Question: Cryptoanalysis Below given is the handout with cipher text and frequency analysis. We don't know anything about the encryption method. We do know that English
Cryptoanalysis
Below given is the handout with cipher text and frequency analysis. We don't know anything about the encryption method.
We do know that English text was encrypted. Please decrypt the text using the frequency information and your knowledge of English.
please check nd picture for cipher
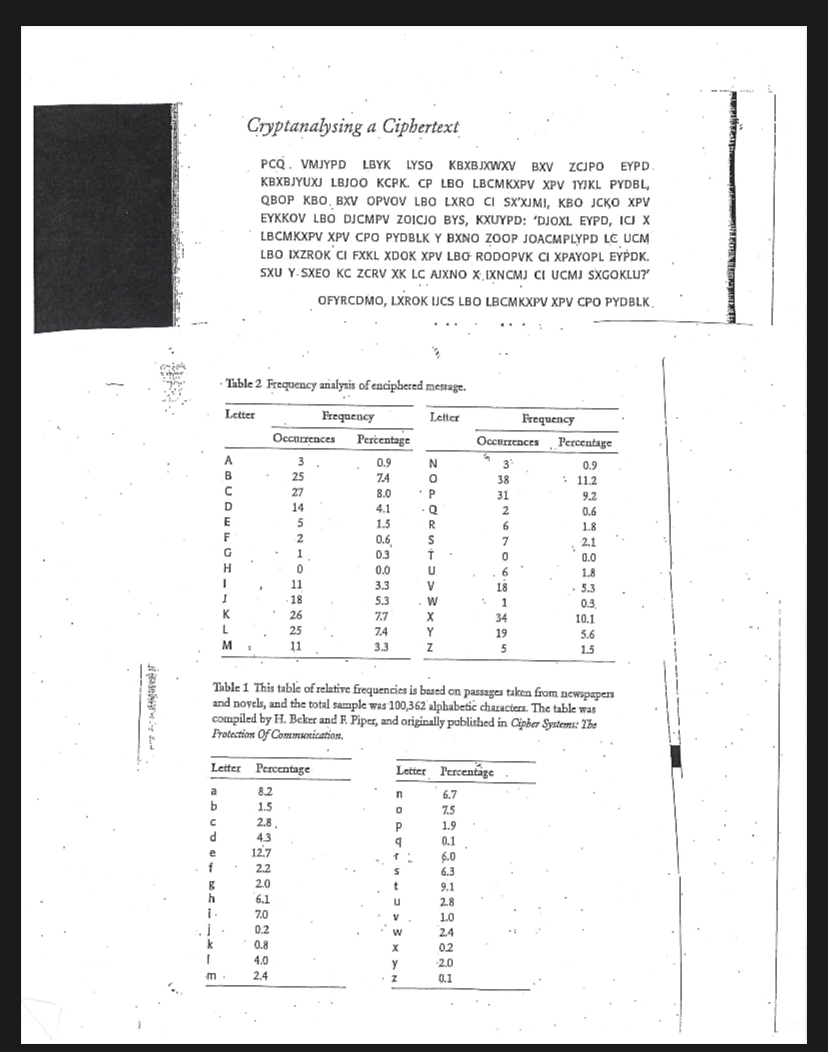
Cryptanalysing a Ciphertext
PCQ VMJYPD LBYK LYSO KBXBJXWXV BXV ZCJPO EYPD KBXBJYUXJ LBJOO KCPK CP LBO LBCMKXPV XPV TYJKL PYDBL QBOP KBO, BXV OPVOV LBO LXRO CI SX'XJMI, KBO JCKO XPV EYKKOV LBO DJCMPV ZOICJO BYS KXUYPD: 'DJOXL. EYPD, ICI X LBCMKXPV XPV CPO PYDBLK Y BXNO ZOOP JOACMPLYPD LC UCM LBO IXZROK' CI FXKL XDOK XPV LBO RODOPVK CI XPAYOPL EYPDE. SXU YSXEO KC ZCRV XK LC AXXNO XDXNCMJ CI UCMJ SXGOKLU?
OFYRCDMO, LXROK UCS LBO LBCMKXXV XPV CPO PYDBLK
Table Frequency anilyzis of enciphered mestage.
tableLetterFrequencyOccurrences,PercentageABCDEFGHIJKLM
tableLetterFrequencyOccurrencesPercentageNOPQRSWUVWXYZ
Table This table of relatire frequencies is based on passages taken from newspapers and novels, and the total sample was alphabetic characters. The table was compiled by H Beker and F Piper, and originally published in Cipher Systems: Tbe Frotection Of Commsorication.
tableLetterPercentageabcdefghij
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


