Question: Case 3 Using a Thematic Analysis Grid to help critically review the literature Sam's undergraduate research project required him to draw together aca- demic research
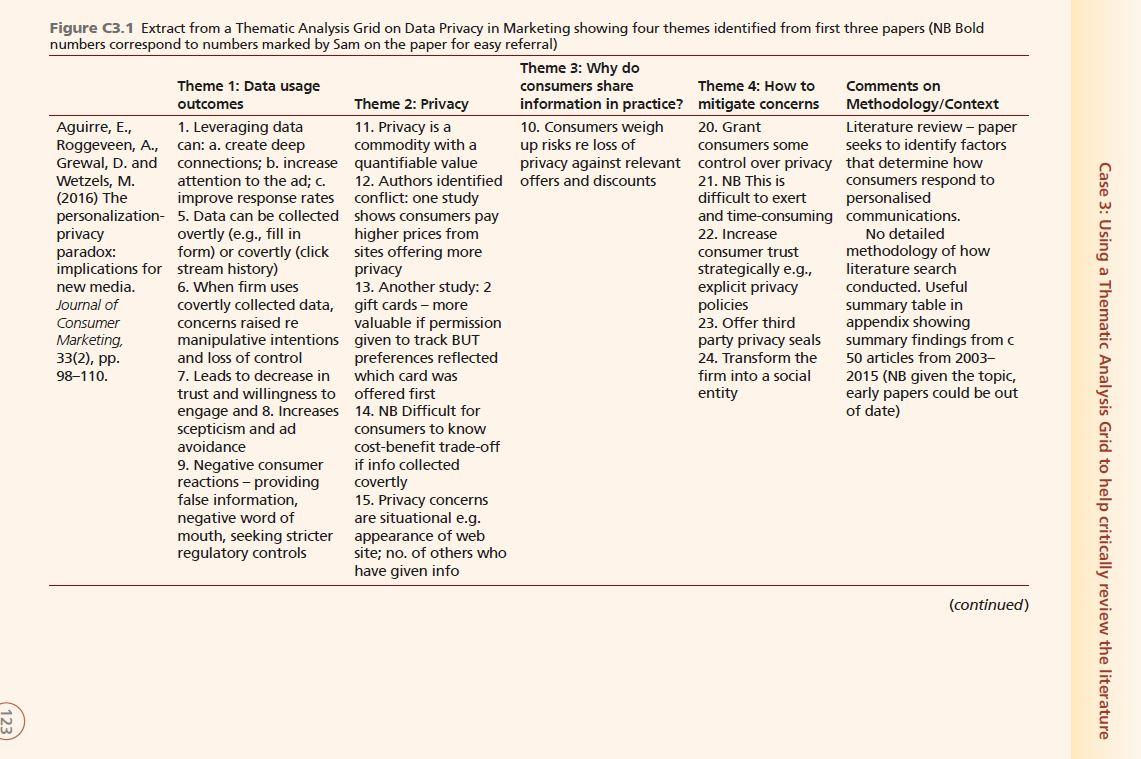
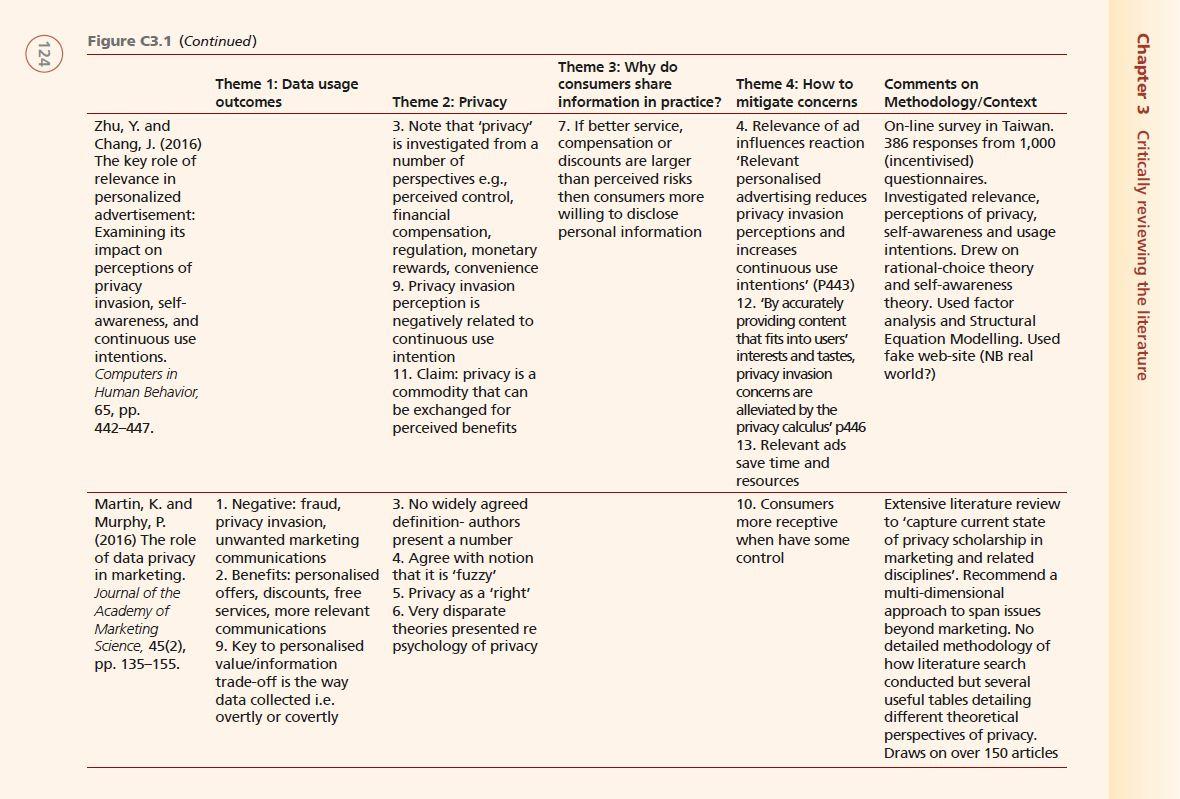

Case 3 Using a Thematic Analysis Grid to help critically review the literature Sam's undergraduate research project required him to draw together aca- demic research on data pri- vacy in marketing to develop practical recom- mendations for a company: an "industry briefing paper". At the heart of the project was a review of aca- demic literature Like many students at this stage in the project. Sam initially felt over- whelmed by the scale of the project. Where should he start? Should he read each paper then make notes? Should he use high- lighters or index cards? Once his tutor had outlined how to use the Thematic Analysis Grid (TAG). he felt much more relaxed. He realised he could address the daunting literature review as a series of more easily managed inter-linked tasks. This suited his busy lifestyle. It also reas- sured him that he would not repeat the mistake from a previous assignment that had been criticised for being too descriptive by simply summarising each artide and not drawing them together as a whole. He started by sorting the articles and book chapters he had found from his literature search into date order. As Sam began to read the first article he soon identified a potential theme: 'data usage out- comes", which became the first column of his grid. He marked a number 1 on his printed ver- sion of the paper and in the cell on his matrix, where he also wrote a very brief summary of the point being made. He then carried on reading and identified several additional themes. By using a numbering system on the grid and on his papers, he could easily return to the relevant section of the paper in the future. In the last column of the grid he noted the methodology used. It should be noted here that although Sam preferred to work with paper and pen, many of his colleagues prefer to use Excel or a table in Word to store their work. After about 90 minutes, Sam had five themes identified, each heading up a column of his TAG. In the next two articles, some of the themes were also discussed, in which case Sam simply documented them on the next row of his TAG in the same way. However, he also identified an additional three themes, so started three new columns. At the end of the afternoon, Sam had recorded all his reading to date in one place, cross- referenced to exactly where he had found the original discussion (Fig (3.1). The next three days were busy for Sam; he had an in-class test, a football final and a quick trip home for his sister's 21st birthday celebration. It was a week before Sam could continue, but then the TAG's value really became apparent. By reviewing his work so far, he was reminded about what he had read. He also began to see patterns emerging, for example, he privacy Figure C3.1 Extract from a Thematic Analysis Grid on Data Privacy in Marketing showing four themes identified from first three papers (NB Bold numbers correspond to numbers marked by Sam on the paper for easy referral) Theme 3: Why do Theme 1: Data usage consumers share Theme 4: How to Comments on outcomes Theme 2: Privacy information in practice? mitigate concerns Methodology/Context Aguirre, E., 1. Leveraging data 11. Privacy is a 10. Consumers weigh 20. Grant Literature review-paper Roggeveen, A., can: a. create deep commodity with a up risks re loss of consumers some seeks to identify factors Grewal, D. and connections; b. increase quantifiable value privacy against relevant control over privacy that determine how Wetzels, M. attention to the ad; C. 12. Authors identified offers and discounts 21. NB This is consumers respond to (2016) The improve response rates conflict: one study difficult to exert personalised personalization- 5. Data can be collected shows consumers pay and time-consuming communications. privacy overtly (e.g., fill in higher prices from 22. Increase No detailed paradox: form) or covertly (click sites offering more consumer trust methodology of how implications for stream history) strategically e.g., literature search new media. 6. When firm uses 13. Another study: 2 explicit privacy conducted. Useful Journal of covertly collected data, gift cards - more policies summary table in Consumer concerns raised re valuable if permission 23. Offer third appendix showing Marketing, manipulative intentions given to track BUT party privacy seals summary findings from and loss of control preferences reflected 24. Transform the 50 articles from 2003- 98-110. 7. Leads to decrease in which card was firm into a social 2015 (NB given the topic, trust and willingness to offered first entity early papers could be out engage and 8. Increases 14. NB Difficult for of date) scepticism and ad consumers to know avoidance cost-benefit trade-off 9. Negative consumer if info collected reactions - providing covertly false information, 15. Privacy concerns negative word of are situational e.g. mouth, seeking stricter appearance of web regulatory controls site; no. of others who have given info 33(2), pp. Case 3: Using a Thematic Analysis Grid to help critically review the literature (continued) N Chapter 3 Critically reviewing the literature Figure C3.1 (Continued) Theme 3: Why do Theme 1: Data usage consumers share Theme 4: How to Comments on outcomes Theme 2: Privacy information in practice? mitigate concerns Methodology/Context Zhu, Y. and 3. Note that 'privacy' 7. If better service, 4. Relevance of ad On-line survey in Taiwan. Chang, J. (2016) is investigated from a compensation or influences reaction 386 responses from 1,000 The key role of number of discounts are larger 'Relevant (incentivised) relevance in perspectives e.g., than perceived risks personalised questionnaires. personalized perceived control, then consumers more advertising reduces Investigated relevance, advertisement: financial willing to disclose privacy invasion perceptions of privacy, Examining its compensation, personal information perceptions and self-awareness and usage impact on regulation, monetary increases intentions. Drew on perceptions of rewards, convenience continuous use rational-choice theory privacy 9. Privacy invasion intentions' (P443) and self-awareness invasion, self- perception is 12. "By accurately theory. Used factor awareness, and negatively related to providing content analysis and Structural continuous use continuous use that fits into users' Equation Modelling. Used intentions. intention interests and tastes, fake web-site (NB real Computers in 11. Claim: privacy is a privacy invasion world?) Human Behavior, commodity that can concerns are be exchanged for alleviated by the 442-447. perceived benefits privacy calculus' p446 13. Relevant ads save time and resources Martin, K. and 1. Negative: fraud, 3. No widely agreed 10. Consumers Extensive literature review Murphy, P. privacy invasion, definition-authors more receptive to 'capture current state (2016) The role unwanted marketing present a number when have some of privacy scholarship in of data privacy communications 4. Agree with notion control marketing and related in marketing. 2. Benefits: personalised that it is 'fuzzy' disciplines'. Recommend a Journal of the offers, discounts, free 5. Privacy as a 'right' multi-dimensional Academy of services, more relevant 6. Very disparate approach to span issues Marketing communications theories presented re beyond marketing. No Science, 45(2), 9. Key to personalised psychology of privacy detailed methodology of pp. 135-155. value/information how literature search trade-off is the way conducted but several data collected i.e. useful tables detailing overtly or covertly different theoretical perspectives of privacy. Draws on over 150 articles 65, pp. saw that Aguirre et al. (2016) and Zhu and Chang (2016) both identified that privacy could be regarded as a commodity with a quantifiable value. However, Martin and Murphy (2017) sug- gested that there is no widely agreed definition. So who was correct? By reviewing his method- ology column, Sam could see that the reason for this discrepancy could be the scope of the studies: whilst Aguirre et al. (2016) and Zhu and Chang (2016) had focused on marketing and specifically marketing communications, the papers reviewed by Martin and Murphy (2017) covered a much wider range of disciplines including psychology. Without realising it, Sam was engaging in critical evaluation. On the grid, he subsequently added a series of arrows and link- ing lines to show where contradictions and consensus appeared. Sam continued constructing his TAG over four sessions, each separated by a gap of 2-5 days. Each time he reviewed his developing TAG, Sam felt more and more confident that he was seeing patterns emerge which would ensure that his project was based on themes rather than just summaries of each article or book chapter he had read. He was also able to use the literature he had read to justify why he believed one view was more credible than another. In other words, he had moved to proper critical evaluation of academic literature. Once Sam had completed all his reading he found the writing of the literature review was made straightfor- ward by using the themes as his sub-headings. Whilst he did not include every point on his TAG in his final work, he was confident that he had made informed decisions about the issues to include Questions 1 Do you think that Sam was being 'critical' in his approach to the academic literature on data privacy in marketing? Provide reasons for your answer. 2 How can Sam claim originality for a piece of work that relies so heavily on others' studies? 3 Why was it insufficient for Sam to simply present the results of a series of studies for this project? References Aguirre, E., Roggeveen, A., Grewal, D. and Wetzels, M. (2016) The personalization-privacy paradox: implications for new media. Journal of Consumer Marketing, 33(2), pp. 98-110. Martin, K. and Murphy, P. (2016) The role of data privacy in marketing. Journal of the Academy of Marketing Science, 45(2), pp. 135155. Zhu, Y. and Chang, J. (2016) The key role of relevance in personalized advertisement: Examining its impact on perceptions of privacy invasion, self-awareness, and continuous use intentions. Computers in Human Behavior, 65, pp. 442-447








