Question: CYBERSECURITY ANALYSIS ETHICAL HACKING a) ==================================================== b) In .... phase of Open-source Intelligence information from sources are collected by a threat actor What is a
CYBERSECURITY ANALYSIS ETHICAL HACKING a) 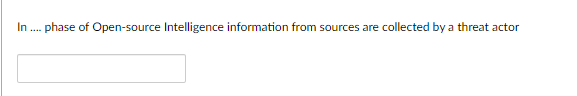 ====================================================
====================================================
b) 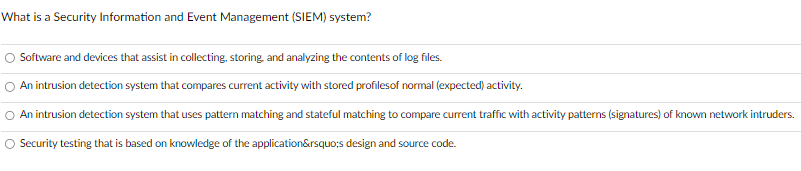
In .... phase of Open-source Intelligence information from sources are collected by a threat actor What is a Security Information and Event Management (SIEM) system? Software and devices that assist in collecting, storing, and analyzing the contents of log files. An intrusion detection system that compares current activity with stored profilesof normal (expected) activity. An intrusion detection system that uses pattern matching and stateful matching to compare current traffic with activity patterns (signatures) of known network intruders. Security testing that is based on knowledge of the application\’s design and source code
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


