Question: Capture 1: 1) Open the provided packet capture files using any tools you see fit(Wireshark/Network Miner/SNORT) 2) Perform an analysis on the captured traffic. Some
Capture 1:
1) Open the provided packet capture files using any tools you see fit(Wireshark/Network Miner/SNORT) 2) Perform an analysis on the captured traffic. Some things you should consider are the following(not all of these happened and may not be all inclusive either): a. How long did the session captures last? b. Can the packet captures be correlated? c. How many packets were captured in each session? d. How many bytes were captured? e. What protocols were observed? f. What does the office enclave look like? g. Is there any events that rise to the level of being classified as an event or even an attack? 3) What story do the capture files tell? 4) Run the capture files through SNORT. What alerts are triggered? 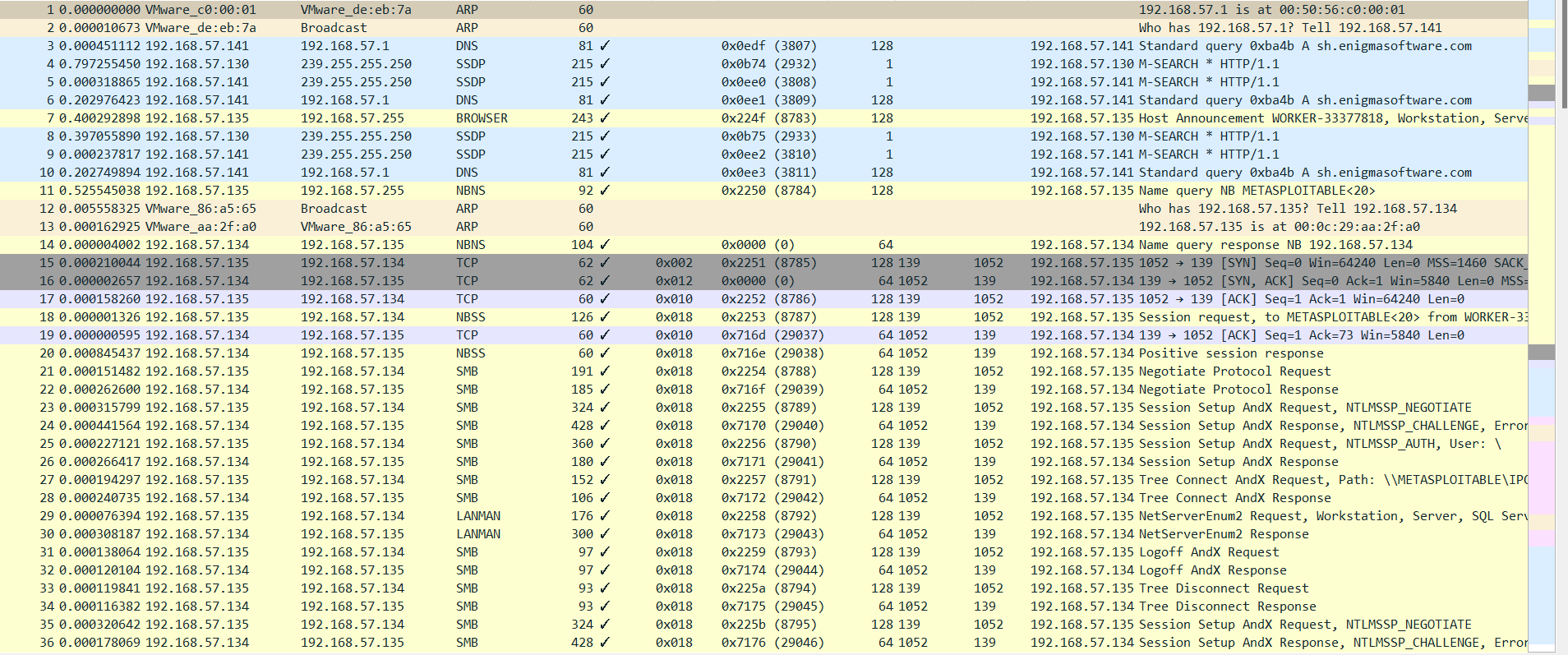
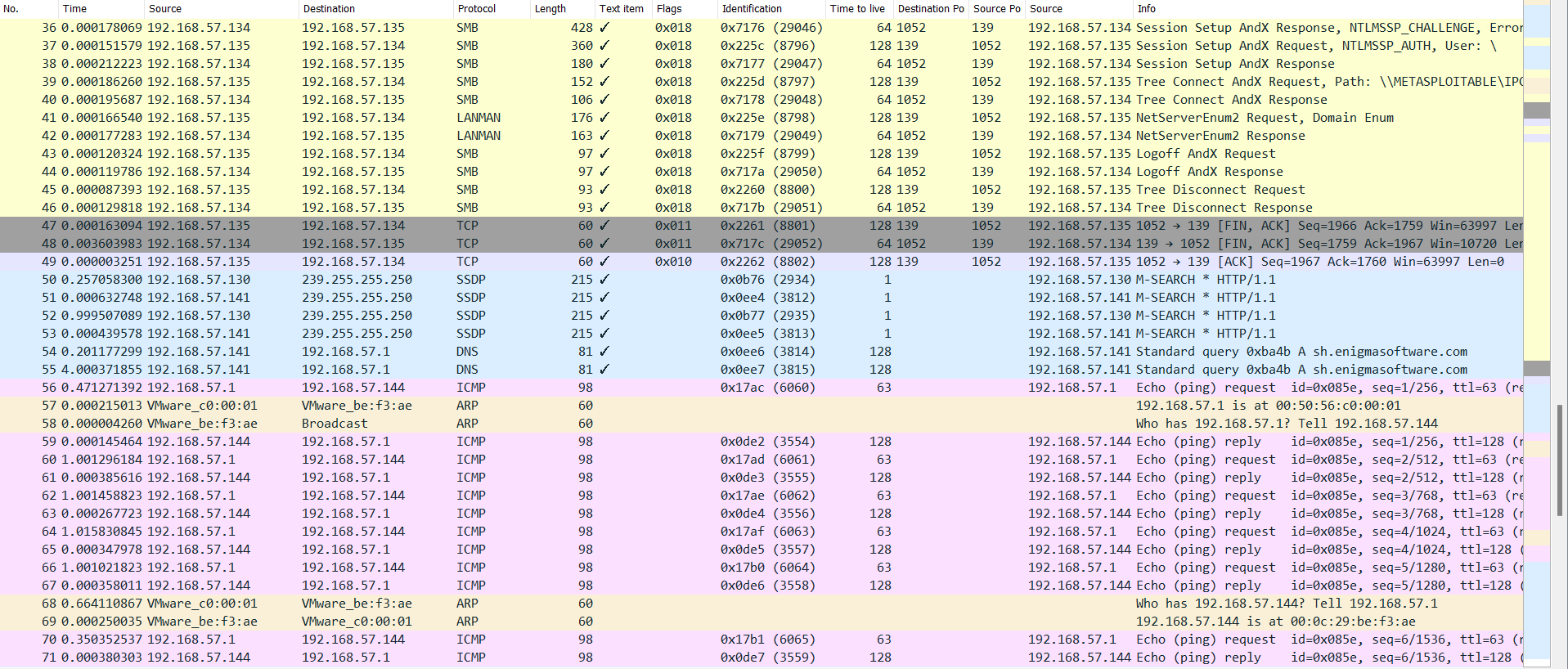
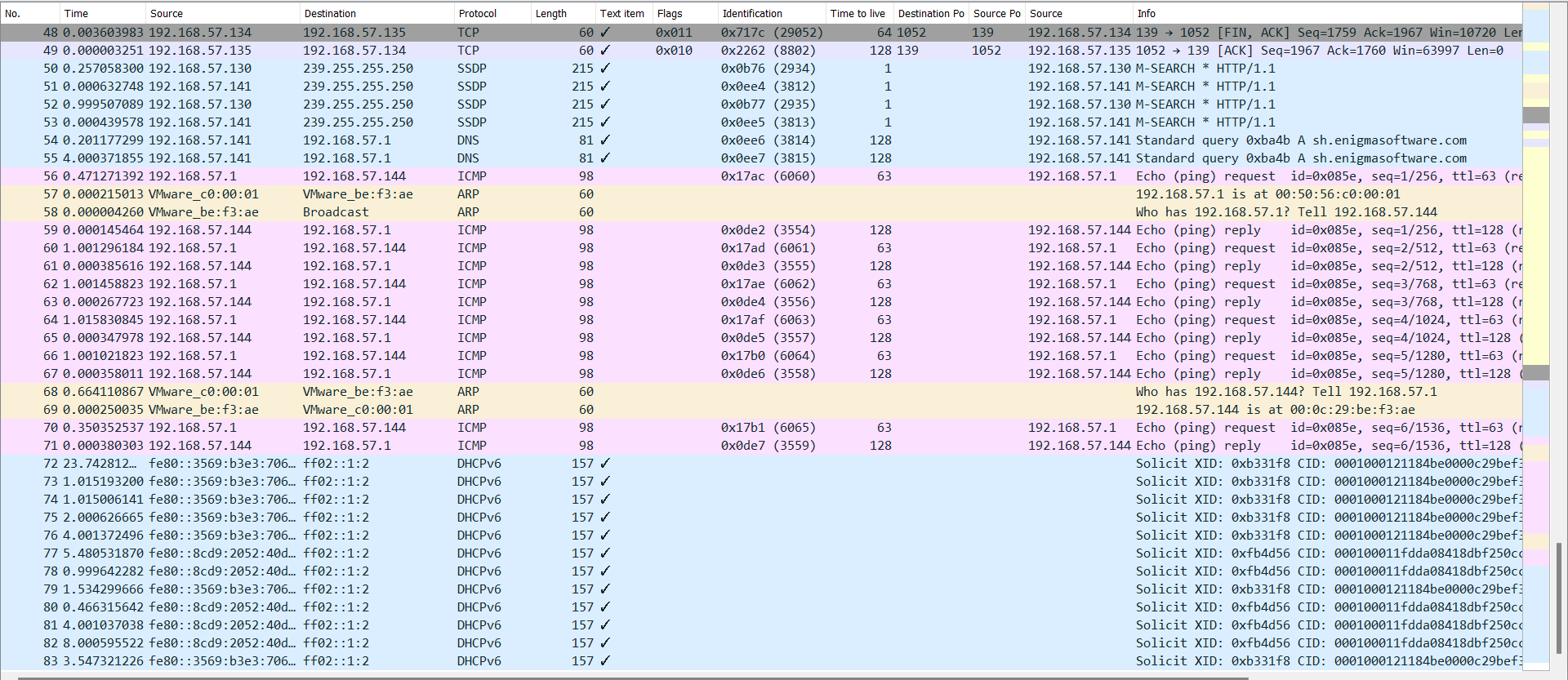
1 0.000000000 VMware_c0:00:01 2 0.000010673 VMware_de:eb:7a 3 0.000451112 192.168.57.141 40.797255450 192.168.57.130 5 0.000318865 192.168.57.141 6 0.202976423 192.168.57.141 7 0.400292898 192.168.57.135 8 0.397055890 192.168.57.130 9 0.000237817 192.168.57.141 10 0.202749894 192.168.57.141 11 0.525545038 192.168.57.135 12 0.005558325 VMware_86:a5:65 13 0.000162925 VMware_aa:2f:a0 14 0.000004002 192.168.57.134 15 0.000210044 192.168.57.135 16 0.000002657 192.168.57.134 17 0.000158260 192.168.57.135 18 0.000001326 192.168.57.135 19 0.000000595 192.168.57.134 20 0.000845437 192.168.57.134 21 0.000151482 192.168.57.135 22 0.000262600 192.168.57.134 23 0.000315799 192.168.57.135 24 0.000441564 192.168.57.134 25 0.000227121 192.168.57.135 26 0.000266417 192.168.57.134 27 0.000194297 192.168.57.135 28 0.000240735 192.168.57.134 29 0.000076394 192.168.57.135 30 0.000308187 192.168.57.134 31 0.000138064 192.168.57.135 32 0.000120104 192.168.57.134 33 0.000119841 192.168.57.135 34 0.000116382 192.168.57.134 35 0.000320642 192.168.57.135 36 0.000178069 192.168.57.134 VMware_de:eb:7a Broadcast 192.168.57.1 239.255.255.250 239.255.255.250 192.168.57.1 192.168.57.255 239.255.255.250 239.255.255.250 192.168.57.1 192.168.57.255 Broadcast VMware_86:a5:65 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.134 192.168.57.135 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 ARP ARP DNS SSDP SSDP DNS BROWSER SSDP SSDP DNS NBNS ARP ARP NBNS TCP TCP TCP NBSS TCP NBSS SMB SMB SMB SMB SMB SMB SMB SMB LANMAN LANMAN SMB SMB SMB SMB SMB SMB 60 60 81 215 215 81 243 215 215 81 92 60 60 104 62 62 60 126 60 60 191 185 324 428 360 180 152 106 176 300 97 97 93 93 324 428 0x002 0x012 0x010 0x018 0x010 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x0edf (3807) 0x0b74 (2932) 0x0ee0 (3808) 0x0ee1 (3809) 0x224f (8783) 0x0b75 (2933) 0x0ee2 (3810) 0x0ee3 (3811) 0x2250 (8784) 0x0000 (0) 0x2251 (8785) 0x0000 (0) 0x2252 (8786) 0x2253 (8787) 0x716d (29037) 0x716e (29038) 0x2254 (8788) 0x716f (29039) 0x2255 (8789) 0x7170 (29040) 0x2256 (8790) 0x7171 (29041) 0x2257 (8791) 0x7172 (29042) 0x2258 (8792) 0x7173 (29043) 0x2259 (8793) 0x7174 (29044) 0x225a (8794) 0x7175 (29045) 0x225b (8795) 0x7176 (29046) 128 1 1 128 128 1 1 128 128 64 128 139 64 1052 128 139 128 139 64 1052 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 1052 139 1052 1052 139 139 1052 139 1052 139 1052 139 1052 139 1052 139 1052 139 1052 139 1052 139 192.168.57.1 is at 00:50:56:c0:00:01 Who has 192.168.57.1? Tell 192.168.57.141 192.168.57.141 Standard query Oxba4b A sh.enigmasoftware.com 192.168.57.130 M-SEARCH * HTTP/1.1 192.168.57.141 M-SEARCH * HTTP/1.1 192.168.57.141 Standard query Oxba4b A sh.enigmasoftware.com 192.168.57.135 Host Announcement WORKER-33377818, Workstation, Serve 192.168.57.130 M-SEARCH * HTTP/1.1 192.168.57.141 M-SEARCH * HTTP/1.1 192.168.57.141 Standard query Oxba4b A sh.enigmasoftware.com 192.168.57.135 Name query NB METASPLOITABLE Who has 192.168.57.135? Tell 192.168.57.134 192.168.57.135 is at 00:0c:29:aa:2f:a0 192.168.57.134 Name query response NB 192.168.57.134 192.168.57.135 1052 139 [SYN] Seq=0 Win=64240 Len=0 MSS=1460 SACK 192.168.57.134 139 1052 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS= 192.168.57.135 1052 139 [ACK] Seq=1 Ack=1 Win=64240 Len=0 192.168.57.135 Session request, to METASPLOITABLE from WORKER-33 192.168.57.134 139 1052 [ACK] Seq=1 Ack=73 Win=5840 Len=0 192.168.57.134 Positive session response 192.168.57.135 Negotiate Protocol Request 192.168.57.134 Negotiate Protocol Response 192.168.57.135 Session Setup AndX Request, NTLMSSP_NEGOTIATE 192.168.57.134 Session Setup AndX Response, NTLMSSP_CHALLENGE, Error 192.168.57.135 Session Setup AndX Request, NTLMSSP_AUTH, User: \ 192.168.57.134 Session Setup AndX Response 192.168.57.135 Tree Connect AndX Request, Path: \\METASPLOITABLE\IP 192.168.57.134 Tree Connect AndX Response 192.168.57.135 NetServerEnum2 Request, Workstation, Server, SQL Serv 192.168.57.134 NetServer Enum2 Response 192.168.57.135 Logoff AndX Request 192.168.57.134 Logoff AndX Response 192.168.57.135 Tree Disconnect Request 192.168.57.134 Tree Disconnect Response 192.168.57.135 Session Setup AndX Request, NTLMSSP_NEGOTIATE 192.168.57.134 Session Setup AndX Response, NTLMSSP_CHALLENGE, Error No. Time Source 36 0.000178069 192.168.57.134 37 0.000151579 192.168.57.135 38 0.000212223 192.168.57.134 39 0.000186260 192.168.57.135 40 0.000195687 192.168.57.134 41 0.000166540 192.168.57.135 42 0.000177283 192.168.57.134 43 0.000120324 192.168.57.135 44 0.000119786 192.168.57.134 45 0.000087393 192.168.57.135 46 0.000129818 192.168.57.134 47 0.000163094 192.168.57.135 48 0.003603983 192.168.57.134 49 0.000003251 192.168.57.135 50 0.257058300 192.168.57.130 51 0.000632748 192.168.57.141 52 0.999507089 192.168.57.130 53 0.000439578 192.168.57.141 54 0.201177299 192.168.57.141 55 4.000371855 192.168.57.141 56 0.471271392 192.168.57.1 57 0.000215013 VMware_c0:00:01 58 0.000004260 VMware_be:f3:ae 59 0.000145464 192.168.57.144 60 1.001296184 192.168.57.1 61 0.000385616 192.168.57.144 62 1.001458823 192.168.57.1 63 0.000267723 192.168.57.144 64 1.015830845 192.168.57.1 65 0.000347978 192.168.57.144 66 1.001021823 192.168.57.1 67 0.000358011 192.168.57.144 68 0.664110867 VMware_c0:00:01 69 0.000250035 VMware_be:f3:ae 70 0.350352537 192.168.57.1 71 0.000380303 192.168.57.144 Destination 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 192.168.57.135 192.168.57.134 239.255.255.250 239.255.255.250 239.255.255.250 239.255.255.250 192.168.57.1 192.168.57.1 192.168.57.144 VMware_be:f3:ae Broadcast 192.168.57.1 192.168.57.144 192.168.57.1 192.168.57.144 192.168.57.1 192.168.57.144 192.168.57.1 192.168.57.144 192.168.57.1 VMware_be:f3:ae VMware_c0:00:01 192.168.57.144 192.168.57.1 Protocol SMB SMB SMB SMB SMB LANMAN LANMAN SMB SMB SMB SMB TCP TCP TCP SSDP SSDP SSDP SSDP DNS DNS ICMP ARP ARP ICMP ICMP ICMP ICMP ICMP ICMP ICMP ICMP ICMP ARP ARP ICMP ICMP Length Text item Flags 428 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x018 0x011 0x011 0x010 360 180 152 106 176 163 97 97 93 93 60 60 60 215 215 215 215 81 81 98 60 60 98 98 98 98 98 98 98 98 98 60 60 98 98 Identification 0x7176 (29046) 0x225c (8796) 0x7177 (29047) 0x225d (8797) 0x7178 (29048) 0x225e (8798) 0x7179 (29049) 0x225f (8799) 0x717a (29050) 0x2260 (8800) 0x717b (29051) 0x2261 (8801) 0x717c (29052) 0x2262 (8802) 0x0b76 (2934) 0x0ee4 (3812) 0x0b77 (2935) 0x0ee5 (3813) 0x0ee6 (3814) 0x0ee7 (3815) 0x17ac (6060) 0x0de2 (3554) 0x17ad (6061) 0x0de3 (3555) 0x17ae (6062) 0x0de4 (3556) 0x17af (6063) 0x0de5 (3557) 0x17b0 (6064) 0x0de6 (3558) 0x17b1 (6065) 0x0de7 (3559) Time to live Destination Po Source Po Source 139 1052 139 1052 139 1052 139 1052 139 1052 139 1052 139 1052 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 64 1052 128 139 1 1 1 1 128 128 63 128 63 128 63 128 63 128 63 128 63 128 Info 192.168.57.134 Session Setup AndX Response, NTLMSSP_CHALLENGE, Error 192.168.57.135 Session Setup AndX Request, NTLMSSP_AUTH, User: \ 192.168.57.134 Session Setup AndX Response 192.168.57.135 Tree Connect AndX Request, Path: \\METASPLOITABLE\IPC 192.168.57.134 Tree Connect AndX Response 192.168.57.135 NetServerEnum2 Request, Domain Enum 192.168.57.134 NetServerEnum2 Response 192.168.57.135 Logoff AndX Request 192.168.57.134 Logoff AndX Response 192.168.57.135 Tree Disconnect Request 192.168.57.134 Tree Disconnect Response 192.168.57.135 1052 139 [FIN, ACK] Seq=1966 Ack=1759 Win=63997 Ler 192.168.57.134 139 1052 [FIN, ACK] Seq=1759 Ack=1967 Win=10720 Ler 192.168.57.135 1052 139 [ACK] Seq=1967 Ack=1760 Win=63997 Len=0 192.168.57.130 M-SEARCH * HTTP/1.1 192.168.57.141 M-SEARCH * HTTP/1.1 192.168.57.130 M-SEARCH * HTTP/1.1 192.168.57.141 M-SEARCH * HTTP/1.1 192.168.57.141 Standard query Oxba4b A sh.enigmasoftware.com 192.168.57.141 Standard query Oxba4b A sh.enigmasoftware.com 192.168.57.1 Echo (ping) request id=0x085e, seq=1/256, ttl=63 (re 192.168.57.1 is at 00:50:56:c0:00:01 Who has 192.168.57.1? Tell 192.168.57.144 192.168.57.144 Echo (ping) reply id=0x085e, seq=1/256, ttl=128 (r 192.168.57.1 Echo (ping) request id=0x085e, seq=2/512, ttl=63 (re 192.168.57.144 Echo (ping) reply id=0x085e, seq=2/512, ttl=128 (r 192.168.57.1 Echo (ping) request id=0x085e, seq=3/768, ttl=63 (re 192.168.57.144 Echo (ping) reply id=0x085e, seq=3/768, ttl=128 (r 192.168.57.1 Echo (ping) request id=0x085e, seq=4/1024, ttl=63 (r 192.168.57.144 Echo (ping) reply id=0x085e, seq=4/1024, ttl=128 ( 192.168.57.1 Echo (ping) request id=0x085e, seq=5/1280, ttl=63 (r 192.168.57.144 Echo (ping) reply id=0x085e, seq=5/1280, ttl=128 Who has 192.168.57.144? Tell 192.168.57.1 192.168.57.144 is at 00:0c:29:be:f3:ae 192.168.57.1 Echo (ping) request id=0x085e, seq=6/1536, ttl=63 (r 192.168.57.144 Echo (ping) reply id=0x085e, seq=6/1536, ttl=128 No. Time Source Destination 192.168.57.135 192.168.57.134 239.255.255.250 239.255.255.250 239.255.255.250 239.255.255.250 192.168.57.1 192.168.57.1 192.168.57.144 VMware_be:f3:ae Broadcast 48 0.003603983 192.168.57.134 49 0.000003251 192.168.57.135 50 0.257058300 192.168.57.130 51 0.000632748 192.168.57.141 52 0.999507089 192.168.57.130 53 0.000439578 192.168.57.141 54 0.201177299 192.168.57.141 55 4.000371855 192.168.57.141 56 0.471271392 192.168.57.1 57 0.000215013 VMware_c0:00:01 58 0.000004260 VMware_be:f3:ae 59 0.000145464 192.168.57.144 60 1.001296184 192.168.57.1 61 0.000385616 192.168.57.144 62 1.001458823 192.168.57.1 63 0.000267723 192.168.57.144 64 1.015830845 192.168.57.1 65 0.000347978 192.168.57.144 66 1.001021823 192.168.57.1 67 0.000358011 192.168.57.144 68 0.664110867 VMware_c0:00:01 69 0.000250035 VMware_be:f3:ae 70 0.350352537 192.168.57.1 71 0.000380303 192.168.57.144 72 23.742812... fe80::3569:b3e3:706... ff02::1:2 73 1.015193200 fe80::3569:b3e3:706... ff02::1:2 74 1.015006141 fe80::3569:b3e3:706... ff02::1:2 75 2.000626665 fe80::3569:b3e3:706... ff02::1:2 76 4.001372496 fe80::3569:b3e3:706... ff02::1:2 77 5.480531870 fe80::8cd9:2052:40d... ff02::1:2 78 0.999642282 fe80::8cd9:2052:40d... ff02::1:2 79 1.534299666 fe80::3569:b3e3:706... ff02::1:2 80 0.466315642 fe80::8cd9:2052:40d... ff02::1:2 81 4.001037038 fe80::8cd9:2052:40d... ff02::1:2 82 8.000595522 fe80::8cd9:2052:40d... ff02::1:2 83 3.547321226 fe80::3569:b3e3:706... ff02::1:2 192.168.57.1 192.168.57.144 192.168.57.1 192.168.57.144 192.168.57.1 192.168.57.144 192.168.57.1 192.168.57.144 192.168.57.1 VMware_be:f3:ae VMware_c0:00:01 192.168.57.144 192.168.57.1 Protocol TCP TCP SSDP SSDP SSDP SSDP DNS DNS ICMP ARP ARP ICMP ICMP ICMP ICMP ICMP ICMP ICMP ICMP ICMP ARP ARP ICMP ICMP DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 DHCPv6 Length Text item Flags 0x011 0x010 60 60 215 215 215 215 81 81 98 60 60 98 98 98 98 98 98 98 98 98 60 60 98 98 157 157 157 157 157 157 157 157 157 157 157 157 Identification 0x717c (29052) 0x2262 (8802) 0x0b76 (2934) 0x0ee4 (3812) 0x0b77 (2935) 0x0ee5 (3813) 0x0ee6 (3814) 0x0ee7 (3815) 0x17ac (6060) 0x0de2 (3554) 0x17ad (6061) 0x0de3 (3555) 0x17ae (6062) 0x0de4 (3556) 0x17af (6063) 0x0de5 (3557) 0x17b0 (6064) 0x0de6 (3558) 0x17b1 (6065) 0x0de7 (3559) Time to live Destination Po Source Po Source 139 1052 64 1052 128 139 1 1 1 1 128 128 63 128 63 128 63 128 63 128 63 128 63 128 Info 192.168.57.134 139 1052 [FIN, ACK] Seq=1759 Ack=1967 Win=10720 Ler 192.168.57.135 1052 139 [ACK] Seq=1967 Ack=1760 Win=63997 Len=0 192.168.57.130 M-SEARCH * HTTP/1.1 192.168.57.141 M-SEARCH * HTTP/1.1 192.168.57.130 M-SEARCH * HTTP/1.1 192.168.57.141 M-SEARCH * HTTP/1.1 192.168.57.141 Standard query Oxba4b A sh.enigmasoftware.com 192.168.57.141 Standard query Oxba4b A sh.enigmasoftware.com 192.168.57.1 Echo (ping) request id=0x085e, seq=1/256, ttl=63 (re 192.168.57.1 is at 00:50:56:c0:00:01 192.168.57.144 Echo (ping) reply 192.168.57.1 Echo (ping) request 192.168.57.144 Echo (ping) reply 192.168.57.1 Echo (ping) request 192.168.57.144 Echo (ping) reply 192.168.57.1 Echo (ping) request 192.168.57.144 Echo (ping) reply 192.168.57.1 Echo (ping) request 192.168.57.144 Echo (ping) reply Who has 192.168.57.1? Tell 192.168.57.144 id=0x085e, seq=1/256, ttl=128 ( id=0x085e, seq=2/512, ttl=63 (re id=0x085e, seq=2/512, ttl=128 (r id=0x085e, seq=3/768, ttl=63 (re id=0x085e, seq=3/768, ttl=128 (r id=0x085e, seq=4/1024, ttl=63 (r id=0x085e, seq=4/1024, ttl=128 id=0x085e, seq=5/1280, ttl=63 (r id=0x085e, seq=5/1280, ttl=128 Who has 192.168.57.144? Tell 192.168.57.1 192.168.57.144 is at 00:0c:29:be:f3:ae 192.168.57.1 Echo (ping) request id=0x085e, seq=6/1536, ttl=63 (r 192.168.57.144 Echo (ping) reply id=0x085e, seq=6/1536, ttl=128 Solicit XID: 0xb331f8 CID: 0001000121184be0000c29bef3 Solicit XID: 0xb331f8 CID: 0001000121184be0000c29bef3 Solicit XID: 0xb331f8 CID: 0001000121184be0000c29bef Solicit XID: 0xb331f8 CID: 0001000121184be0000c29bef3 Solicit XID: 0xb331f8 CID: 0001000121184be0000c29bef: Solicit XID: 0xfb4d56 CID: 000100011fdda08418dbf250cc Solicit XID: 0xfb4d56 CID: 000100011fdda08418dbf250cc Solicit XID: 0xb331f8 CID: 0001000121184be0000c29bef3 Solicit XID: 0xfb4d56 CID: 000100011fdda08418dbf250cc Solicit XID: 0xfb4d56 CID: 000100011fdda08418dbf250cc Solicit XID: 0xfb4d56 CID: 000100011fdda08418dbf250cc Solicit XID: 0xb331f8 CID: 0001000121184be0000c29bef
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


