Question: EP2: Assume a block cipher achieving the avalanche effect is used. Does this guarantee that the encryption algorithm has the same effect? Explain your answer
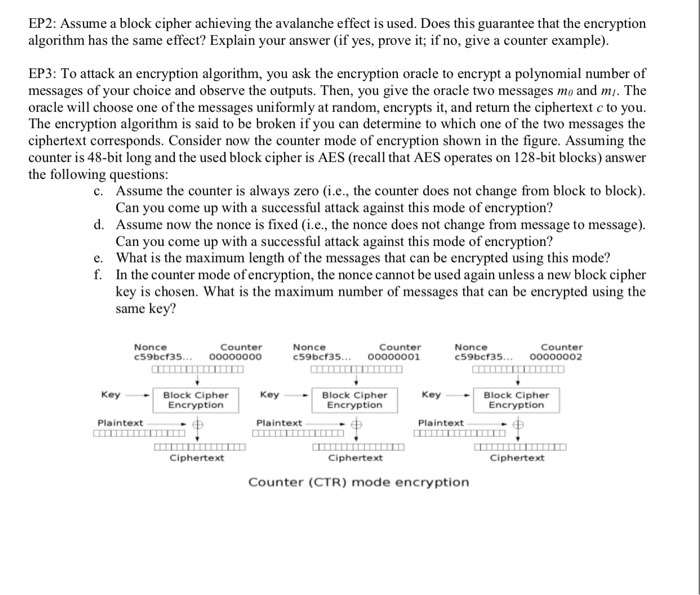
EP2: Assume a block cipher achieving the avalanche effect is used. Does this guarantee that the encryption algorithm has the same effect? Explain your answer (if yes, prove it; if no, give a counter example) EP3: To attack an encryption algorithm, you ask the encryption oracle to encrypt a polynomial number of messages of your choice and observe the outputs. Then, you give the oracle two messages mo and mi. The oracle will choose one of the messages uniformly at random, encrypts it, and return the ciphertext cto you The encryption algorithm is said to be broken if you can determine to which one of the two messages the ciphertext corresponds. Consider now the counter mode of encryption shown in the figure. Assuming the counter is 48-bit long and the used block cipher is AES (recall that AES operates on 128-bit blocks) answer the following questions: c. Assume the counter is always zero (i.e., the counter does not change from block to block) d. Assume now the nonce is fixed (i.e., the nonce does not change from message to message). e. What is the maximum length of the messages that can be encrypted using this mode? Can you come up with a successful attack against this mode of encryption? Can you come up with a successful attack against this mode of encryption? f. In the counter mode of encryption, the nonce cannot be used again unless a new block cipher key is chosen. What is the maximum number of messages that can be encrypted using the same key? Nonce c59bcf35. Counter Nonce c59bcf35 ooo00o01 Counter Nonce c59bcf35. ooooo002 Counter Block Cipher Block Cipher Encryption Block Cipher tion Plaintext Plaintext Plaintext Ciphertext Ciphertext Ciphertext Counter (CTR) mode encryption
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


