Question: Birthday collision attack implementation Implement the given algorithm in C/C++ or Python to search for collisions in a toy example of a cryptographic hash function
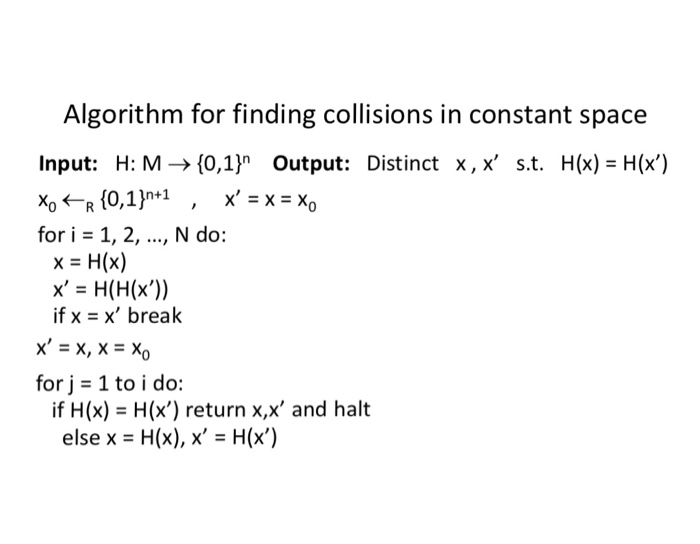
Algorithm for finding collisions in constant space input: H: M->{0,1)n Output: Distinct x, x, st. H(x)-H(x) for i = 1, 2, , N do: x = H(x) x' = H(H(x)) if x = x' break x'=x, x=x0 for j 1 to i do: if H(x) -H(x) return x,x' and halt else x- H(x), x' - H(x') Algorithm for finding collisions in constant space input: H: M->{0,1)n Output: Distinct x, x, st. H(x)-H(x) for i = 1, 2, , N do: x = H(x) x' = H(H(x)) if x = x' break x'=x, x=x0 for j 1 to i do: if H(x) -H(x) return x,x' and halt else x- H(x), x' - H(x')
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


