Question: Brute - force attacks Tasks Deploy Your Authentication Mechanism. I prepared a basic login and authentication with php , then connected it to mysql through
Bruteforce attacks
Tasks
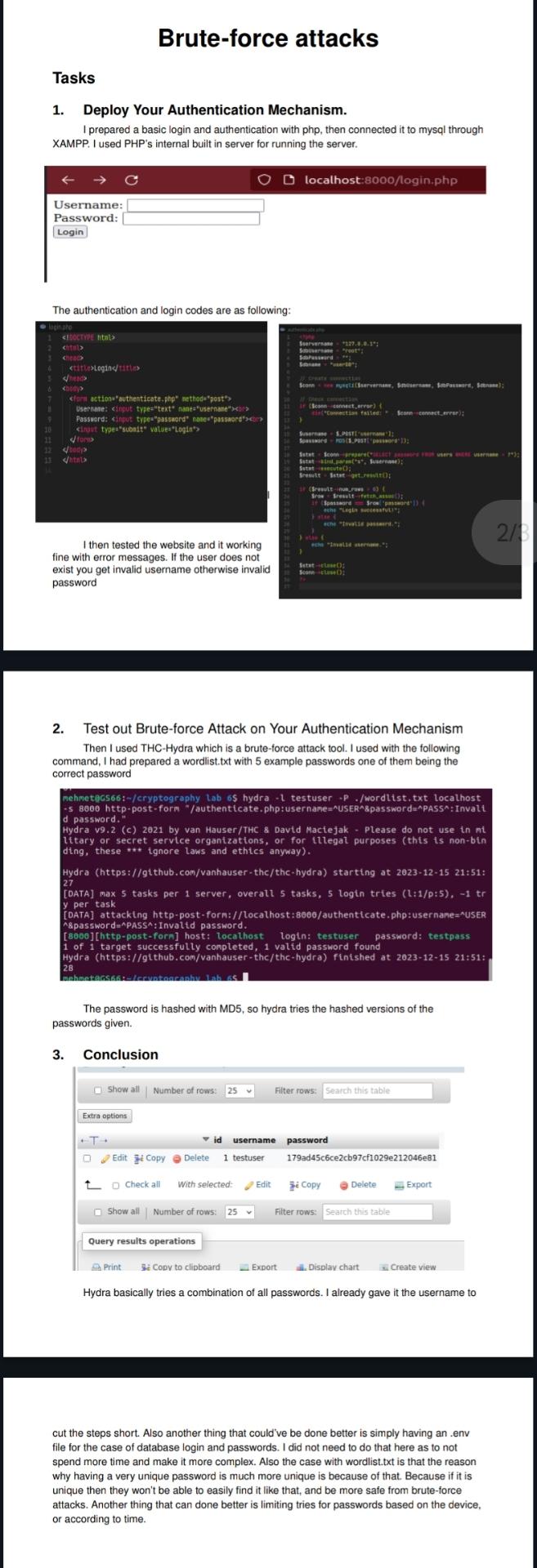
Deploy Your Authentication Mechanism.
I prepared a basic login and authentication with php then connected it to mysql through XAMPP. I used PHPs internal built in server for running the server.
The authentication and login codes are as following: exist you get invalid username otherwise invalid password
Test out Bruteforce Attack on Your Authentication Mechanism Then I used THCHydra which is a bruteforce attack tool. I used with the following command, I had prepared a wordlist.txt with example passwords one of them being the correct password
The password is hashed with MD so hydra tries the hashed versions of the passwords given.
Conclusion
Hydra basically tries a combination of all passwords. I already gave it the username to
cut the steps short. Also another thing that could've be done better is simply having an env file for the case of database login and passwords. I did not need to do that here as to not spend more time and make it more complex. Also the case with wordlist.txt is that the reason why having a very unique password is much more unique is because of that. Because if it is unique then they won't be able to easily find it like that, and be more safe from bruteforce attacks. Another thing that can done better is limiting tries for passwords based on the device, or according to time.
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


