Question: Cryptography TOOLS VIEW Enable Editing CTED VIEW Be careful-files from the Internet can contain vinuses, Unless you need to edit, it's safer to stay in

 Cryptography
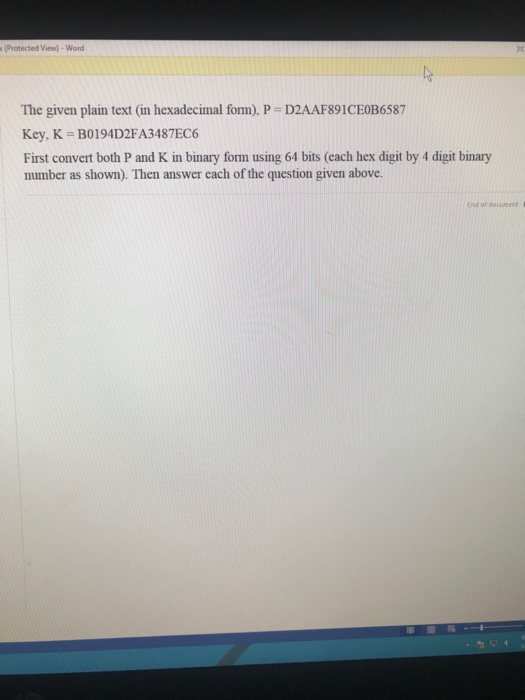
Cryptography TOOLS VIEW Enable Editing CTED VIEW Be careful-files from the Internet can contain vinuses, Unless you need to edit, it's safer to stay in Protected View. HOMEWORK # 3: CS 386 Due Date: February 29, 2018 1. Using Vigenere ciph repeated key procedure and (b) autokey system 2. This problem explores the use of a one-time pad version of the Vigenre cipher In this scheme, the key is a stream of random numbers between 0 and 26. For example, if the key is 3 195..., then the first letter of plaintext is encrypted with a shift of 3 letters, the second with a shift of 19 letters, the third with a shift of 5 letters, and so on. Encrypt the plaintext sendmoremoney with the key stream 9 0 1 7 23 15 21 14 11 11 2 8 9 h. Using the ciphertext produced in part (a),find a key so that the cipher text decrypts to the plaintext cashnotneeded. 3. Consider the following letter encodings: letter A etooding-001-10T011 100 101 110 111 A message M MARIO is Vernam encrypted into ciphertext C = A0AA1V; C-Al e K where shows modulo 2 XOR operation. Find the corresponding encryption key. Provide details of your cryptanalaysis. 4. DES Ilustration This problem provides a numerical example of encryption using a one-round ver- sion of DES Hexadecinal notations 0123456789A BCDEF Binary notation 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 1010 1011 1100 1101 1110 1111 a. Derive Kj, the first-round subkey b. Derive L c. Expand Rg to get EIRl,where El-l is the expansion function of Table S1 d. Calculate A EIRIOKI e Group the 48-bit result of (d) into sets of 6 bits and evaluate the corresponding S-box substitutions Concatenate the results of (e) to get a 32-bit resul, B Apply the permutation to get P(B). t. ls, Calculate Rt-INB) 4 L Write down the ciphertext
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


