Question: D Question 1 1 pts What type of attack would allow the attacker could trick computers into sending traffic through the attacker's computer (performing a
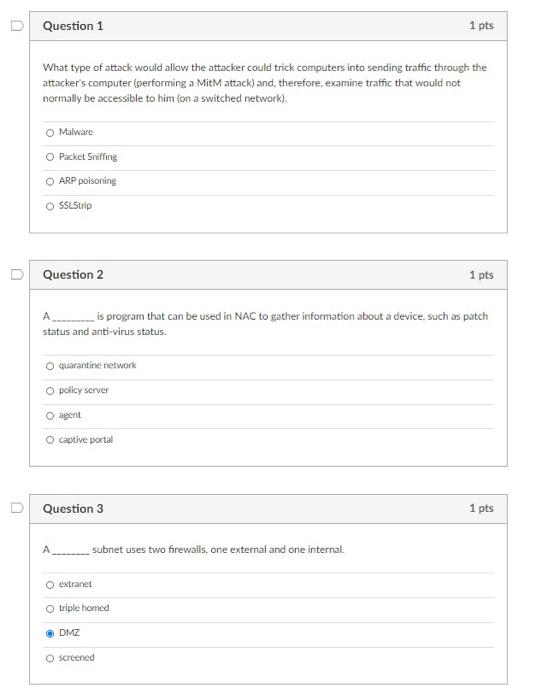
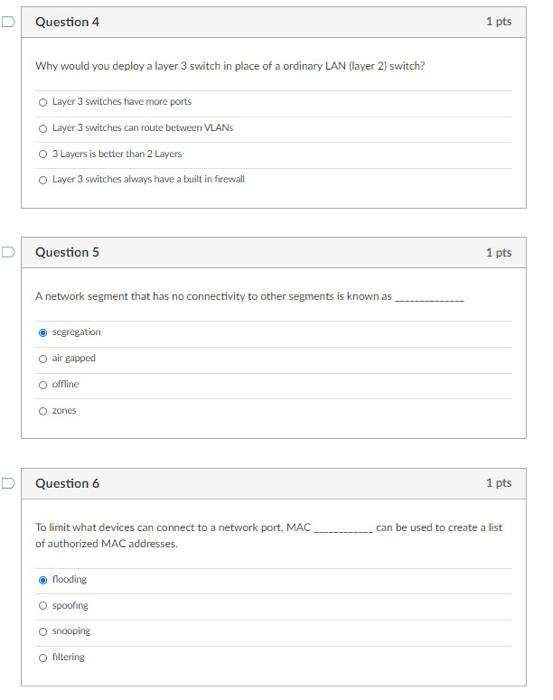
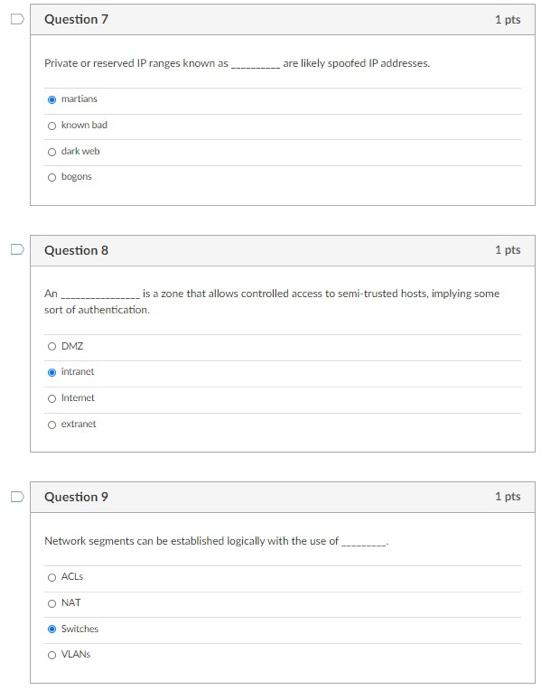
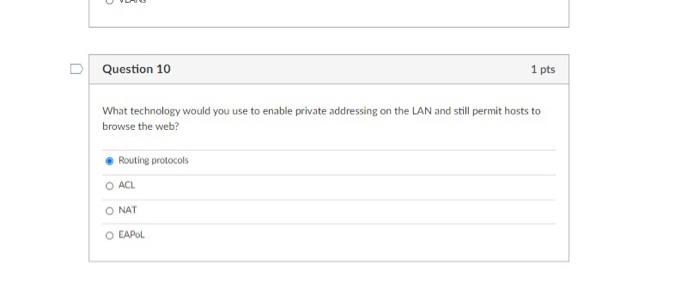
D Question 1 1 pts What type of attack would allow the attacker could trick computers into sending traffic through the attacker's computer (performing a Mit attack) and therefore, examine traffic that would not normally be accessible to him (on a switched network). Malware O Packet Sniffing ARP poisoning O SSL Strip Question 2 1 pts A is program that can be used in NAC to gather information about a device, such as patch status and anti-virus status. O quarantine network O policy server O agent captive portal Question 3 1 pts A subnet uses two firewalls, one external and one internal. O extranet triple homed DMZ O screened Question 4 1 pts Why would you deploy a layer 3 switch in place of a ordinary LAN (layer 2) switch? Layer 3 switches have more ports Layer 3 switches can route between VLANS O 3 Layers is better than 2 Layers Layer 3 switches always have a built in firewall D Question 5 1 pts A network segment that has no connectivity to other segments is known as segregation O air gapped offline Ozones D Question 6 1 pts can be used to create a list To limit what devices can connect to a network port, MAC of authorized MAC addresses. noodine spoofine Osnooping O filtering Question 7 1 pts Private or reserved IP ranges known as are likely spoofed IP addresses. martians known bad dark web bogons Question 8 1 pts An is a zone that allows controlled access to semi-trusted hosts, implying some sort of authentication O DMZ intranet Intemet O extranet Question 9 1 pts Network segments can be established logically with the use of O ACLS O NAT Switches O VLANS D Question 10 1 pts What technology would you use to enable private addressing on the LAN and still permit hosts to browse the web? Routing protocols O ACL O NAT O EAPOL
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


