Question: Book: Database Security and Auditing: Protecting Data Integrity and Accessibility Case 5-2 Application Security with Oracle You were hired by Acme Telecommunication Systems (ATS) to
Book: Database Security and Auditing: Protecting Data Integrity and Accessibility
Case 5-2 Application Security with Oracle
You were hired by Acme Telecommunication Systems (ATS) to implement a number of security requirements. Provide the architecture of the application security model you select and the steps to implement it. The application has the following modules:
- Account Maintenance
- Call Records
- Transactions
- Call Monitoring
- Backup and Restore
- Security
The following users will be accessing the system:
- Sammy Bright
- Tom Lord
- Linda Glass
- Joan Knight
- James Howell
- Dennis Wright
- Ray Stevenson
- Phil Magnet
- Kate Davis
(Picture is additional information to the question)
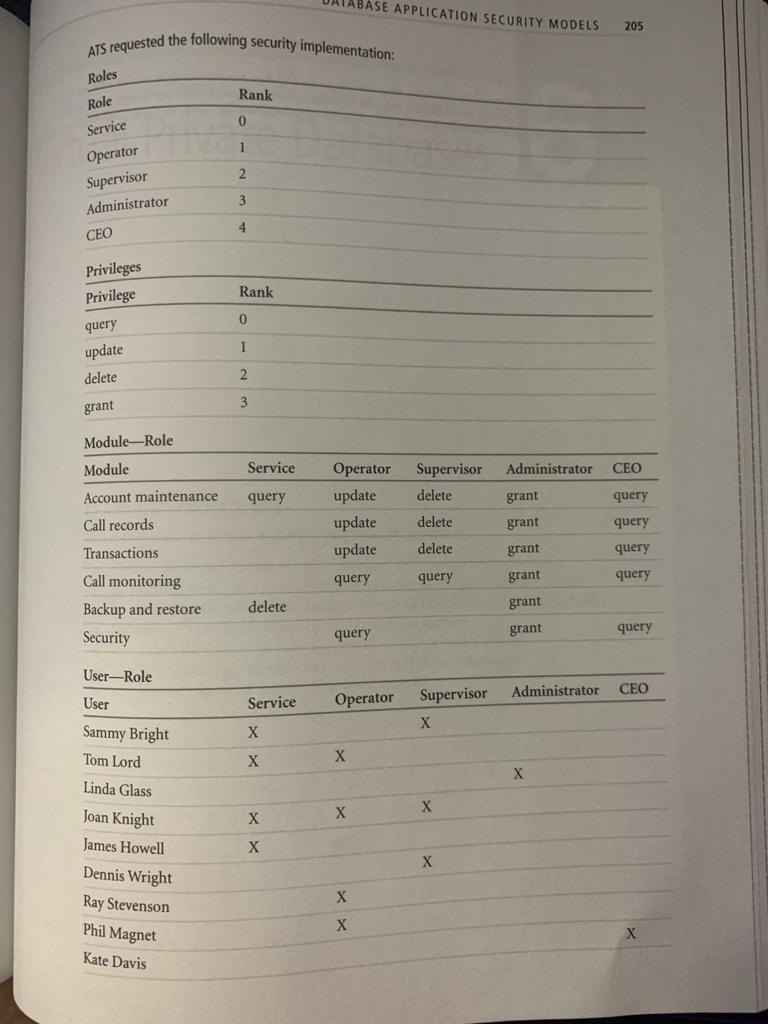
ATS requested the following security implementation: ABASE APPLICATION SECURITY MODELS 205 Roles Rank Role 0 Service 1 2 Operator Supervisor Administrator CEO 3 4 Rank 0 Privileges Privilege query update delete grant 1 2 3 Module-Role Module Service Administrator CEO Supervisor delete Account maintenance query grant query Operator update update update query delete grant query delete grant Call records Transactions Call monitoring Backup and restore Security query query grant query delete grant query grant query User-Role Administrator CEO User Service Operator Supervisor X X X Sammy Bright Tom Lord Linda Glass Joan Knight James Howell Dennis Wright Ray Stevenson Phil Magnet Kate Davis
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


