Question: B1. Given four types of assets (data, hardware, software, and communication), many threat types (interception, interruption, modification, and fabrication) can cause a breach of security
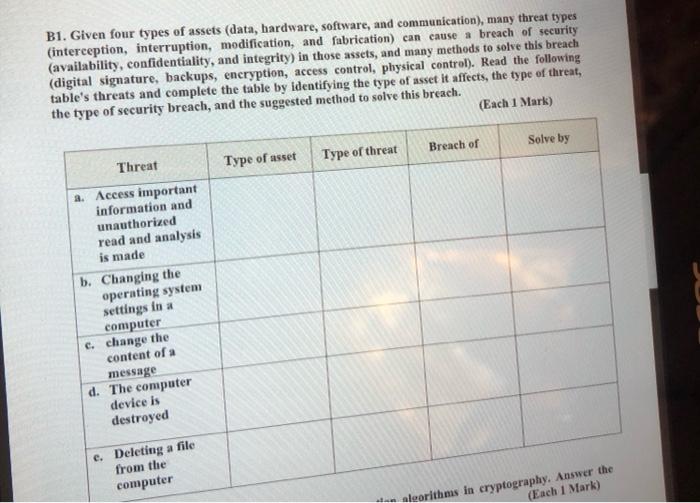
B1. Given four types of assets (data, hardware, software, and communication), many threat types (interception, interruption, modification, and fabrication) can cause a breach of security (availability, confidentiality, and integrity) in those assets, and many methods to solve this breach (digital signature, backups, encryption, access control, physical control). Read the following table's threats and complete the table by identifying the type of asset it affects, the type of threat, the type of security breach, and the suggested method to solve this breach. (Each 1 Mark) Solve by Breach of Type of asset Type of threat Threat a. Access important information and unauthorized read and analysis is made b. Changing the operating system settings in a computer c. change the content of a message d. The computer device is destroyed e. Deleting a file from the computer algorithms in cryptography. Answer the (Each 1 Mark)
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


