Question: Consider a DBMS using write - ahead logging with the STEAL and NO - FORCE buffer pool management policy. The log contains update records, checkpoints,
Consider a DBMS using writeahead logging with the STEAL and NOFORCE buffer pool management policy. The log contains update records, checkpoints, and transaction begincommitabort records. Assume the DBMS executes a nonfuzzy checkpoint, where all dirty pages are written to disk. Its update record has the following form:
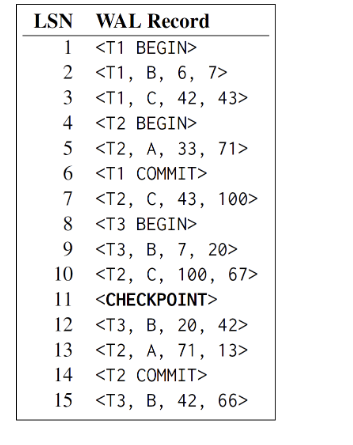
Assume the DBMS uses the ARIES recovery protocol.The database has three transactions T T T on three data objects A B C The following image has a table shows the log records available on disk after a crash:
QWhat should be the correct action on T when recovering the database from WAL?
Question options:
redo all of Ts changes
undo all of Ts changes
do nothing to T
Q What should be the correct action on T when recovering the database from WAL?
Question options:
redo all of Ts changes
undo all of Ts changes
do nothing to T
Q What should be the correct action on T when recovering the database from WAL?
Question options:
redo all of Ts changes
undo all of Ts changes
do nothing to T
Q Assume that the DBMS flushes all dirty pages when the recovery process finishes. What are the values of A B and C after the DBMS recovers the state of the database?
Question options:
A B C
A B C
A B C
A B C
A B C
A B C
A B C
A B C
A B C
A B C
A B C
Not sure
please provide the complete answer
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


