Question: Computer Network Security 1) Look at figure 11.4. Note what servers are in the DMZ. Explain why they are in the DMZ area rather than
Computer Network Security

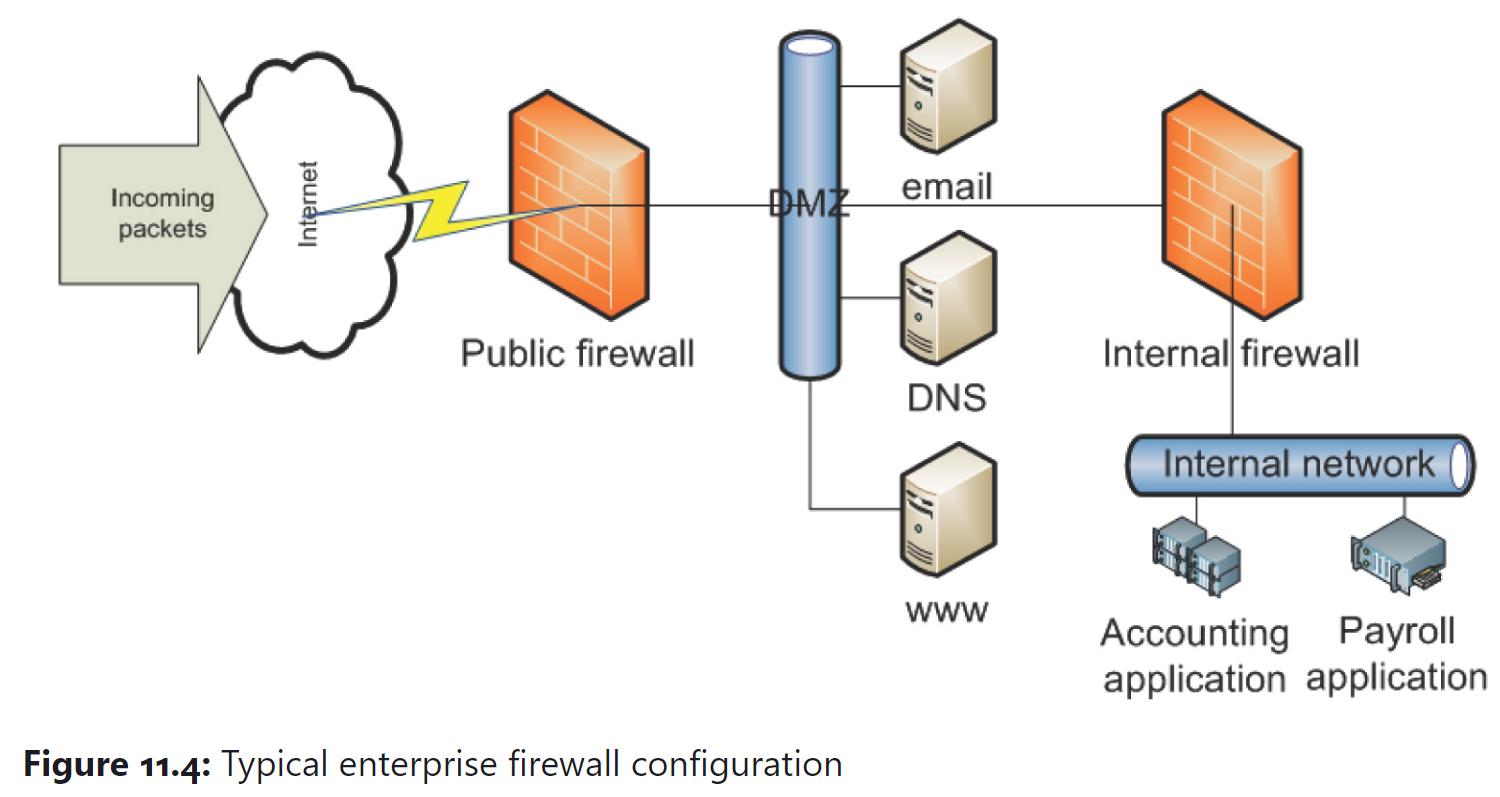



1) Look at figure 11.4. Note what servers are in the DMZ. Explain why they are in the DMZ area rather than on the internal network.
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


