Question: c. Vulnerability valuation - Determine the numeric value of identified assets - Use personal judgment - Keep mission of the entity in mind Risk Asset
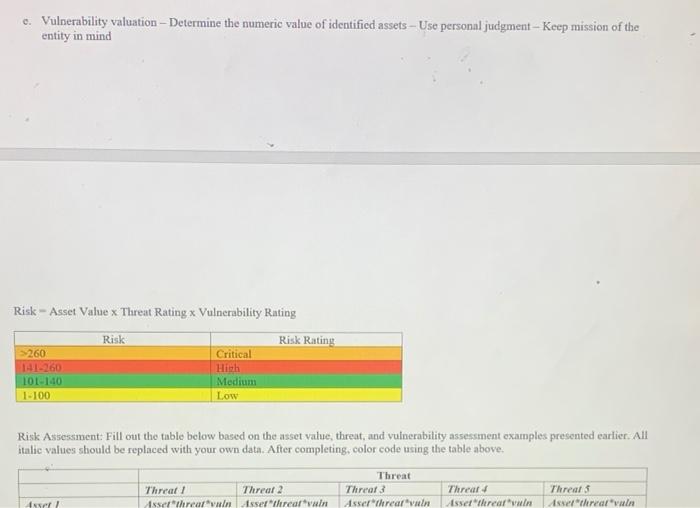
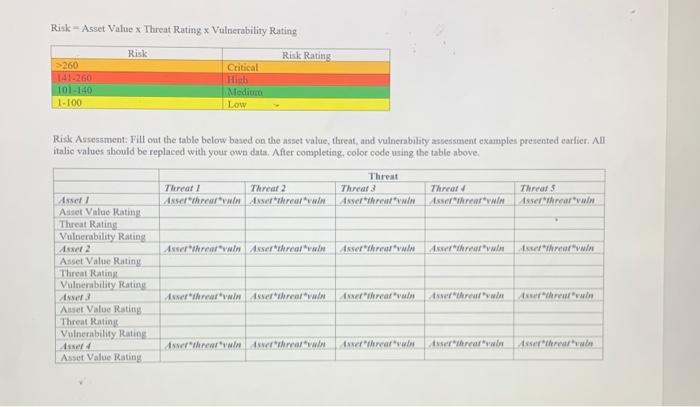
c. Vulnerability valuation - Determine the numeric value of identified assets - Use personal judgment - Keep mission of the entity in mind Risk Asset Value x Threat Rating x Vulnerability Rating X Risk Risk Rating 260 Critical 141-260 Hitch 101-140 Medium 1-100 Low Risk Assessment: Fill out the table below based on the asset value, threat, and vulnerability assessment examples presented earlier. All Italic values should be replaced with your own data. After completing, color code using the table above. Threat! Althrear win Threat 2 Isser threar win Threat Threat Asserthrear vain Threat Isselthrear win Threats Asselthreat'vuln Ayol Risk Asset Value x Threat Rating x Vulnerability Rating Risk Risk Rating Critical >260 141-260 10140 1-100 Hib Medium Low Risk Assessment: Fill out the table below based on the asset value, tareat, and vulnerability assessment examples presented earlier. All italic values should be replaced with your own data. After completing, color code using the table above Threat Threat / Threar 2 Threat 3 Threat Threats Asset! Asser threar winxserthreat Assertralin Assalari Asselthreat Asset Value Rating Threat Rating Vulnerability Rating Axel 2 Assortearwin Asser threat Asserthur Ashraf Esselthrear win Asset Value Rating Threat Rating Vulnerability Rating ter Assef "Marwi Asserthreadwin ferrari serhead arthrall Aliset Value Rating Threat Rating Vulnerability Rating Asset wherwinterthawin real'w Asselthrear win Asserter Asset Value Rating c. Vulnerability valuation - Determine the numeric value of identified assets - Use personal judgment - Keep mission of the entity in mind Risk Asset Value x Threat Rating x Vulnerability Rating X Risk Risk Rating 260 Critical 141-260 Hitch 101-140 Medium 1-100 Low Risk Assessment: Fill out the table below based on the asset value, threat, and vulnerability assessment examples presented earlier. All Italic values should be replaced with your own data. After completing, color code using the table above. Threat! Althrear win Threat 2 Isser threar win Threat Threat Asserthrear vain Threat Isselthrear win Threats Asselthreat'vuln Ayol Risk Asset Value x Threat Rating x Vulnerability Rating Risk Risk Rating Critical >260 141-260 10140 1-100 Hib Medium Low Risk Assessment: Fill out the table below based on the asset value, tareat, and vulnerability assessment examples presented earlier. All italic values should be replaced with your own data. After completing, color code using the table above Threat Threat / Threar 2 Threat 3 Threat Threats Asset! Asser threar winxserthreat Assertralin Assalari Asselthreat Asset Value Rating Threat Rating Vulnerability Rating Axel 2 Assortearwin Asser threat Asserthur Ashraf Esselthrear win Asset Value Rating Threat Rating Vulnerability Rating ter Assef "Marwi Asserthreadwin ferrari serhead arthrall Aliset Value Rating Threat Rating Vulnerability Rating Asset wherwinterthawin real'w Asselthrear win Asserter Asset Value Rating
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


