Question: ANSWER ALL QUESTIONS SECTION B: ATTEMPT QUESTION 1 AND ANY OTHER TWO (2) QUESTIONS 20 Marks Question 1: a) Select the correct answer from the
ANSWER ALL QUESTIONS
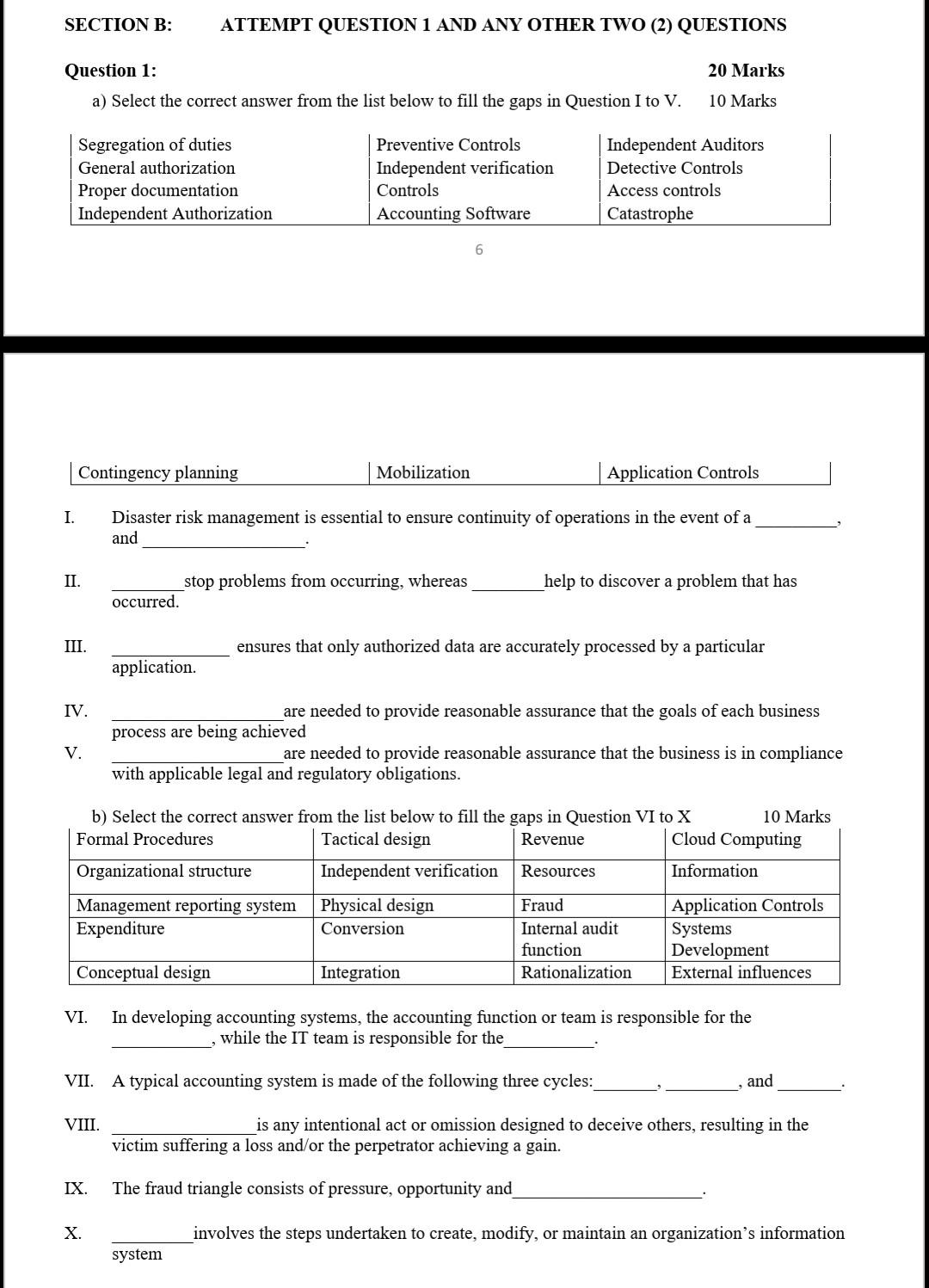
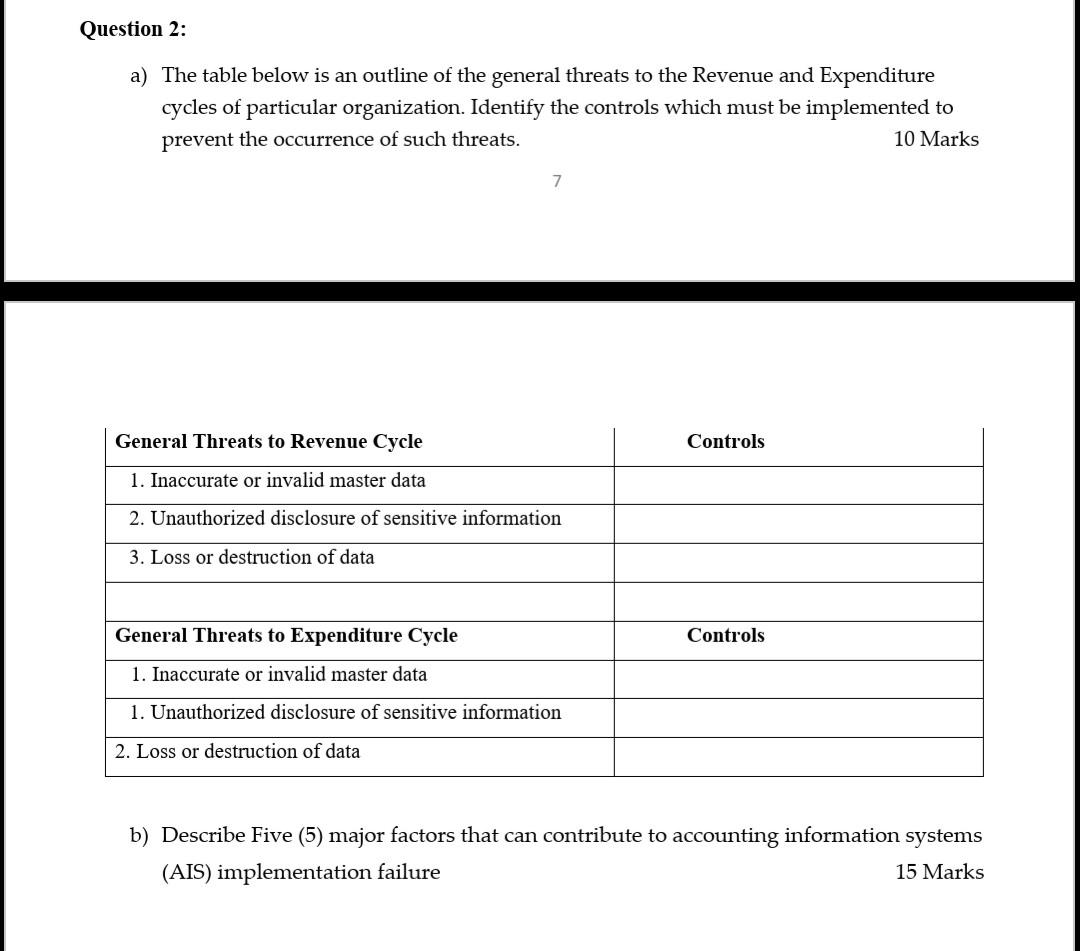
SECTION B: ATTEMPT QUESTION 1 AND ANY OTHER TWO (2) QUESTIONS 20 Marks Question 1: a) Select the correct answer from the list below to fill the gaps in Question I to V. 10 Marks Segregation of duties General authorization Proper documentation Independent Authorization Preventive Controls Independent verification Controls Accounting Software Independent Auditors Detective Controls Access controls Catastrophe 6 Contingency planning Mobilization Application Controls I. Disaster risk management is essential to ensure continuity of operations in the event of a and II. stop problems from occurring, whereas occurred. help to discover a problem that has III. ensures that only authorized data are accurately processed by a particular application IV. V. are needed to provide reasonable assurance that the goals of each business process are being achieved are needed to provide reasonable assurance that the business is in compliance with applicable legal and regulatory obligations. b) Select the correct answer from the list below to fill the gaps in Question VI to X 10 Marks Formal Procedures Tactical design Revenue Cloud Computing Organizational structure Independent verification Resources Information Management reporting system Physical design Fraud Application Controls Expenditure Conversion Internal audit Systems function Development Conceptual design Integration Rationalization External influences VI. In developing accounting systems, the accounting function or team is responsible for the while the IT team is responsible for the VII. A typical accounting system is made of the following three cycles: and VIII. is any intentional act or omission designed to deceive others, resulting in the victim suffering a loss and/or the perpetrator achieving a gain. IX. The fraud triangle consists of pressure, opportunity and X. involves the steps undertaken to create, modify, or maintain an organization's information system Question 2: a) The table below is an outline of the general threats to the Revenue and Expenditure cycles of particular organization. Identify the controls which must be implemented to prevent the occurrence of such threats. 10 Marks 7 General Threats to Revenue Cycle Controls 1. Inaccurate or invalid master data 2. Unauthorized disclosure of sensitive information 3. Loss or destruction of data General Threats to Expenditure Cycle Controls 1. Inaccurate or invalid master data 1. Unauthorized disclosure of sensitive information 2. Loss or destruction of data b) Describe Five (5) major factors that can contribute to accounting information systems (AIS) implementation failure 15 Marks
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


