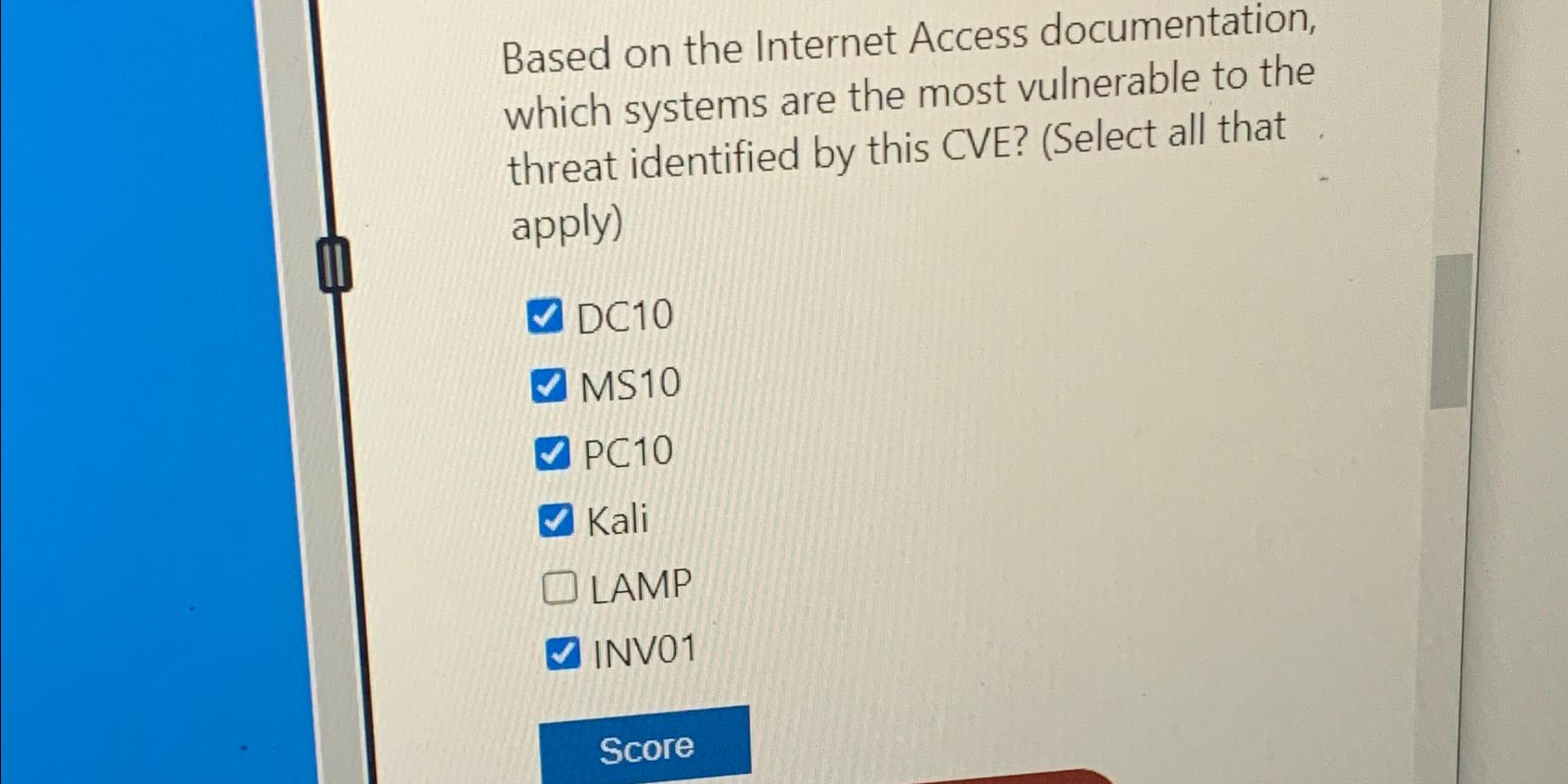
Question: Based on the Internet Access documentation, which systems are the most vulnerable to the threat identified by this CVE? ( Select all that apply )
Based on the Internet Access documentation, which systems are the most vulnerable to the threat identified by this CVE? Select all that apply
DC
MS
PC
Kali
LAMP
INV
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


