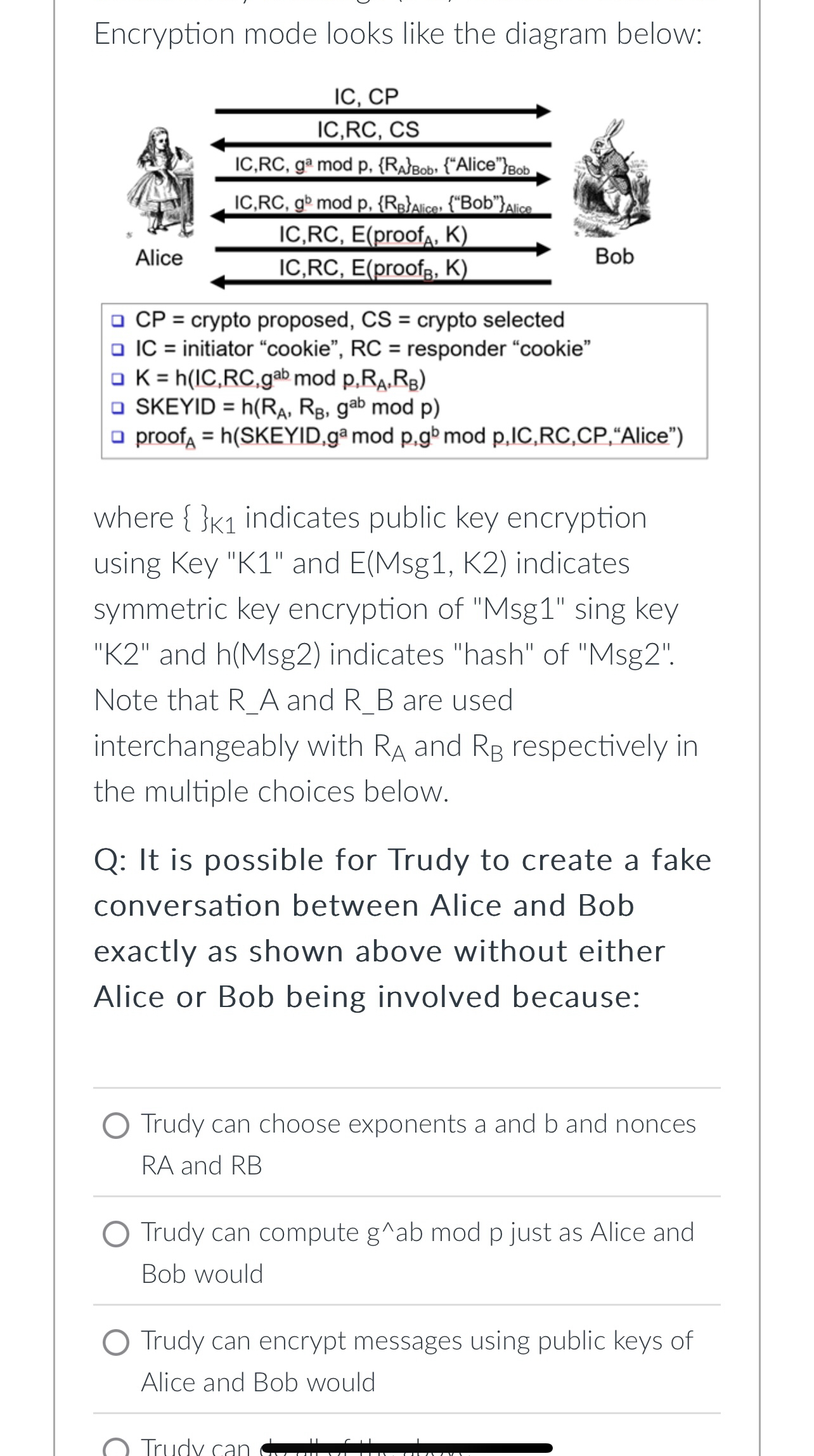
Question: Encryption mode looks like the diagram below:where } _ ( K 1 ) : } indicates public key encryption using Key K 1
Encryption mode looks like the diagram below:where K: indicates public key encryption using Key K and EMsg K indicates symmetric key encryption of Msg sing key K and hMsg indicates "hash" of MsgNote that RA and RB are used interchangeably with RA and RB respectively in the multiple choices below.
Q: It is possible for Trudy to create a fake conversation between Alice and Bob exactly as shown above without either Alice or Bob being involved because:
a trudy can choose exponents a and and nonces and
b trudy can compute gab mod p just as Alice and Bob would
C trudy can encrypt messages using public keys of Alice and Bob would
d Trudy can do all of the above
Step by Step Solution
There are 3 Steps involved in it
1 Expert Approved Answer
Step: 1 Unlock


Question Has Been Solved by an Expert!
Get step-by-step solutions from verified subject matter experts
Step: 2 Unlock
Step: 3 Unlock


