Question: Data security Preferably in Java 1.) (50 POINTS - 25 POINTS each) A ciphertext C given as follows: TEBKFKQEBZLROPBLCERJXKBSBKQP is known to be enciphered using
Data security
Preferably in Java
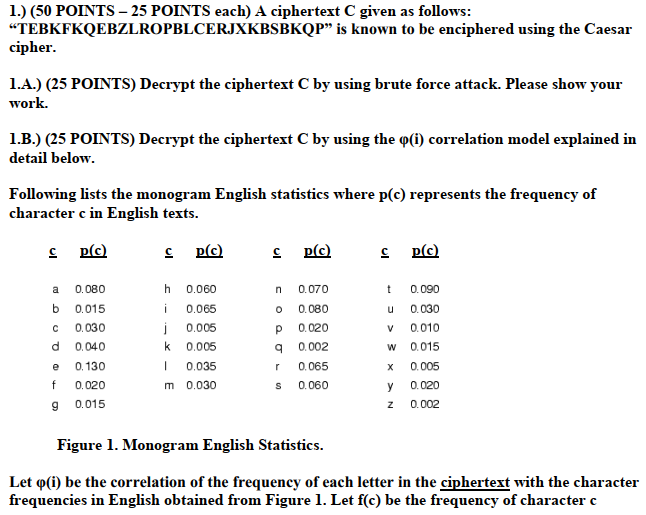

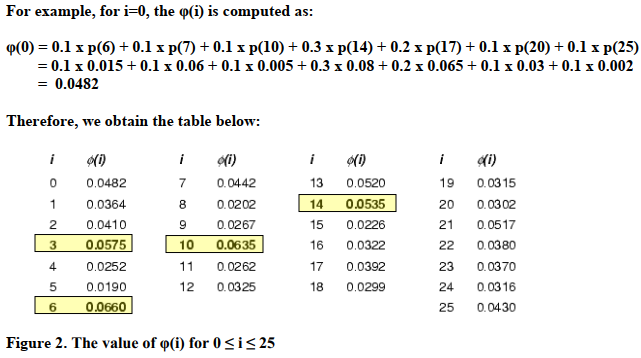
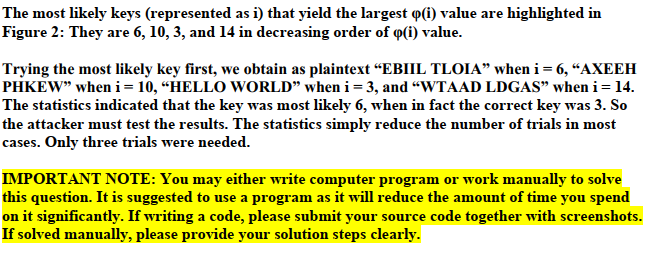
1.) (50 POINTS - 25 POINTS each) A ciphertext C given as follows: TEBKFKQEBZLROPBLCERJXKBSBKQP is known to be enciphered using the Caesar cipher 1.A.) (25 POINTS) Decrypt the ciphertext C by using brute force attack. Please show your work. 1.B.) (25 POINTS) Decrypt the ciphertext C by using the p(i) correlation model explained in detail below Following lists the monogram English statistics where p(c) represents the frequency of character c in English texts. c p(C c p(C c p(C c p(C a 0.080 b 0.015 0.030 d 0.040 e 0.130 f 0.020 9 0.015 h 0.060 i 0.065 0.00 k 0.005 n 0.070 o 0.080 p 0.020 q0.002 r 0.065 s 0.060 t 0.090 u 0.030 v 0.010 W 0.015 x 0.005 y 0.020 Z 0.002 0.035 m 0.030 Figure 1. Monogram English Statistics. Let (i) be the correlation of the frequencv of each letter in the ciphertext with the character frequencies in English obtained from Figure 1. Let f(c) be the frequency of character c 1.) (50 POINTS - 25 POINTS each) A ciphertext C given as follows: TEBKFKQEBZLROPBLCERJXKBSBKQP is known to be enciphered using the Caesar cipher 1.A.) (25 POINTS) Decrypt the ciphertext C by using brute force attack. Please show your work. 1.B.) (25 POINTS) Decrypt the ciphertext C by using the p(i) correlation model explained in detail below Following lists the monogram English statistics where p(c) represents the frequency of character c in English texts. c p(C c p(C c p(C c p(C a 0.080 b 0.015 0.030 d 0.040 e 0.130 f 0.020 9 0.015 h 0.060 i 0.065 0.00 k 0.005 n 0.070 o 0.080 p 0.020 q0.002 r 0.065 s 0.060 t 0.090 u 0.030 v 0.010 W 0.015 x 0.005 y 0.020 Z 0.002 0.035 m 0.030 Figure 1. Monogram English Statistics. Let (i) be the correlation of the frequencv of each letter in the ciphertext with the character frequencies in English obtained from Figure 1. Let f(c) be the frequency of character c
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


