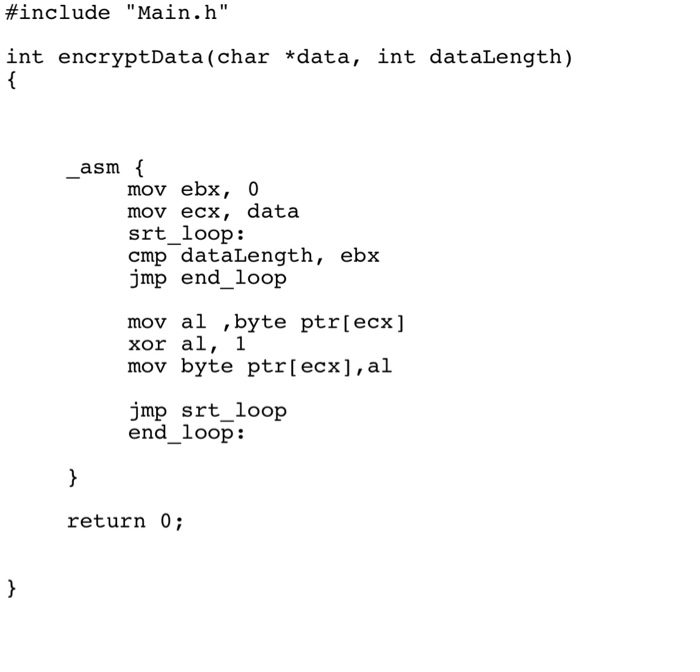
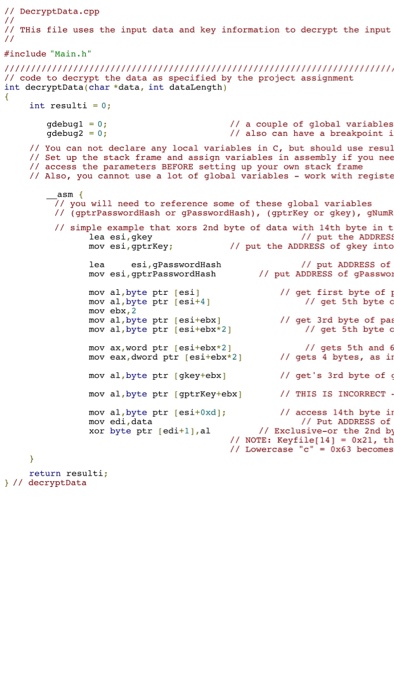
Question: C++ code what I need is decryption(must loop through the encrypted file and again xor every byte with a one ) basically the opposite of
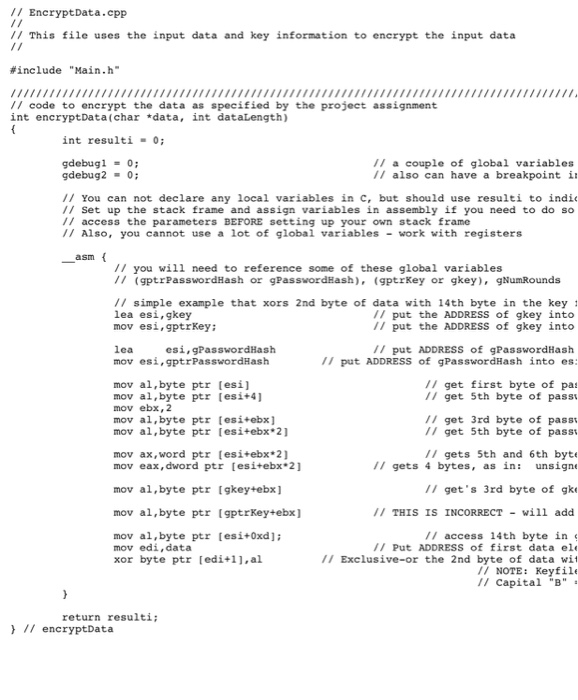
/I EncryptData.cpp // This file uses the input data and key information to encrypt the input data #include "Main"h" /I code to encrypt the data as specified by the project assignment int encryptData(chardata, int dataLength) int resulti-0; gdebug 1 = 0; gdebug2-0 // a couple of global variables // also can have a breakpoint i# // You can not declare any local variables in C, but should use resulti to indic /I Set up the stack frame and assign variables in assembly if you need to do so /I access the parameters BEFORE setting up your own stack frame // Also, you cannot use a lot of global variables - work with registers asm // you will need to reference some of these global variables // (gptrPasswordHash or gPasswordHash), (gptrKey or gkey), gNumRounds // simple example that xors 2nd byte of data with 14th byte in the key 1 lea esi,gkey mov esi,gptrkey; // put the ADDRESS of gkey into // put the ADDRESS of gkey into ca esi,gPasswordHash /I put ADDRESS of gPasswordHash mov esi,gptrPasswordHash // put ADDRESS of gPasswordHash into es mov al,byte ptr esi] mov al,byte ptr esit4] mov ebx,2 mov al,byte ptr esi+ebx] mov al,byte ptr esitebx 2] /I get first byte of pas // get 5th byte of pass /I get 3rd byte of pass /I get 5th byte of passt mov ax,word ptr esi+ebx 2) mov eax, dword ptr [esitebx 2 // gets 5th and 6th byte // gets 4 bytes, as in: unsigne mov al,byte ptr [gkey+ebx] // get's 3rd byte of gk mov al,byte ptr gptrKey+ebx /I THIS IS INCORRECT will add /I access 14th byte in mov al,byte ptr esit0xdl; mov edi,data xor byte ptr [edi+i],al /I Put ADDRESS of first data el /I Exclusive-or the 2nd byte of data wit NOTE: Keyfile // capital "B" return resulti I encryptData
Step by Step Solution
There are 3 Steps involved in it
To decrypt the data that was encrypted using XOR with 1 for every byte youll need to apply the same ... View full answer

Get step-by-step solutions from verified subject matter experts


