thumbs up!
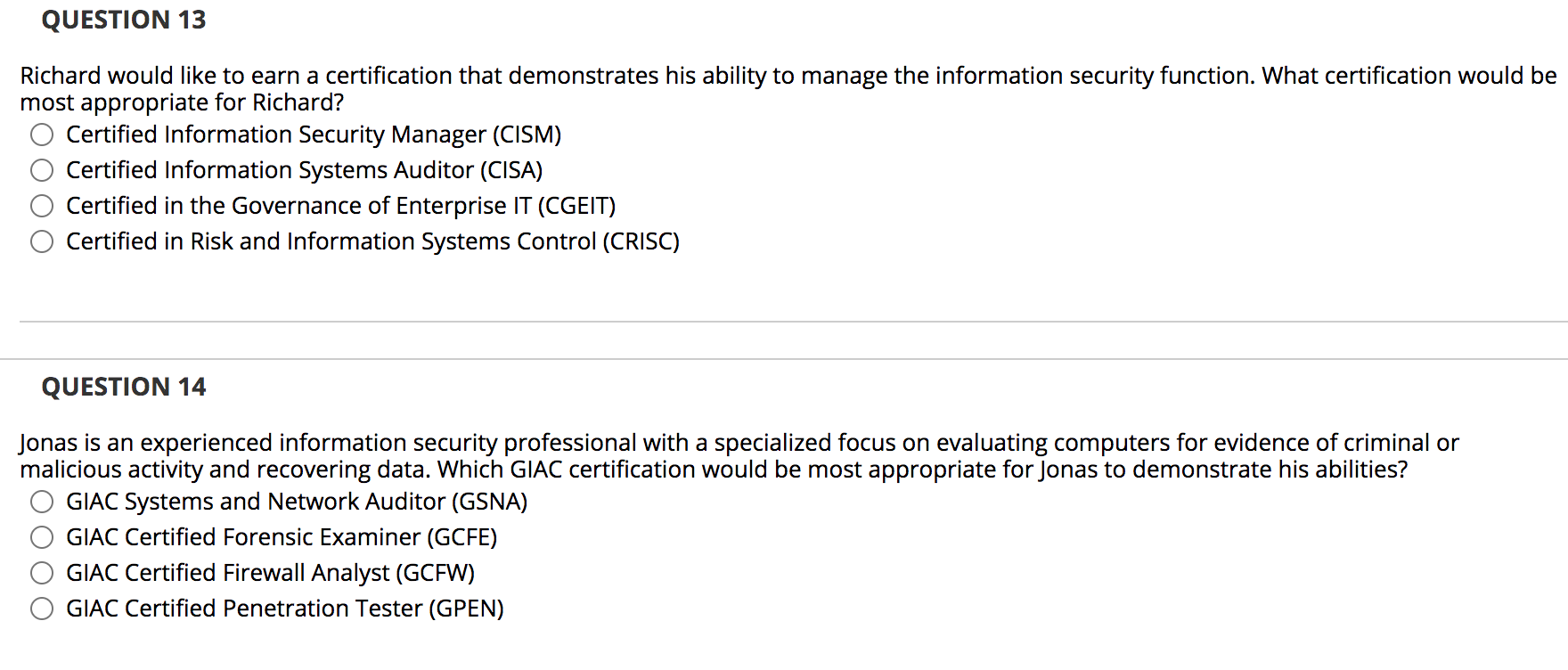
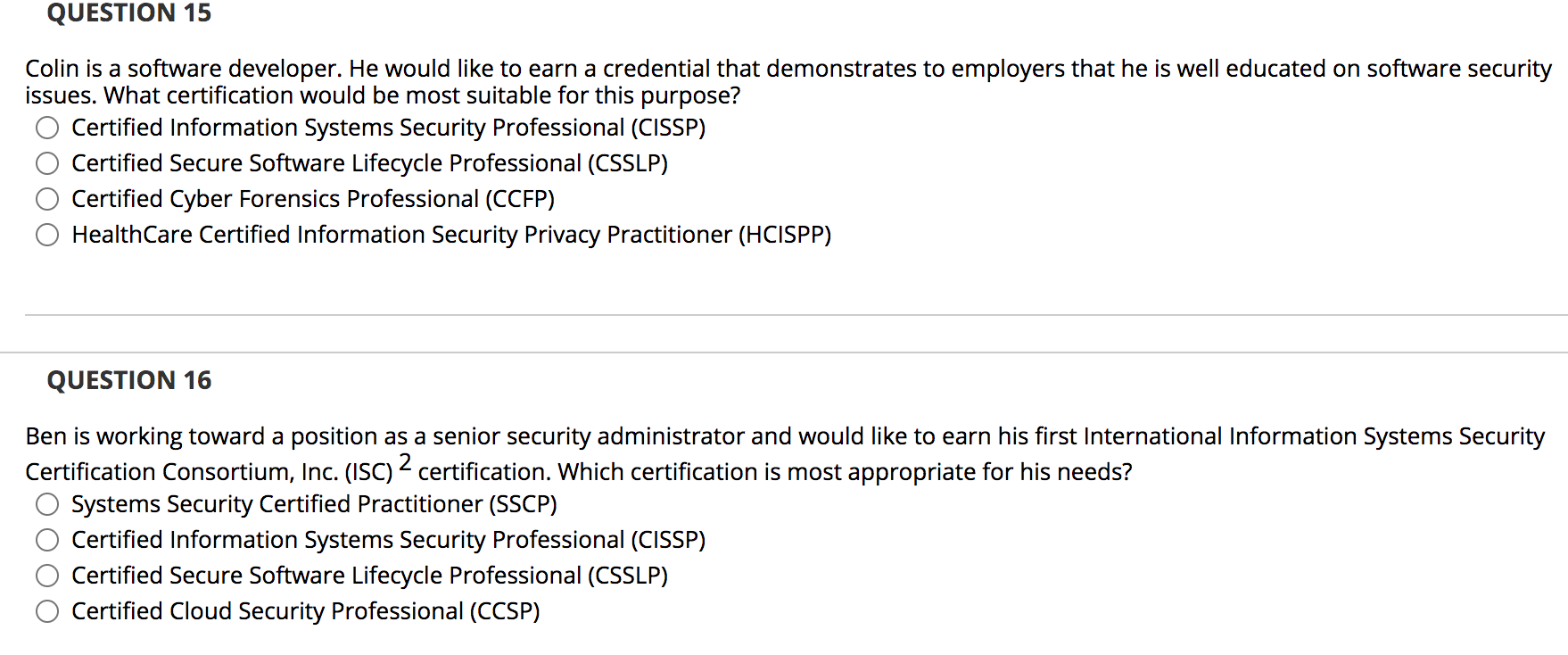
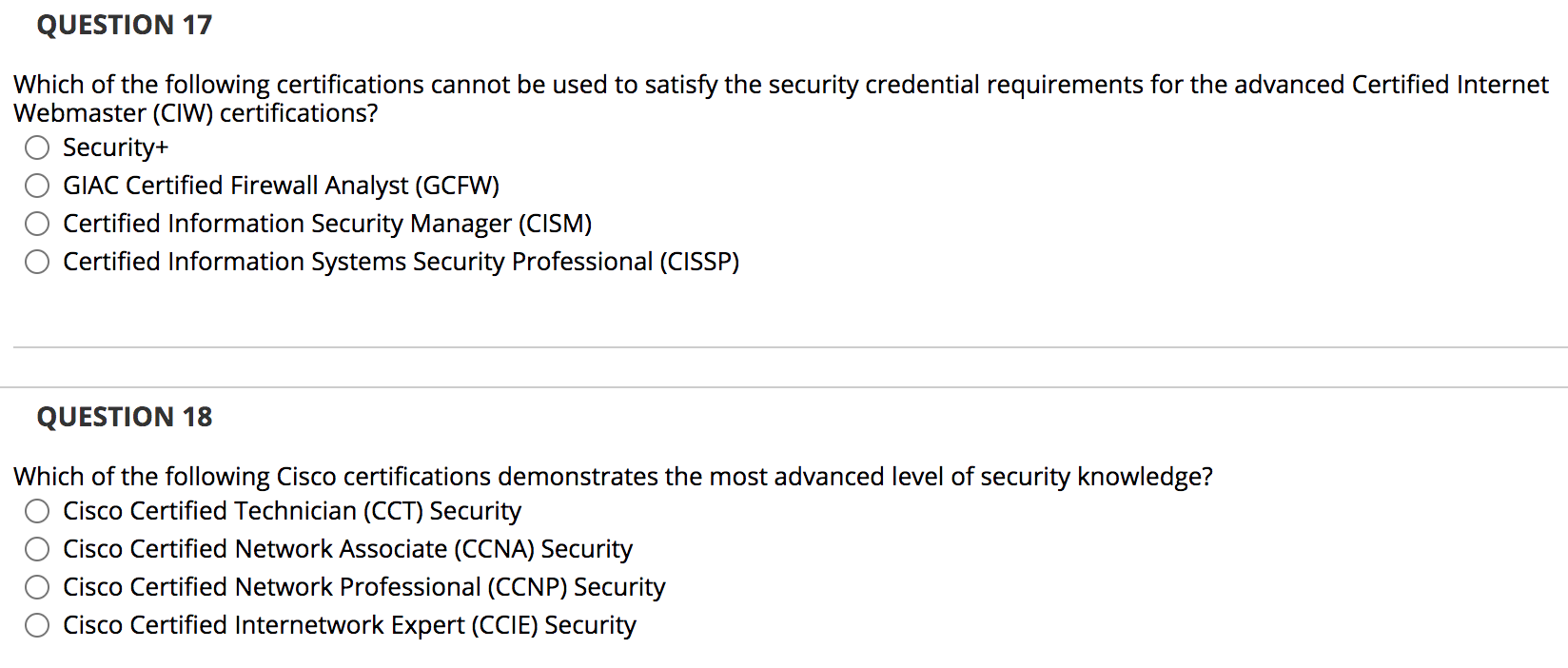
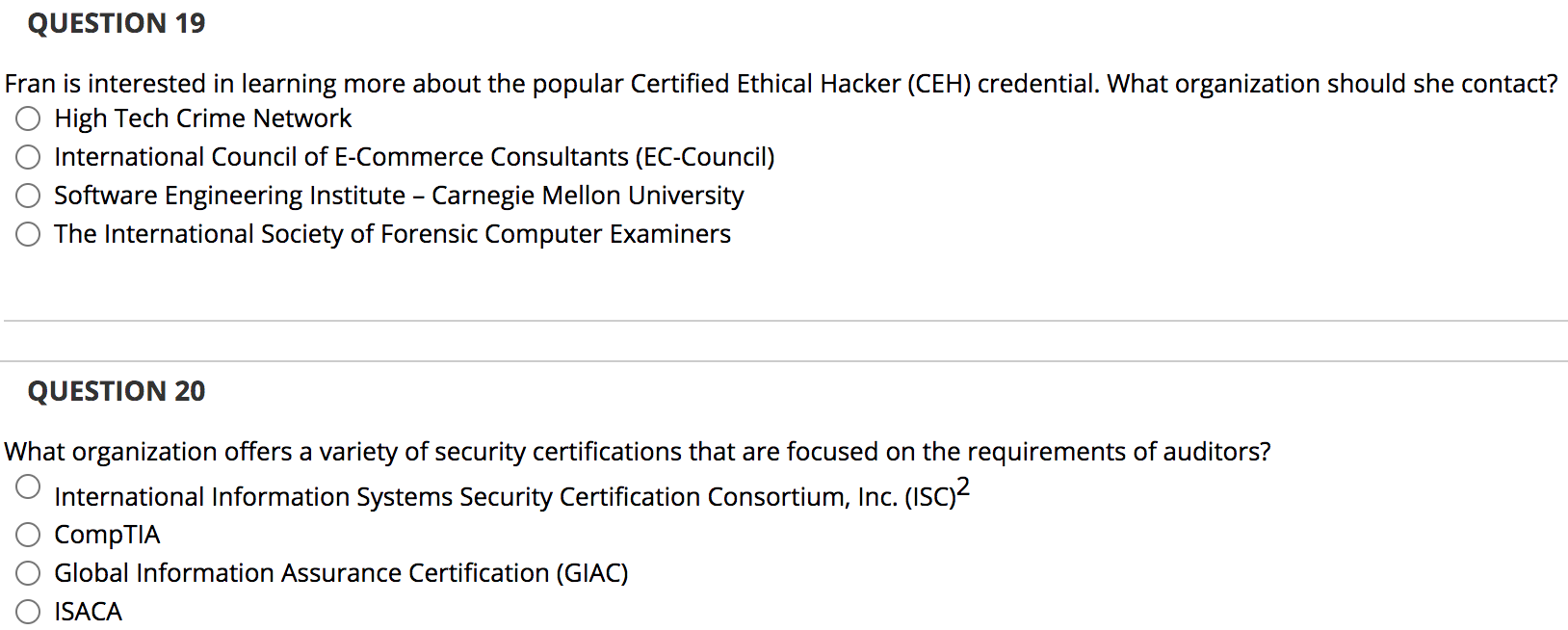
QUESTION 1 Information Systems Security Certification Consortium, Inc. (ISC)2 is the baseline for federal and DoD work-role definitions. True False QUESTION 2 The CISSP-ISSEP concentration requires that a candidate demonstrate two years of professional experience in the area of architecture. O True False QUESTION 3 A common method for identifying what skills a security professional possesses is his or her level of certification. True False QUESTION 4 DoD and NSA have adopted several training standards to serve as a pathway to satisfy Directive 8140. Although they are called standards, they are really training requirements for specific job responsibilities. True False QUESTION 5 Dod Directive 8570.01 is a voluntary certification requirement. O True False QUESTION 6 The HealthCare Certified Information Security and Privacy Practitioner (HCISPP) credential recognizes the knowledge and skills necessary to perform and conduct security and privacy work for health care organizations. True False QUESTION 7 Certified Internet Webmaster (CIW) offers several credentials that focus on both general and web-related security. True False QUESTION 8 RSA is a global provider of security, risk, and compliance solutions for enterprise environments. O True O False QUESTION 9 The Certified Secure Software Lifecycle Professional (CSSLP) credential measures the knowledge and skills necessary for professionals involved in the process of authorizing and maintaining information systems. O True False QUESTION 10 CompTIA Security+ is an entry-level security certification. True False QUESTION 11 What type of security role is covered by the Committee on National Security Systems (CNSS) Training Standard CNSS-4012? Senior System Manager System Administrator Information Assurance Officer Risk Analyst QUESTION 12 What certification focuses on information systems audit, control, and security professionals? Certified Information Security Manager (CISM) Certified Information Systems Auditor (CISA) Certified in the Governance of Enterprise IT (CGEIT) Certified in Risk and Information Systems Control (CRISC) QUESTION 13 Richard would like to earn a certification that demonstrates his ability to manage the information security function. What certification would be most appropriate for Richard? O Certified Information Security Manager (CISM) Certified Information Systems Auditor (CISA) Certified in the Governance of Enterprise IT (CGEIT) Certified in Risk and Information Systems Control (CRISC) QUESTION 14 Jonas is an experienced information security professional with a specialized focus on evaluating computers for evidence of criminal or malicious activity and recovering data. Which GIAC certification would be most appropriate for Jonas to demonstrate his abilities? GIAC Systems and Network Auditor (GSNA) GIAC Certified Forensic Examiner (GCFE) GIAC Certified Firewall Analyst (GCFW) GIAC Certified Penetration Tester (GPEN) QUESTION 15 Colin is a software developer. He would like to earn a credential that demonstrates to employers that he is well educated on software security issues. What certification would be most suitable for this purpose? Certified Information Systems Security Professional (CISSP) Certified Secure Software Lifecycle Professional (CSSLP) Certified Cyber Forensics Professional (CCFP) Health Care Certified Information Security Privacy Practitioner (HCISPP) QUESTION 16 Ben is working toward a position as a senior security administrator and would like to earn his first International Information Systems Security Certification Consortium, Inc. (ISC) - certification. Which certification is most appropriate for his needs? Systems Security Certified Practitioner (SSCP) Certified Information Systems Security Professional (CISSP) Certified Secure Software Lifecycle Professional (CSSLP) Certified Cloud Security Professional (CCSP) QUESTION 17 Which of the following certifications cannot be used to satisfy the security credential requirements for the advanced Certified Internet Webmaster (CIW) certifications? Security+ GIAC Certified Firewall Analyst (GCFW) Certified Information Security Manager (CISM) Certified Information Systems Security Professional (CISSP) QUESTION 18 Which of the following Cisco certifications demonstrates the most advanced level of security knowledge? Cisco Certified Technician (CCT) Security Cisco Certified Network Associate (CCNA) Security Cisco Certified Network Professional (CCNP) Security Cisco Certified Internetwork Expert (CCIE) Security QUESTION 19 Fran is interested in learning more about the popular Certified Ethical Hacker (CEH) credential. What organization should she contact? High Tech Crime Network International Council of E-Commerce Consultants (EC-Council) Software Engineering Institute - Carnegie Mellon University O The International Society of Forensic Computer Examiners QUESTION 20 What organization offers a variety of security certifications that are focused on the requirements of auditors? International Information Systems Security Certification Consortium, Inc. (ISC)2 CompTIA Global Information Assurance Certification (GIAC) ISACA
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


