Question: Construct an access control matrix for the subjects and objects of Lipner's commercial model (see below). The matrix will have entries for r(read) and w(write)
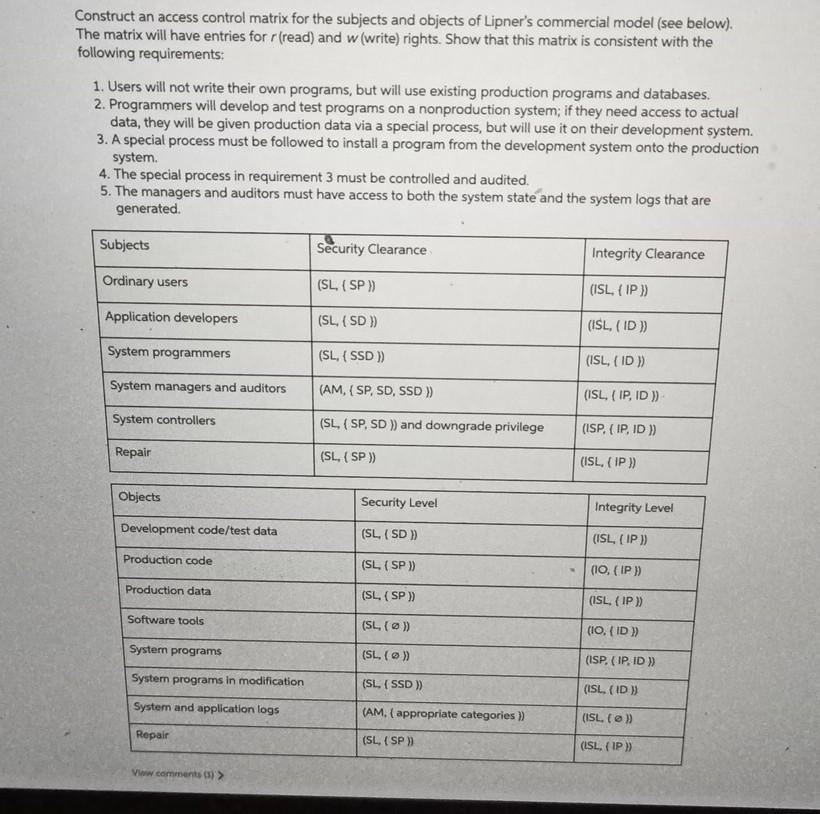
Construct an access control matrix for the subjects and objects of Lipner's commercial model (see below). The matrix will have entries for r(read) and w(write) rights. Show that this matrix is consistent with the following requirements: 1. Users will not write their own programs, but will use existing production programs and databases. 2. Programmers will develop and test programs on a nonproduction system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. 3. A special process must be followed to install a program from the development system onto the production system. 4. The special process in requirement 3 must be controlled and audited. 5. The managers and auditors must have access to both the system state and the system logs that are generated Subjects Security Clearance Integrity Clearance Ordinary users (SL, (SP) (ISL. (IP) Application developers (SL, (SD)) (ISL. (ID)) System programmers (SL, (SSD) (ISL, (ID)) System managers and auditors (AM, (SP, SD, SSD )) (ISL(IP, ID)) System controllers (SL, (SP, SD )) and downgrade privilege (ISP, CIP, ID)) Repair (SL, (SP) (ISL, (IP Objects Security Level Integrity Level Development code/test data (SL, (SD) (ISL (IP) Production code (SL, (SP) (10, (IP) Production data (SL. (SP) (ISL (IP) Software tools (SL. () (10. (ID)) Systern programs (SL, ( ) (ISP, CIP, ID)) System programs in modification (SL. (SSD) (ISL. (ID)) System and application logs (AM,( appropriate categories >> (ISL. ( ) Repair (SL (SP) (ISL (IP) VWww comments) Construct an access control matrix for the subjects and objects of Lipner's commercial model (see below). The matrix will have entries for r(read) and w(write) rights. Show that this matrix is consistent with the following requirements: 1. Users will not write their own programs, but will use existing production programs and databases. 2. Programmers will develop and test programs on a nonproduction system; if they need access to actual data, they will be given production data via a special process, but will use it on their development system. 3. A special process must be followed to install a program from the development system onto the production system. 4. The special process in requirement 3 must be controlled and audited. 5. The managers and auditors must have access to both the system state and the system logs that are generated Subjects Security Clearance Integrity Clearance Ordinary users (SL, (SP) (ISL. (IP) Application developers (SL, (SD)) (ISL. (ID)) System programmers (SL, (SSD) (ISL, (ID)) System managers and auditors (AM, (SP, SD, SSD )) (ISL(IP, ID)) System controllers (SL, (SP, SD )) and downgrade privilege (ISP, CIP, ID)) Repair (SL, (SP) (ISL, (IP Objects Security Level Integrity Level Development code/test data (SL, (SD) (ISL (IP) Production code (SL, (SP) (10, (IP) Production data (SL. (SP) (ISL (IP) Software tools (SL. () (10. (ID)) Systern programs (SL, ( ) (ISP, CIP, ID)) System programs in modification (SL. (SSD) (ISL. (ID)) System and application logs (AM,( appropriate categories >> (ISL. ( ) Repair (SL (SP) (ISL (IP) VWww comments)
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


