Question: CODED IN JAVA. USE HORNER'S HASHING RULE AS NOTED BELOW. 1 Objective Build a hash table that supports searching, insertion, deletion, printing, and integer hash
CODED IN JAVA. USE HORNER'S HASHING RULE AS NOTED BELOW.


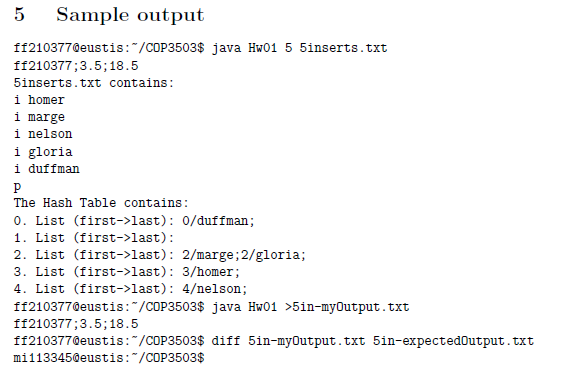
1 Objective Build a hash table that supports searching, insertion, deletion, printing, and integer hash key creation based on text or string input data. In the event of collisions, this separate chaining hash table will use a singly linked list to store duplicate keys 2 Requirements 1. Read the input file formatted as follows. The input file will contain at least one command per line, either insert, delete, search, print, or quit. These are defined in detail below. And if appropriate, a second parameter may be required. This string would contain a name, typically, less than seven characters. This name will be the data used to generate the hash. For example, one of the input files, named 5inserts.txt contains the following: i homer i marge i nelson i gloria i duffman 2. The specific commands are i for insert, d for delete s for search p for print, and q for quit (a) Insert The insert command uses the single character i as the command token. The com mand token will be followed by a single space, then the name which will be the characters used to calculate the hash key as defined below. The program will then insert the key and the data in the hash table. In the event that there is a duplicate key, the new key (and data) would be added to the appropriate slot's linked list. This command's success can be verified by using the print command (b) Delete The delete command uses the single character d as the command token. The command token will be followed by a single space, then the name which will
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


