Question: Defensible Security Architecture (DSA) Lifecycle is an effective methodology based on practical models that allows to secure new or existing infrastructure. Apply DSA lifecycle to




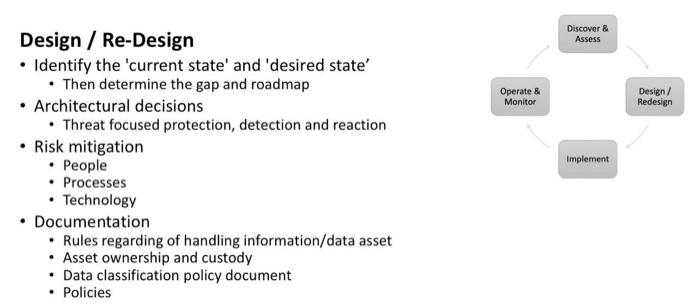
Defensible Security Architecture (DSA) Lifecycle is an effective methodology based on practical models that allows to secure new or existing infrastructure. Apply DSA lifecycle to the following: - Router (Layer 3) - IPv6 2.3 Defensible Security Architecture Lifecycle Discover \& Assess - Identify requirements (business \& regulatory) - Identify and prioritize critical assets - Sets goals, objectives \& expectations - Sets risk appetite (the level of risk that the organization is willing to take) - Threat modeling (threat identification, vulnerability analysis/Pen testing) - Risk analysis (Threat modeling is discussed next section) Implement - Implement what you have designed/redesigned. - Establish processes, and controls - Establish baseline in device configurations and traffic 1 - Enable logging for monitoring - Appoint \& train people - Validate implementation. Operate \& Monitor - Continuous security monitoring - Data and logs - Network traffic ( NetFlow, pcaps) - Monitor performance \& risk - Create and conduct awareness regularly on threat intel and lessons learned - Risk mitigation - People - Processes - Technology - Documentation - Rules regarding of handling information/data asset - Asset ownership and custody - Data classification policy document - Policies
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


