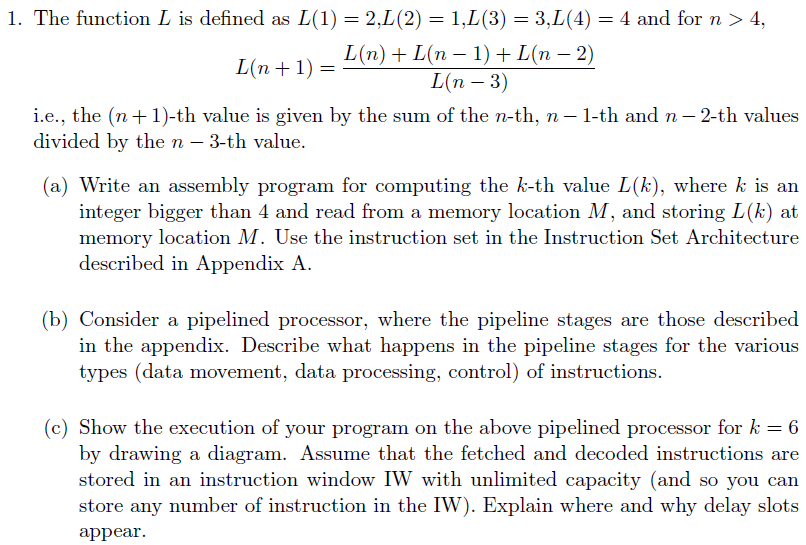
Question: Appendix: 1. The function L is defined as L(1) = 2,L (2) = 1,L (3) = 3,L(4) = 4 and for n > 4, L(n)
Appendix:
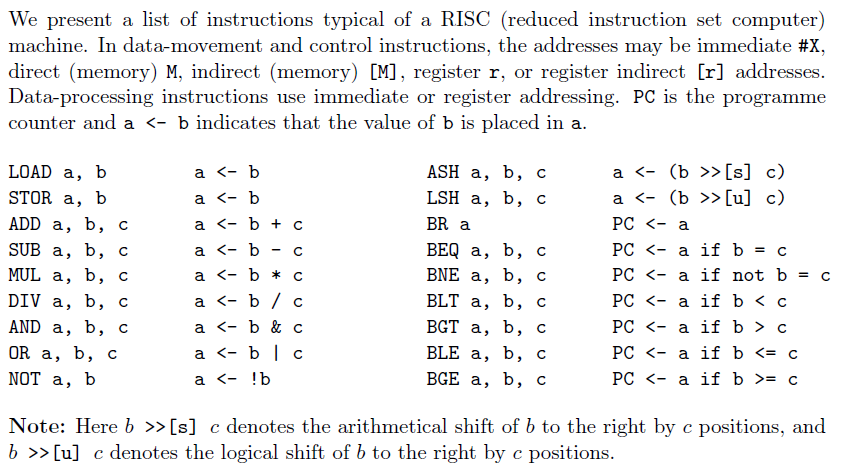

1. The function L is defined as L(1) = 2,L (2) = 1,L (3) = 3,L(4) = 4 and for n > 4, L(n) + L(n 1) + L(n 2) L(n + 1) = L(n-3) i.e., the (n+1)-th value is given by the sum of the n-th, n-1-th and n-2-th values divided by the n-3-th value. (a) Write an assembly program for computing the k-th value L(k), where k is an integer bigger than 4 and read from a memory location M, and storing L(k) at memory location M. Use the instruction set in the Instruction Set Architecture described in Appendix A. (b) Consider a pipelined processor, where the pipeline stages are those described in the appendix. Describe what happens in the pipeline stages for the various types (data movement, data processing, control) of instructions. (c) Show the execution of your program on the above pipelined processor for k= 6 by drawing a diagram. Assume that the fetched and decoded instructions are stored in an instruction window IW with unlimited capacity (and so you can store any number of instruction in the IW). Explain where and why delay slots appear. We present a list of instructions typical of a RISC (reduced instruction set computer) machine. In data-movement and control instructions, the addresses may be immediate #X, direct (memory) M, indirect (memory) [M], register r, or register indirect [r] addresses. Data-processing instructions use immediate or register addressing. PC is the programme counter and a >[s] c) a >[u] c) PC C PC = c Note: Here b >>[s] c denotes the arithmetical shift of b to the right by c positions, and b >>[u] c denotes the logical shift of b to the right by c positions. A.2 The pipeline We will use a five-stage pipeline: IF (instruction fetch), ID (instruction decode), RR (register read), EX (execute instruction), WB (write back result into register). Note that for some instructions (e.g., LOAD r, #x) some of the pipeline stages (e.g., RR) are not needed. 1. The function L is defined as L(1) = 2,L (2) = 1,L (3) = 3,L(4) = 4 and for n > 4, L(n) + L(n 1) + L(n 2) L(n + 1) = L(n-3) i.e., the (n+1)-th value is given by the sum of the n-th, n-1-th and n-2-th values divided by the n-3-th value. (a) Write an assembly program for computing the k-th value L(k), where k is an integer bigger than 4 and read from a memory location M, and storing L(k) at memory location M. Use the instruction set in the Instruction Set Architecture described in Appendix A. (b) Consider a pipelined processor, where the pipeline stages are those described in the appendix. Describe what happens in the pipeline stages for the various types (data movement, data processing, control) of instructions. (c) Show the execution of your program on the above pipelined processor for k= 6 by drawing a diagram. Assume that the fetched and decoded instructions are stored in an instruction window IW with unlimited capacity (and so you can store any number of instruction in the IW). Explain where and why delay slots appear. We present a list of instructions typical of a RISC (reduced instruction set computer) machine. In data-movement and control instructions, the addresses may be immediate #X, direct (memory) M, indirect (memory) [M], register r, or register indirect [r] addresses. Data-processing instructions use immediate or register addressing. PC is the programme counter and a >[s] c) a >[u] c) PC C PC = c Note: Here b >>[s] c denotes the arithmetical shift of b to the right by c positions, and b >>[u] c denotes the logical shift of b to the right by c positions. A.2 The pipeline We will use a five-stage pipeline: IF (instruction fetch), ID (instruction decode), RR (register read), EX (execute instruction), WB (write back result into register). Note that for some instructions (e.g., LOAD r, #x) some of the pipeline stages (e.g., RR) are not needed
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


