Question: Complete the implementation of the AES algorithm operating in ECB mode, partially implemented by the attached code. The class must be capable of both encrypting
Complete the implementation of the AES algorithm operating in ECB mode, partially implemented by the attached code. The class must be capable of both encrypting and decrypting a plain text into a cipher text and back when the same key is passed to the encrypt and decrypt methods. AES is a block cipher that operates on bytes directly, so your code should be capable of encrypting any string of Unicode characters and decrypting back to identical Unicode.
import java.util.Arrays;
public class AES
public final Integer keyLengths ;
private int key;
private static final HashMap RC new HashMap;
static
RCputxL;
RCputxL;
RCputxL;
RCputxL;
RCputxL;
RCputxL;
RCputxL;
RCputxL;
RCputxBL;
RCputxL;
public AES
int index intMathrandom keyLengths.length;
genKeykeyLengthsindex;
public AESint keyLength
genKeykeyLength;
public int getRandomLength
int index intMathrandom keyLengths.length;
return keyLengthsindex;
private void genKeyint keyLength
key new intkeyLength ;
for int i ; i key.length; i
keyi randByte;
private int keySchedule
int N key.length ;
int R key.length ;
int WLen R;
int W new intWLen;
for int i ; i WLen; i
if i N
int word getKeyWordi;
for int j ; j ; j
Wij wordj;
else if i N && i N
int word new int;
for int j ; j ; j
wordj Wij;
word rotWordword;
for int j ; j ; j
wordj SBox.encryptwordj;
Wi WiN word RCgetiN
for int j ; j ; j
Wij WiNj wordj;
else if i N && N && i N
int word new int;
for int j ; j ; j
wordj Wij;
for int j ; j ; j
wordj SBox.encryptwordj;
for int j ; j ; j
Wij WiNj wordj;
else
int word new int;
for int j ; j ; j
wordj Wij;
for int j ; j ; j
Wij WiNj wordj;
return W;
private int getKeyWordint index
int word new int;
for int i ; i ; i
wordi keyindex i;
return word;
private int rotWordint word
int rot new int;
rot word;
rot word;
rot word;
rot word;
return rot;
prvate int randByte
return intMathrandom;
public String encryptString plaintext
return cipherplaintext true;
public String decryptString cipherText
return ciphercipherText false;
private String cipherString inText, boolean mode
char charArray inText.toCharArray;
char block new char;
StringBuilder outText new StringBuilder;
int index ;
whilegetBlockblock charArray, index
outText.appendcipherBlockblock mode;
index ;
return outText.toString;
private boolean getBlockchar block, char chars, int index
boolean lastBlock false;
for int col ; col ; col
for int row ; row ; row
if index chars.length
blockrowcolcharrandByte;
lastBlock true;
else
blockrowcol charsindex;
index;
return lastBlock;
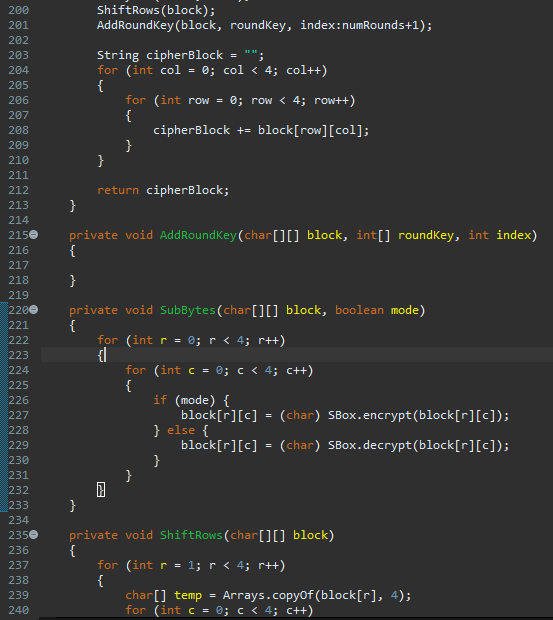
private String cipherBlockchar block, boolean mode
int roundKey keySchedule;
AddRoundKeyblock roundKey, ;
int numRounds key.length ;
for int i ; i numRounds; i
SubBytesblock mode;
ShiftRowsblock;
MixColumnsblock;
AddRoundKeyblock roundKey, index:i;
SubBytesblock mode
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


