Question: Assume that you are choosing an algorithm to provide encryption method, but an attacker exploits the characteristics of the algorithm to attempt to deduce a
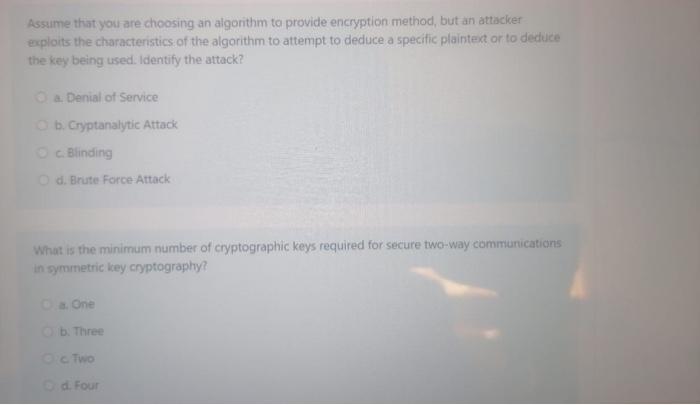
Assume that you are choosing an algorithm to provide encryption method, but an attacker exploits the characteristics of the algorithm to attempt to deduce a specific plaintext or to deduce the key being used. Identify the attack? a Denial of Service b. Cryptanalytic Attack Blinding d. Brute Force Attack What is the minimum number of cryptographic keys required for secure two-way communications in symmetric key cryptography? oa. One b. Three O c Two od Four
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


