Question: e Please answer me ASAP Looking at the Subcategory column in Table 2 (pages 31-50, numbered pp24-44) Identify 6 things you think would be easy
 e
e
Please answer me ASAP
Looking at the Subcategory column in Table 2 (pages 31-50, numbered pp24-44) Identify 6 things you think would be easy to implement. Identify an organization (business, workplace, etc), and give the rationale for implementing each of your six in that organization, and why it would be easy.
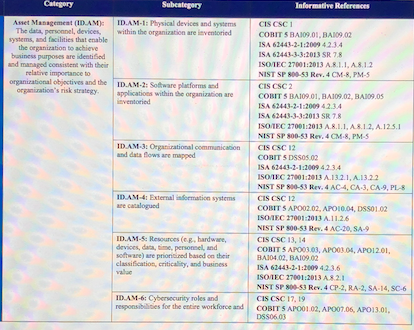
Categery Subcategory Informative References Anet Managemest (ID AM ID.AM-1:Physical devices and systems The data, personnel, devices within the organization are leventoried CORIT S BAI09.01,BA902 SA 62443-2-1:2009 42.3 4 ISA 62443-3-3:2013 SR 78 ISOMEC 27001:2013 A8.1.1, A8.12 NIST SP 800-53 Rev. 4 CM-8, PM-5 CIS CSC2 systems, and facilities that enable the oeganization to achieve business purposes are identiSed and managed consistent with thei relative importance to organizational objoctives and the ID.AM-2: Sotware placforms an organiration's risk strategy applications within the organization are COBIT S BA109.01, BA109.02, BA9.05 ISA 62443-2-1:2009 42.3.4 ISA 62443-3-3:2013 SR 7.8 ISOMEC 27001:2013 A.8.1.1, A.8.12, A.125.1 NIST SP800-53 Rev, 4 CM8, PM5 CIS CSC 12 COBIT S DSS05.02 SA 62443-2-1:2009 42.3.4 ISOIEC 2700112013 A.132. 1, A.13.22 NIST SP 800-53 Rev, 4 AC-4, CA-3, CA-9, PL- IDAM.3: Organirational communication and data Bows are mapped ID.AM-4 External nformasise systems CIS CS re catalogued COBIT SAPO02.02, APO10.04, DSS0102 ISOIEC 27001:2013 A.11.2.6 NIST SP 500-53 Rev.4 AC-20, SA-9 ID.AM-5: Resources (eg, hardware, devices, daa, time, personsel, and software) are prionicined based on their classiscation, criticallity, and business valae CIS CSC 13, 14 COBIT 5 03. AP003 04, APO201. BAI04 02. IA09 02 ISA 62443-2-1:2009 423.6 son EC 27001:2013 A.8.2.1 NIST SP 800-53 Rev. 4 CP-2, RA-2, SA-14, SC-6 CIS CSC 17, 19 DAM-6: Cybersecurity roles and responsibilities for the entiee workforce and COBIT S APO01 02, APO07.06, APO 3,01, DSS06.03 Categery Subcategory Informative References Anet Managemest (ID AM ID.AM-1:Physical devices and systems The data, personnel, devices within the organization are leventoried CORIT S BAI09.01,BA902 SA 62443-2-1:2009 42.3 4 ISA 62443-3-3:2013 SR 78 ISOMEC 27001:2013 A8.1.1, A8.12 NIST SP 800-53 Rev. 4 CM-8, PM-5 CIS CSC2 systems, and facilities that enable the oeganization to achieve business purposes are identiSed and managed consistent with thei relative importance to organizational objoctives and the ID.AM-2: Sotware placforms an organiration's risk strategy applications within the organization are COBIT S BA109.01, BA109.02, BA9.05 ISA 62443-2-1:2009 42.3.4 ISA 62443-3-3:2013 SR 7.8 ISOMEC 27001:2013 A.8.1.1, A.8.12, A.125.1 NIST SP800-53 Rev, 4 CM8, PM5 CIS CSC 12 COBIT S DSS05.02 SA 62443-2-1:2009 42.3.4 ISOIEC 2700112013 A.132. 1, A.13.22 NIST SP 800-53 Rev, 4 AC-4, CA-3, CA-9, PL- IDAM.3: Organirational communication and data Bows are mapped ID.AM-4 External nformasise systems CIS CS re catalogued COBIT SAPO02.02, APO10.04, DSS0102 ISOIEC 27001:2013 A.11.2.6 NIST SP 500-53 Rev.4 AC-20, SA-9 ID.AM-5: Resources (eg, hardware, devices, daa, time, personsel, and software) are prionicined based on their classiscation, criticallity, and business valae CIS CSC 13, 14 COBIT 5 03. AP003 04, APO201. BAI04 02. IA09 02 ISA 62443-2-1:2009 423.6 son EC 27001:2013 A.8.2.1 NIST SP 800-53 Rev. 4 CP-2, RA-2, SA-14, SC-6 CIS CSC 17, 19 DAM-6: Cybersecurity roles and responsibilities for the entiee workforce and COBIT S APO01 02, APO07.06, APO 3,01, DSS06.03
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


