Question: D.Fill in the blank 3 points) 1. There are different types of management systems for cyber defense. Among them, one management system requires that a
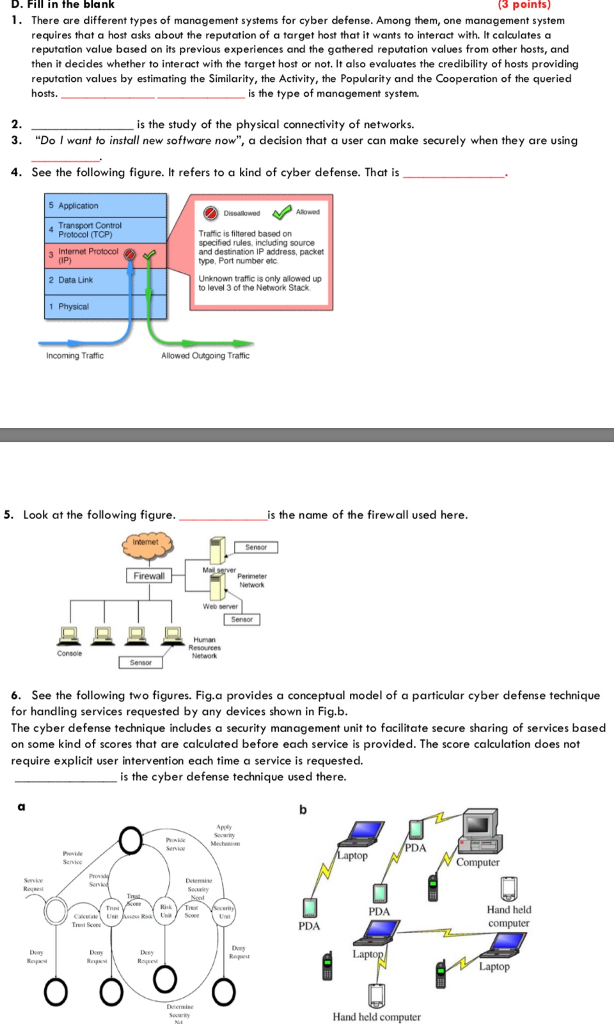

D.Fill in the blank 3 points) 1. There are different types of management systems for cyber defense. Among them, one management system requires that a host asks about the reputation of a target host that it wants to interact with. It calaulates a reputation value based on its previous experiences and the gathered reputation values from other hosts, and then it decides whether to interact with the target host or not. It also evaluates the credibility of hosts providing reputation values by estimating the Similarity, the Activity, the Popularity and the Cooperation of the queried hosts. is the type of management system. 2 is the study of the physical connectivity of networks. 3. "Do I want to install new software now", a decision that a user can make securely when they are using 4. See the following figure. It refers to a kind of cyber defense. That is 5 Application 4 Transport Control Protcool (TCP) Traffic is filtered based on specified rules, including source and destination IP address, packet type, Port number etc 3 Internet Protocol (IP) 2 Data Link 1 Physical Uniknown traffic is only alowed up to level 3 of the Network Stack Incoming Tratfic Allowed Outgoing Traffic 5. Look at the following figure s the name of the firew all used here Sensor Mail sever Firewal Human 6. See the following two figures. Fig.a provides a conceptual model of a particular cyber defense technique for handling services requested by any devices shown in Fig.b. The cyber defense technique includes a security management unit to facilitate secure sharing of services based on some kind of scores that are calculated before each service is provided. The score calculation does not require explicit user intervention each time a service is requested. is the cyber defense technique used there. ai pply PDA Hand held Hand held computer B. Select True or False for the following statements (3 points) 1. The Inherent risk and the residual risk could be the same, however, the risk tolerance differs. 2. IPS cannot recognize unknown anomalies. 3. When you are working in a group project of your organization and having a secret collaboration with an outsider, the situation is assumed to the collusion attack. 4. IDS include all abilities of intrusion detection and also attempt to stop possible cyber incident:s. 5. A firewall can be developed to protect a computer by blocking certain programs from sending and receiving information from a local network or the Internet. 6. Trust management is a countermeasure that picks an appropriate reputation estimation model for a given application. D.Fill in the blank 3 points) 1. There are different types of management systems for cyber defense. Among them, one management system requires that a host asks about the reputation of a target host that it wants to interact with. It calaulates a reputation value based on its previous experiences and the gathered reputation values from other hosts, and then it decides whether to interact with the target host or not. It also evaluates the credibility of hosts providing reputation values by estimating the Similarity, the Activity, the Popularity and the Cooperation of the queried hosts. is the type of management system. 2 is the study of the physical connectivity of networks. 3. "Do I want to install new software now", a decision that a user can make securely when they are using 4. See the following figure. It refers to a kind of cyber defense. That is 5 Application 4 Transport Control Protcool (TCP) Traffic is filtered based on specified rules, including source and destination IP address, packet type, Port number etc 3 Internet Protocol (IP) 2 Data Link 1 Physical Uniknown traffic is only alowed up to level 3 of the Network Stack Incoming Tratfic Allowed Outgoing Traffic 5. Look at the following figure s the name of the firew all used here Sensor Mail sever Firewal Human 6. See the following two figures. Fig.a provides a conceptual model of a particular cyber defense technique for handling services requested by any devices shown in Fig.b. The cyber defense technique includes a security management unit to facilitate secure sharing of services based on some kind of scores that are calculated before each service is provided. The score calculation does not require explicit user intervention each time a service is requested. is the cyber defense technique used there. ai pply PDA Hand held Hand held computer B. Select True or False for the following statements (3 points) 1. The Inherent risk and the residual risk could be the same, however, the risk tolerance differs. 2. IPS cannot recognize unknown anomalies. 3. When you are working in a group project of your organization and having a secret collaboration with an outsider, the situation is assumed to the collusion attack. 4. IDS include all abilities of intrusion detection and also attempt to stop possible cyber incident:s. 5. A firewall can be developed to protect a computer by blocking certain programs from sending and receiving information from a local network or the Internet. 6. Trust management is a countermeasure that picks an appropriate reputation estimation model for a given application
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


