Question: Below is the assembly for a function getbuf2 that is very similar to the getbuf function from the attacklab. It also calls gets with
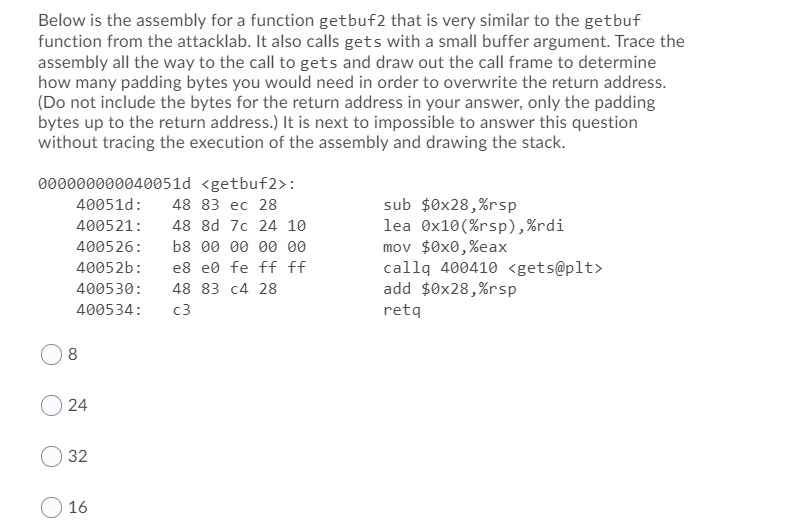
Below is the assembly for a function getbuf2 that is very similar to the getbuf function from the attacklab. It also calls gets with a small buffer argument. Trace the assembly all the way to the call to gets and draw out the call frame to determine how many padding bytes you would need in order to overwrite the return address. (Do not include the bytes for the return address in your answer, only the padding bytes up to the return address.) It is next to impossible to answer this question without tracing the execution of the assembly and drawing the stack. 000000000040051d : sub $0x28,%rsp lea Ox10(%rsp),%rdi mov $0x0,%eax callq 400410 add $0x28,%rsp 40051d: 48 83 28 400521: 48 8d 7c 24 10 400526: b8 00 00 00 00 40052b: e8 e0 fe ff ff 400530: 48 83 c4 28 400534: c3 ret 8 24 32 O 16
Step by Step Solution
3.41 Rating (164 Votes )
There are 3 Steps involved in it
Phase 2 involves injecting a small code and calling function touch2 while making it look like you passed the cookie as an argument to touch2 If you look inside the ctarget dump and search for touch2 i... View full answer

Get step-by-step solutions from verified subject matter experts


