Question: cryptography & network security Q2 Considering the below figure M M ( M Compare E (b) EK, HOM) Discuss how an attacker can exploit the
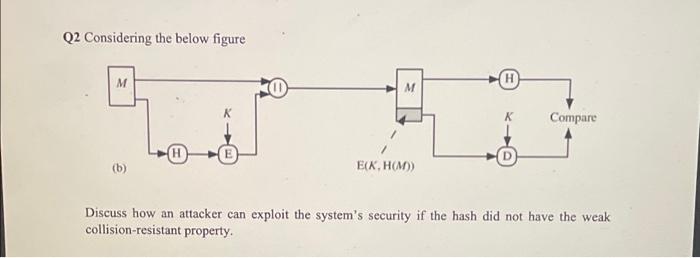
Q2 Considering the below figure M M ( M Compare E (b) EK, HOM) Discuss how an attacker can exploit the system's security if the hash did not have the weak collision-resistant property
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


