Question: Assignment 2 from Chapter 4 is the second image. Thanks Assignment 4. Using the template provided in Table 9-1 in your textbook, develop documentation for
 Assignment 2 from Chapter 4 is the second image. Thanks
Assignment 2 from Chapter 4 is the second image. Thanks
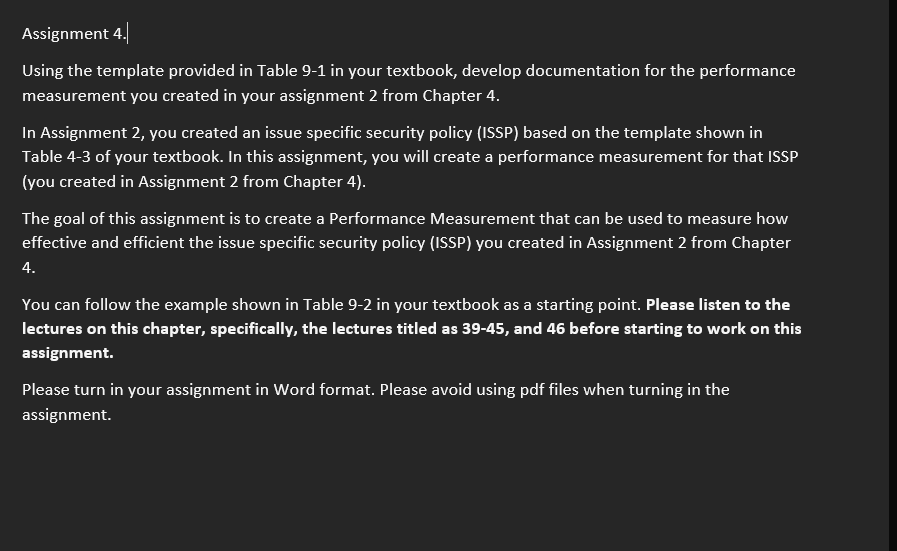
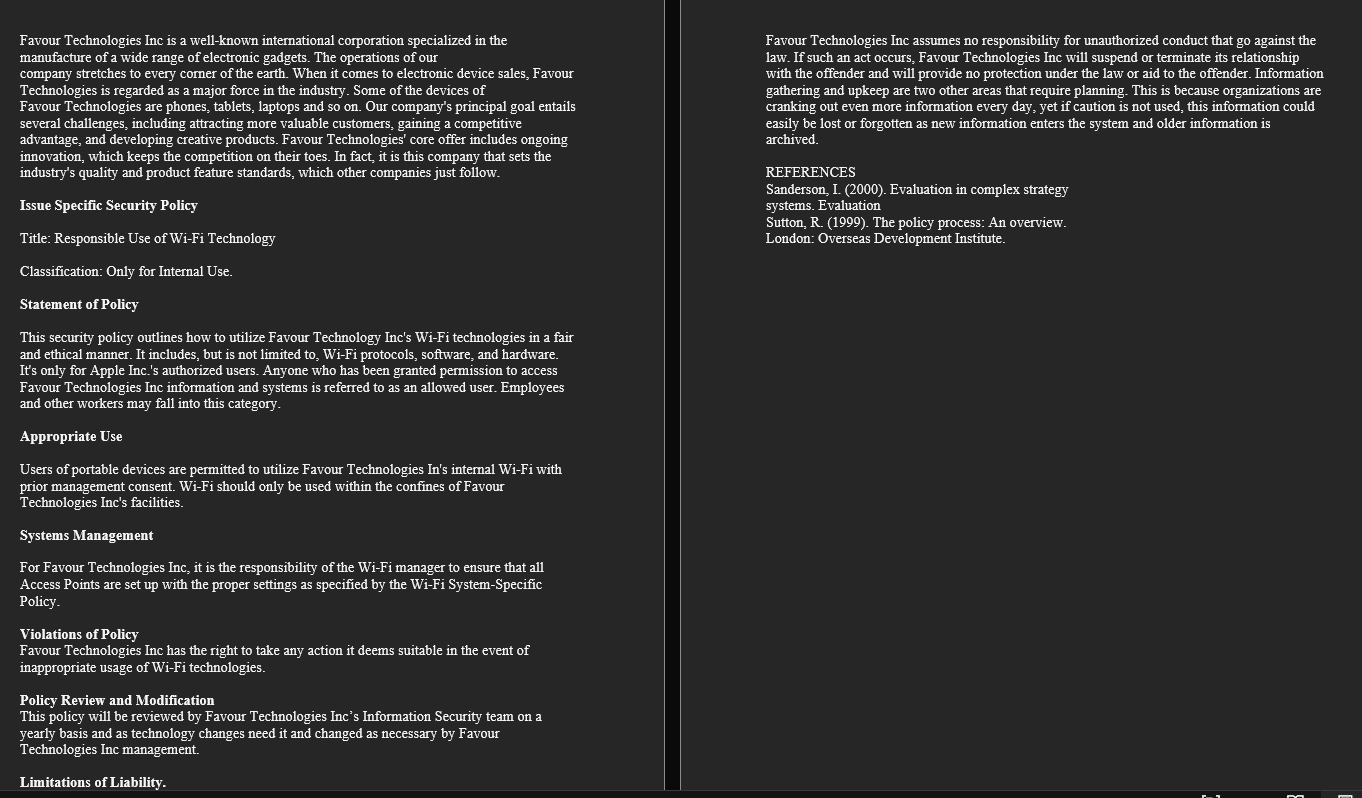
Assignment 4. Using the template provided in Table 9-1 in your textbook, develop documentation for the performance measurement you created in your assignment 2 from Chapter 4. In Assignment 2, you created an issue specific security policy (ISSP) based on the template shown in Table 4-3 of your textbook. In this assignment, you will create a performance measurement for that ISSP (you created in Assignment 2 from Chapter 4). The goal of this assignment is to create a Performance Measurement that can be used to measure how effective and efficient the issue specific security policy (ISSP) you created in Assignment 2 from Chapter 4. You can follow the example shown in Table 9-2 in your textbook as a starting point. Please listen to the lectures on this chapter, specifically, the lectures titled as 39-45, and 46 before starting to work on this assignment. Please turn in your assignment in Word format. Please avoid using pdf files when turning in the assignment Favour Technologies Inc is a well-known international corporation specialized in the manufacture of a wide range of electronic gadgets. The operations of our company stretches to every corner of the earth. When it comes to electronic device sales, Favour Technologies is regarded as a major force in the industry. Some of the devices of Favour Technologies are phones, tablets, laptops and so on. Our company's principal goal entails several challenges, including attracting more valuable customers, gaining a competitive advantage, and developing creative products. Favour Technologies' core offer includes ongoing innovation, which keeps the competition on their toes. In fact, it is this company that sets the industry's quality and product feature standards, which other companies just follow. Favour Technologies Inc assumes no responsibility for unauthorized conduct that go against the law. If such an act occurs, Favour Technologies Inc will suspend or terminate its relationship with the offender and will provide no protection under the law or aid to the offender. Information gathering and upkeep are two other areas that require planning. This is because organizations are cranking out even more information every day, yet if caution is not used, this information could easily be lost or forgotten as new information enters the system and older information is archived. Issue Specific Security Policy REFERENCES Sanderson, I. (2000). Evaluation in complex strategy systems. Evaluation Sutton, R. (1999). The policy process: An overview. London: Overseas Development Institute. Title: Responsible Use of Wi-Fi Technology Classification: Only for Internal Use. Statement of Policy This security policy outlines how to utilize Favour Technology Inc's Wi-Fi technologies in a fair and ethical manner. It includes, but is not limited to, Wi-Fi protocols, software, and hardware. It's only for Apple Inc.'s authorized users. Anyone who has been granted permission to access Favour Technologies Inc information and systems is referred to as an allowed user. Employees and other workers may fall into this category. Appropriate Use Users of portable devices are permitted to utilize Favour Technologies In's internal Wi-Fi with prior management consent. Wi-Fi should only be used within the confines of Favour Technologies Inc's facilities. Systems Management For Favour Technologies Inc, it is the responsibility of the Wi-Fi manager to ensure that all Access Points are set up with the proper settings as specified by the Wi-Fi System-Specific Policy. Violations of Policy Favour Technologies Inc has the right to take any action it deems suitable in the event of inappropriate usage of Wi-Fi technologies. Policy Review and Modification This policy will be reviewed by Favour Technologies Inc's Information Security team on a yearly basis and as technology changes need it and changed as necessary by Favour Technologies Inc management. Limitations of Liability. M. Assignment 4. Using the template provided in Table 9-1 in your textbook, develop documentation for the performance measurement you created in your assignment 2 from Chapter 4. In Assignment 2, you created an issue specific security policy (ISSP) based on the template shown in Table 4-3 of your textbook. In this assignment, you will create a performance measurement for that ISSP (you created in Assignment 2 from Chapter 4). The goal of this assignment is to create a Performance Measurement that can be used to measure how effective and efficient the issue specific security policy (ISSP) you created in Assignment 2 from Chapter 4. You can follow the example shown in Table 9-2 in your textbook as a starting point. Please listen to the lectures on this chapter, specifically, the lectures titled as 39-45, and 46 before starting to work on this assignment. Please turn in your assignment in Word format. Please avoid using pdf files when turning in the assignment Favour Technologies Inc is a well-known international corporation specialized in the manufacture of a wide range of electronic gadgets. The operations of our company stretches to every corner of the earth. When it comes to electronic device sales, Favour Technologies is regarded as a major force in the industry. Some of the devices of Favour Technologies are phones, tablets, laptops and so on. Our company's principal goal entails several challenges, including attracting more valuable customers, gaining a competitive advantage, and developing creative products. Favour Technologies' core offer includes ongoing innovation, which keeps the competition on their toes. In fact, it is this company that sets the industry's quality and product feature standards, which other companies just follow. Favour Technologies Inc assumes no responsibility for unauthorized conduct that go against the law. If such an act occurs, Favour Technologies Inc will suspend or terminate its relationship with the offender and will provide no protection under the law or aid to the offender. Information gathering and upkeep are two other areas that require planning. This is because organizations are cranking out even more information every day, yet if caution is not used, this information could easily be lost or forgotten as new information enters the system and older information is archived. Issue Specific Security Policy REFERENCES Sanderson, I. (2000). Evaluation in complex strategy systems. Evaluation Sutton, R. (1999). The policy process: An overview. London: Overseas Development Institute. Title: Responsible Use of Wi-Fi Technology Classification: Only for Internal Use. Statement of Policy This security policy outlines how to utilize Favour Technology Inc's Wi-Fi technologies in a fair and ethical manner. It includes, but is not limited to, Wi-Fi protocols, software, and hardware. It's only for Apple Inc.'s authorized users. Anyone who has been granted permission to access Favour Technologies Inc information and systems is referred to as an allowed user. Employees and other workers may fall into this category. Appropriate Use Users of portable devices are permitted to utilize Favour Technologies In's internal Wi-Fi with prior management consent. Wi-Fi should only be used within the confines of Favour Technologies Inc's facilities. Systems Management For Favour Technologies Inc, it is the responsibility of the Wi-Fi manager to ensure that all Access Points are set up with the proper settings as specified by the Wi-Fi System-Specific Policy. Violations of Policy Favour Technologies Inc has the right to take any action it deems suitable in the event of inappropriate usage of Wi-Fi technologies. Policy Review and Modification This policy will be reviewed by Favour Technologies Inc's Information Security team on a yearly basis and as technology changes need it and changed as necessary by Favour Technologies Inc management. Limitations of Liability. M
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


