Question: Ethical Hacking Assignment 2 Networking Fundamentals Objective: To understand how networks function and have conceptual comprehension of how the protocols fit together. There is
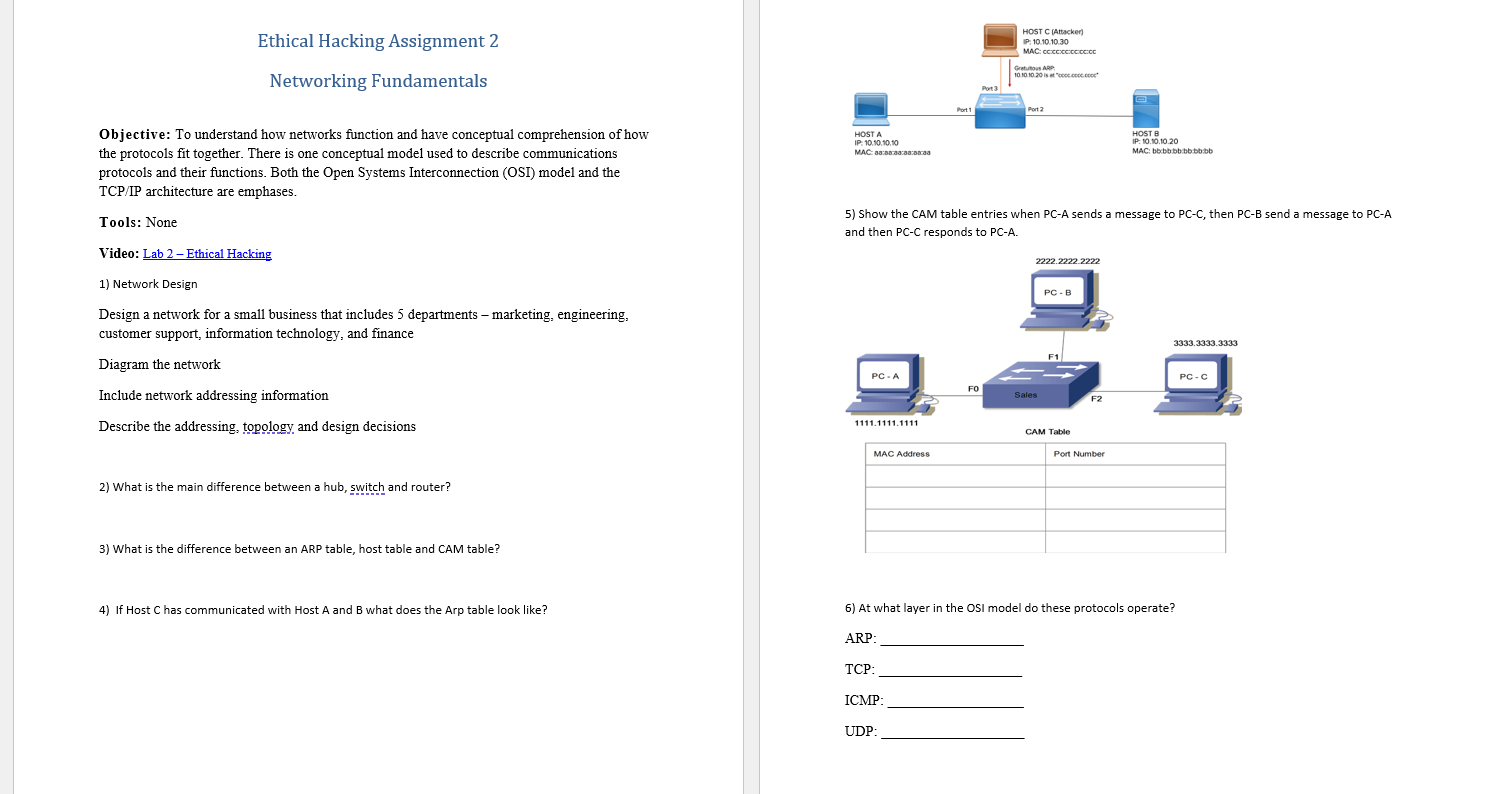
Ethical Hacking Assignment 2 Networking Fundamentals Objective: To understand how networks function and have conceptual comprehension of how the protocols fit together. There is one conceptual model used to describe communications protocols and their functions. Both the Open Systems Interconnection (OSI) model and the TCP/IP architecture are emphases. Tools: None Video: Lab 2- Ethical Hacking 1) Network Design Design a network for a small business that includes 5 departments - marketing, engineering. customer support, information technology, and finance Diagram the network Include network addressing information Describe the addressing, topology and design decisions 2) What is the main difference between a hub, switch and router? 3) What is the difference between an ARP table, host table and CAM table? 4) If Host C has communicated with Host A and B what does the Arp table look like? HOST A IP: 10.10.10.10 MAC: 00:00:00:08:08:33 PC-A 1111.1111.1111 MAC Address TCP: Port 1 ICMP: 5) Show the CAM table entries when PC-A sends a message to PC-C, then PC-B send a message to PC-A and then PC-C responds to PC-A. UDP: Part 3 FO HOST C (Attacker) IP: 10.10.10.30 MAC: ccxxccccccc Gratuitous ARP 10.10.10.20is et "ccoc.cooc.coo Port 2 2222.2222.2222 Sales PC-B CAM Table F2 e Port Number HOST B IP:10.10.10.20 MAC: bbbbbbbbbbbb 6) At what layer in the OSI model do these protocols operate? ARP: 3333.3333.3333 PC-C
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


