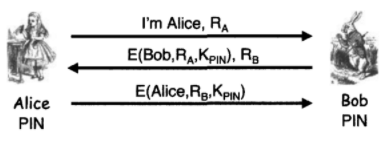
Question: Consider the authentication protocol below, which is based on knowl- edge of a shared 4-digit PIN number. Here, PIN = H(PIN, R A , R
Consider the authentication protocol below, which is based on knowl- edge of a shared 4-digit PIN number. Here, PIN = H(PIN, RA, RB).
a. Suppose that Trudy passively observes one iteration of the protocol. Can she determine the 4-digit PIN number? Justify your answer.
b. Suppose that the PIN number is replaced by a 256-bit shared symmetric key. Is the protocol secure? Why or why not?
I'm Alice, RA E (Bob, RA,KPIN), RB Alice E(Alice,RB,KPIN) Bob PIN PIN
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


