Question: DES is already done I just need HMAC ClientCand Server Sshare a key for HMAC in anoffline manner (e.g., a local file). Client Cthen generates
DES is already done I just need HMAC
ClientCand Server Sshare a key for HMAC in anoffline manner (e.g., a local file). Client Cthen generates a message, gets the HMAC digest of this message, and encryptsthe message along with its HMAC to obtain ciphertext. Then Csends this ciphertext to ServerS. ServerSdecrypts received ciphertext and then verifies the integrity of the received message by generating another HMAC with the shared HMAC key and matchesthe two HMACs. Client Cand Server Sswitch the roles and do the above again. All the transmitted messages should be encrypted with DES.
1.S and C share two keys. One is for HMAC, the other is for DES. Dump them to files.
2.S and C set up a simple chat program. (Socket)
3.S and C both load HMAC key and DES key from the files on startup of their programs.
4.S and C exchange messages. The messages should be entered by you through the keyboard in the console, NOT by hardcoding.
Both sides should display
Shared keys for HMACs and DES
Plain message and HMAC before concatenation
Ciphertext to be sent
Received Ciphertext
Plain Message and HMAC after decryption and seperation
Receiver calculated HMAC, which uses KHMAC and received plain message+
Verification result(by compared two HMACs)
server.py
from des import DesKey import hmac import hashlib import binascii import socket #Create the socket #AF_INET = IPV4 #SOCK_STREAM ==TCP sc = socket.socket(socket.AF_INET,socket.SOCK_STREAM) sc.bind((socket.gethostname(),9494)) sc.listen(7) print("Pinging the server.....") clientsocket, address = sc.accept() print("Connection has been received %s"%(str(address))) clientsocket.send(str("Connection established").encode()) keystr = "keytovictoryisto" key = DesKey(keystr.encode('utf-8')) while True: message = clientsocket.recv(1024) print("Received Ciphertext is: %s"%message.decode("utf-8","ignore")) pt = key.decrypt(message, padding=True).decode() print("Received plaintext is: %s"%pt) msg = input("Type here:") ct = key.encrypt(msg.encode("utf-8"), padding= True) print("Shared DES key is", keystr) print("Sent plaintext is: %s"%msg) print("Sent ciphertext is: %s"%ct.decode("utf-8","ignore")) clientsocket.send(ct) clientsocket.close()client.py:
from des import DesKey import socket import hashlib import hmac import binascii #Create the socket #AF_INET = IPV4 #SOCK_STREAM ==TCP sc = socket.socket(socket.AF_INET,socket.SOCK_STREAM) sc.connect((socket.gethostname(),9494)) print(sc.recv(1024).decode()) keystr = "keytovictoryisto" key = DesKey(keystr.encode('utf-8')) while True: msg = input("Type here:") ct = key.encrypt(msg.encode('utf-8'),padding = True) print("Shared DES key is ",keystr) print("Shared HMAC key is",keystr) print("Sent plaintext is: %s"%msg) print("Sent ciphertext is: %s"%ct.decode('utf-8','ignore')) sc.send(ct) message = sc.recv(1024) print("Received ciphertext is: %s"%message.decode('utf-8','ignore')) pt = key.decrypt(rcv, padding=True).decode() print("Recieved plaintext is: %s" % pt) sc.close() I need the output below 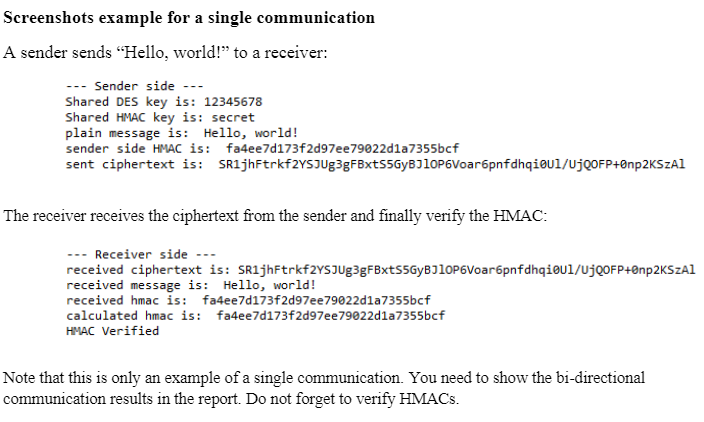
Screenshots example for a single communication A sender sends "Hello, world!" to a receiver: --- Sender side Shared DES key is: 12345678 Shared HMAC key is: secret plain message is: Hello, world! sender side HMAC is: fa4ee7d173f2d97ee79022d1a7355bcf sent ciphertext is: SRijhFtrkf2YSJUg3gFBxt55GyBJIOP6Voar opnfdhqiel/UjQOFP+Onp2KSZAI The receiver receives the ciphertext from the sender and finally verify the HMAC: -- Receiver side --- received ciphertext is: SRijhFtrkfYSJUg3gFBxts5GyBJ10P6Voar pnfdhqiel/UjQOFP+Onp2KSzal received message is: Hello, world! received hmac is: fa4ee7d173f2d97ee79022d1a7355bcf calculated hmac is: fa4ee7d173f2d97ee79022d1a7355bcf HMAC Verified Note that this is only an example of a single communication. You need to show the bi-directional communication results in the report. Do not forget to verify HMACS. Screenshots example for a single communication A sender sends "Hello, world!" to a receiver: --- Sender side Shared DES key is: 12345678 Shared HMAC key is: secret plain message is: Hello, world! sender side HMAC is: fa4ee7d173f2d97ee79022d1a7355bcf sent ciphertext is: SRijhFtrkf2YSJUg3gFBxt55GyBJIOP6Voar opnfdhqiel/UjQOFP+Onp2KSZAI The receiver receives the ciphertext from the sender and finally verify the HMAC: -- Receiver side --- received ciphertext is: SRijhFtrkfYSJUg3gFBxts5GyBJ10P6Voar pnfdhqiel/UjQOFP+Onp2KSzal received message is: Hello, world! received hmac is: fa4ee7d173f2d97ee79022d1a7355bcf calculated hmac is: fa4ee7d173f2d97ee79022d1a7355bcf HMAC Verified Note that this is only an example of a single communication. You need to show the bi-directional communication results in the report. Do not forget to verify HMACS
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


