Question: d . Identify and explain one ethical hacking step that is not performed by black hat hackers.The International Information Systems Security Certification Consortium ( ISC
d Identify and explain one ethical hacking step that is not performed by black hat hackers.The International Information Systems Security Certification Consortium ISC and ISO defined
security domains and ISO control sets Controls respectively.
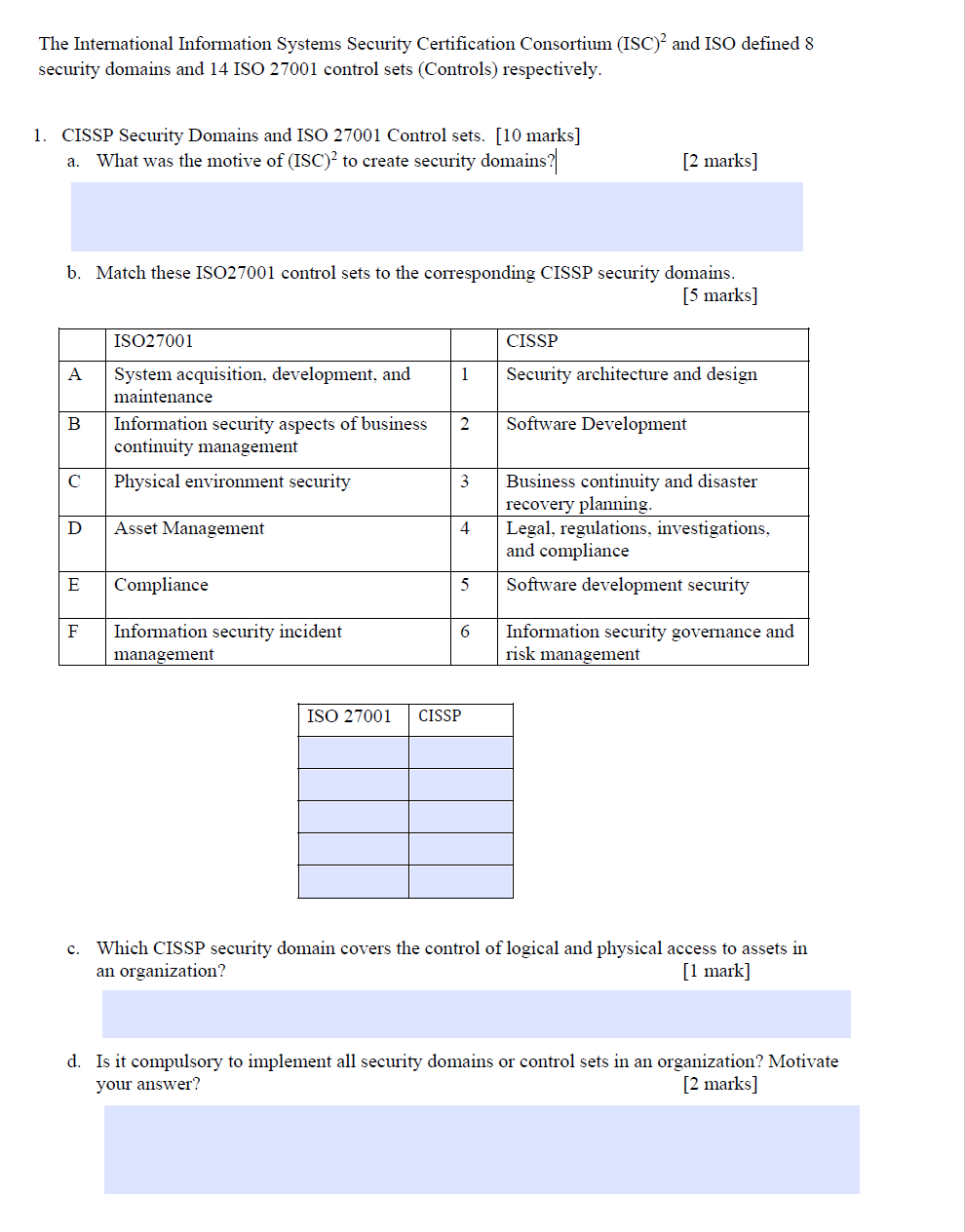
CISSP Security Domains and ISO Control sets. marks
a What was the motive of ISC to create security domains?
marks
b Match these ISO control sets to the corresponding CISSP security domains.
marks
c Which CISSP security domain covers the control of logical and physical access to assets in
an organization?
mark
d Is it compulsory to implement all security domains or control sets in an organization? Motivate
your answer?
marks
marks
e An ethical hacker has been hired to do a penetration test on a company he works for. Name
and explain the type of penetration testing he is doing,
marks
f What is the purpose of the penetration testing type performed in
mark
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


