Question: Exam - Requires Respondus LockDown Browser + Webcam Question 10 (1 point) Saved 21 ) Listen The process of monitoring progress and making necessary adjustments
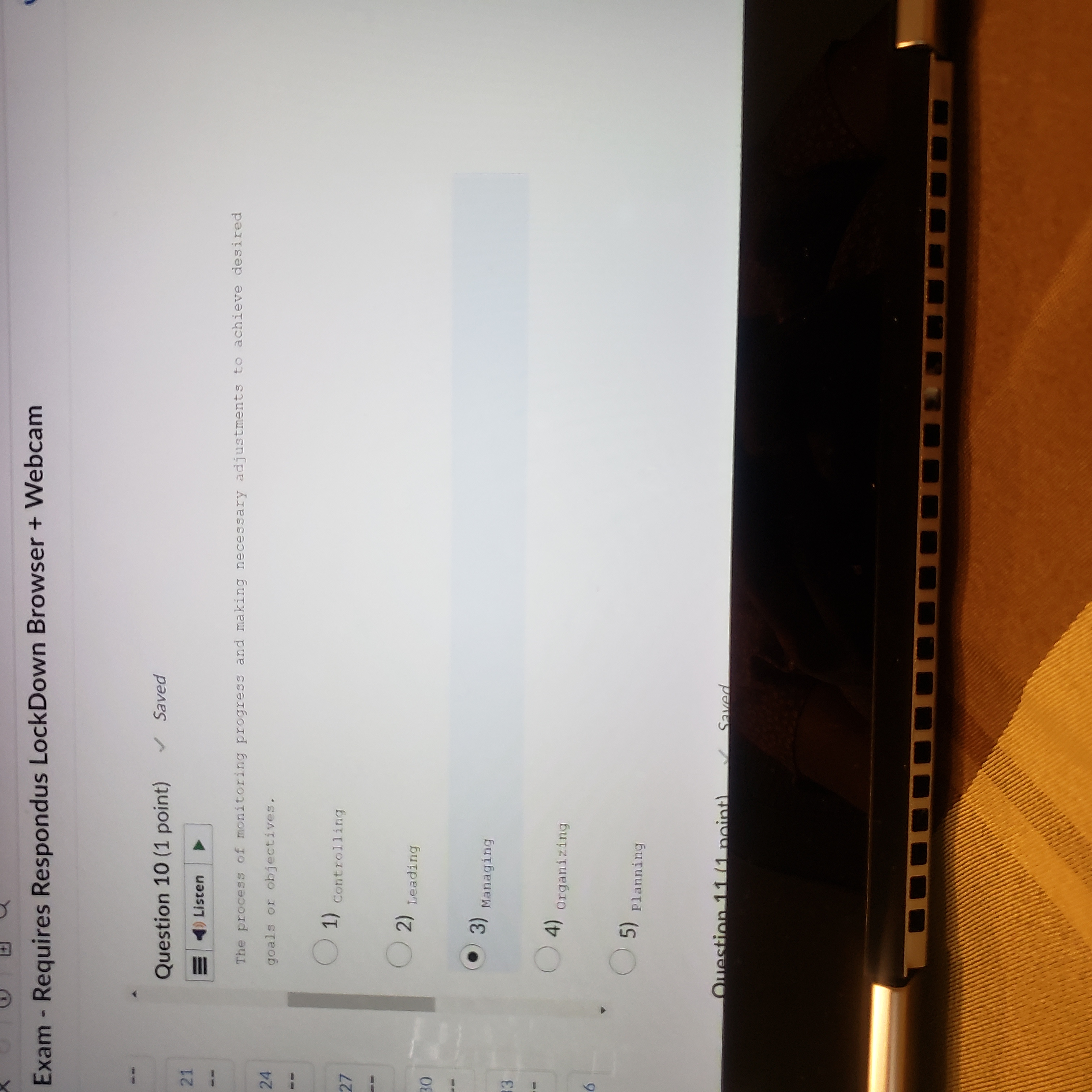
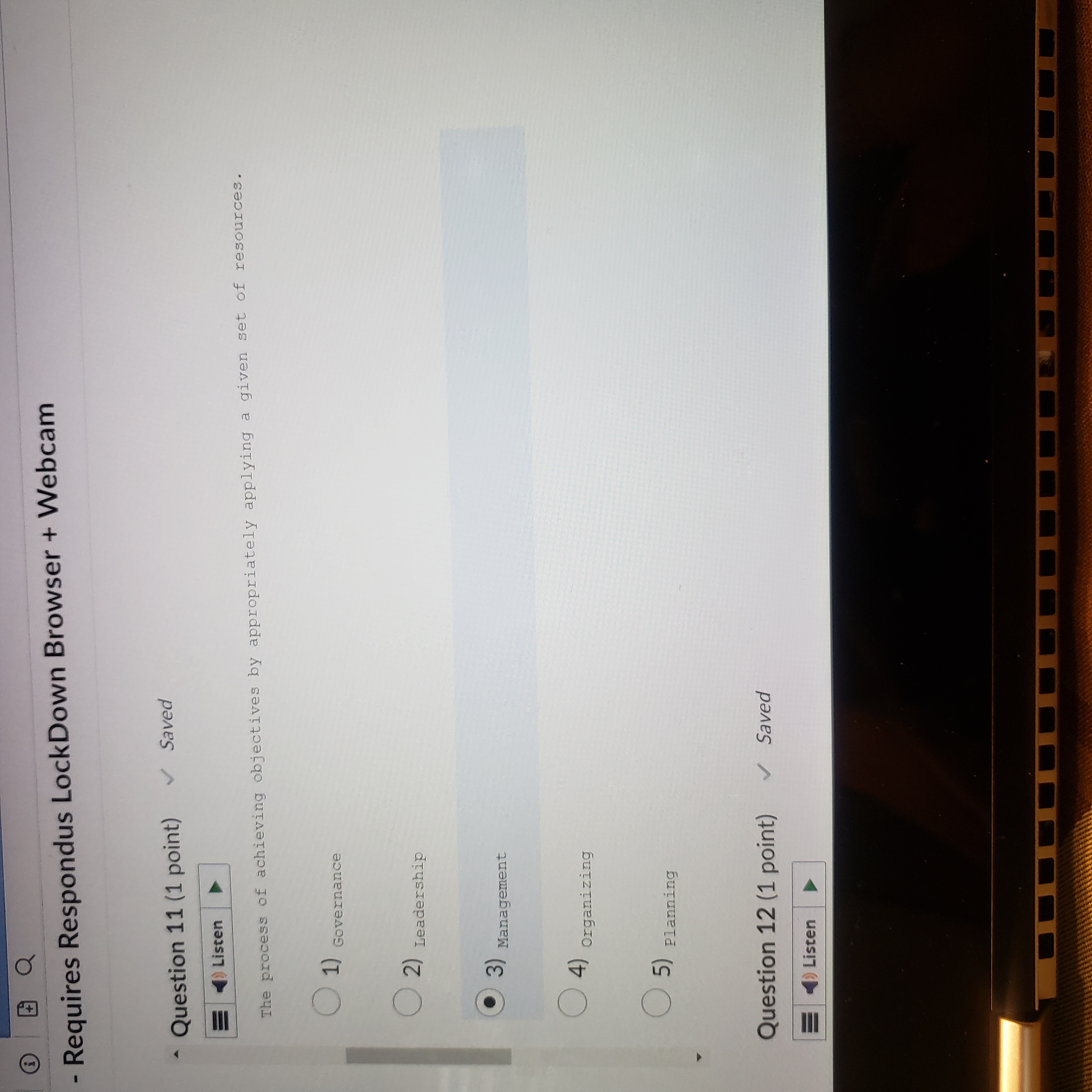
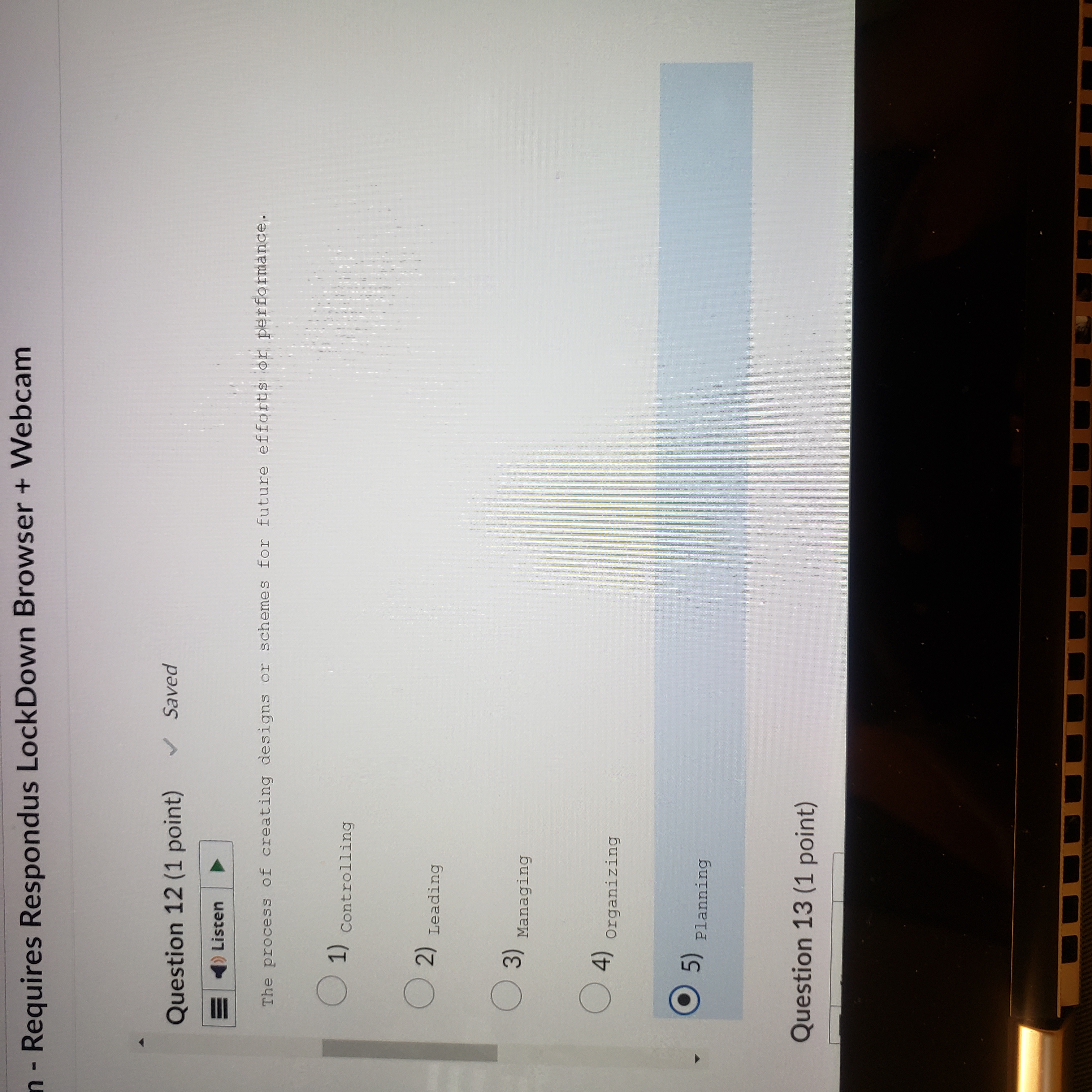
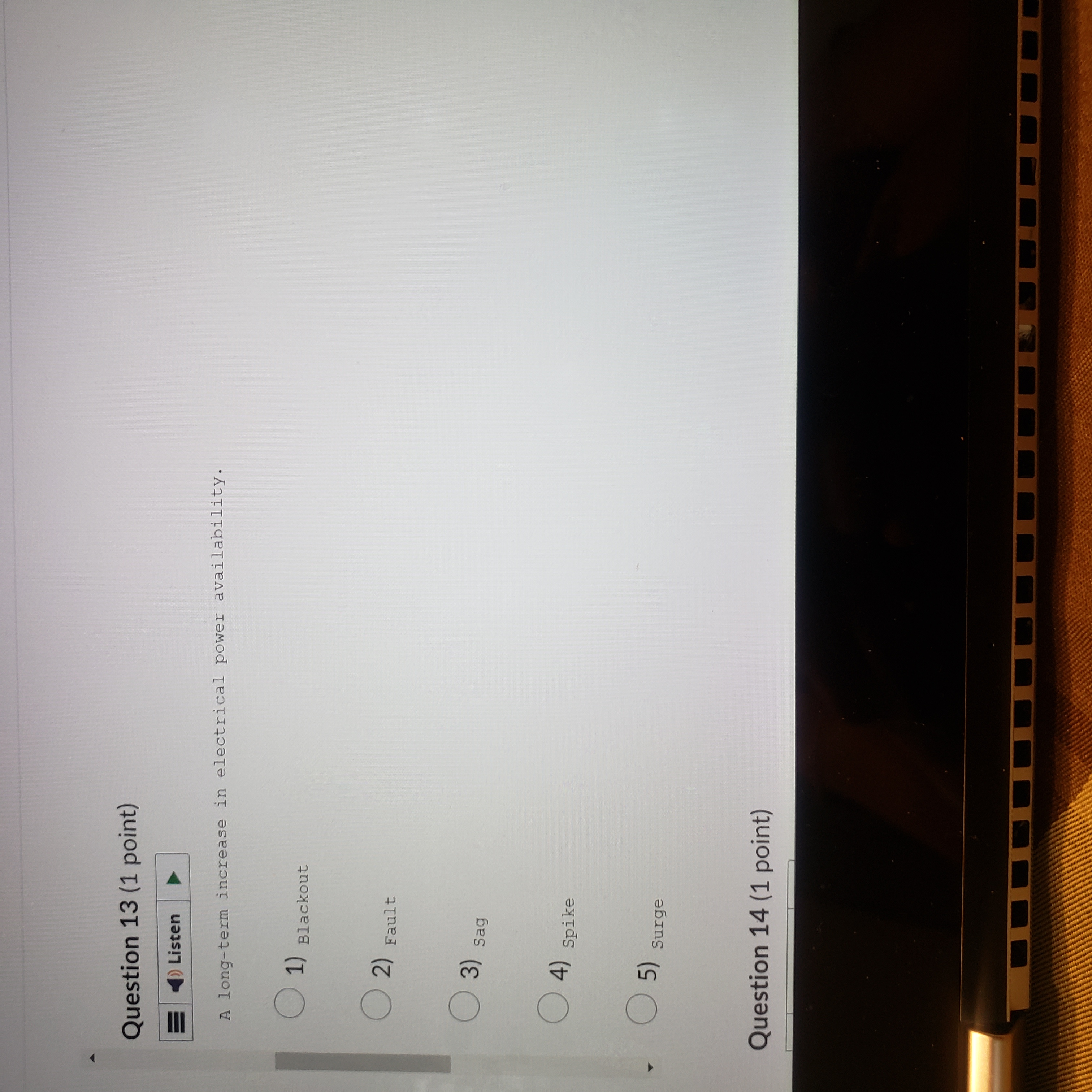
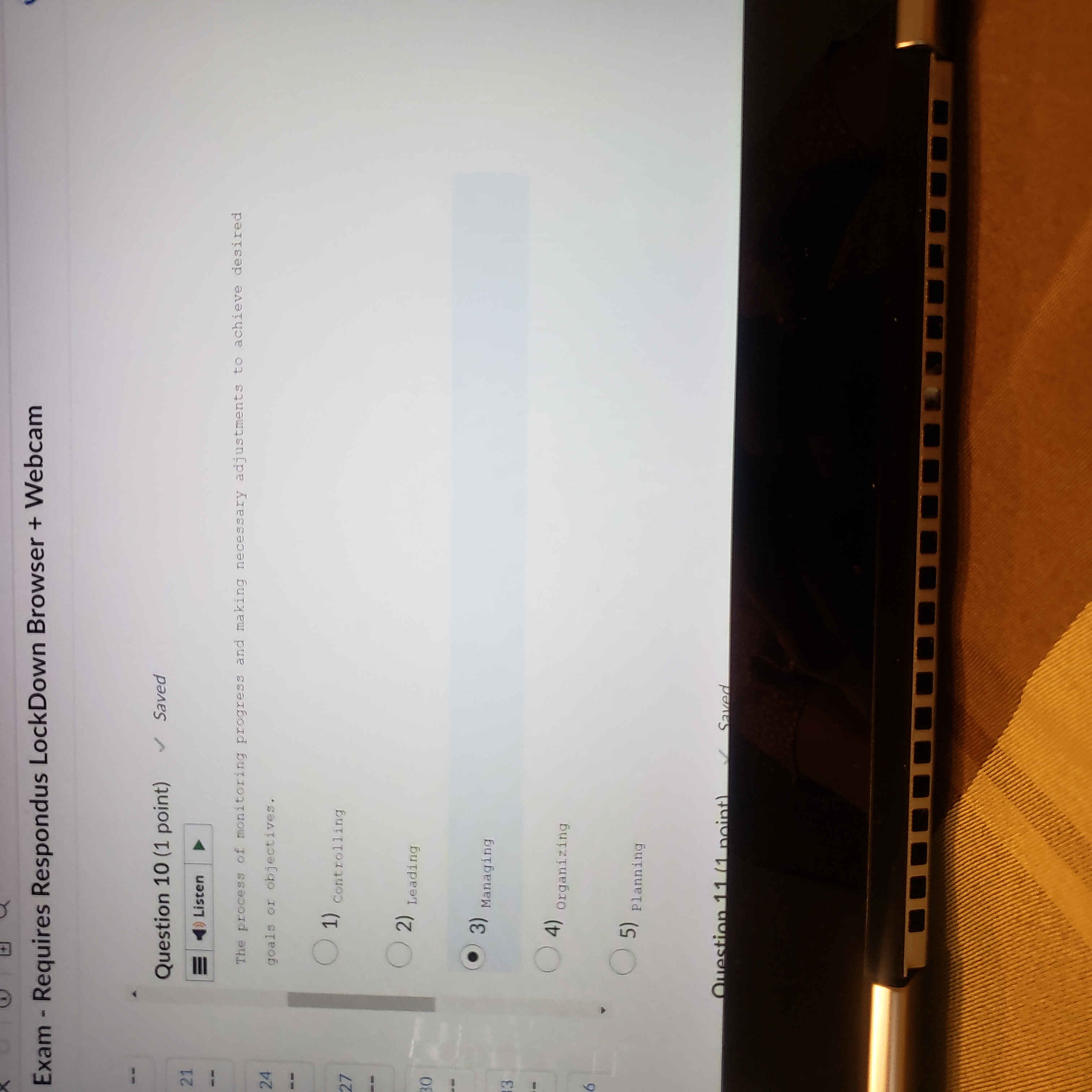
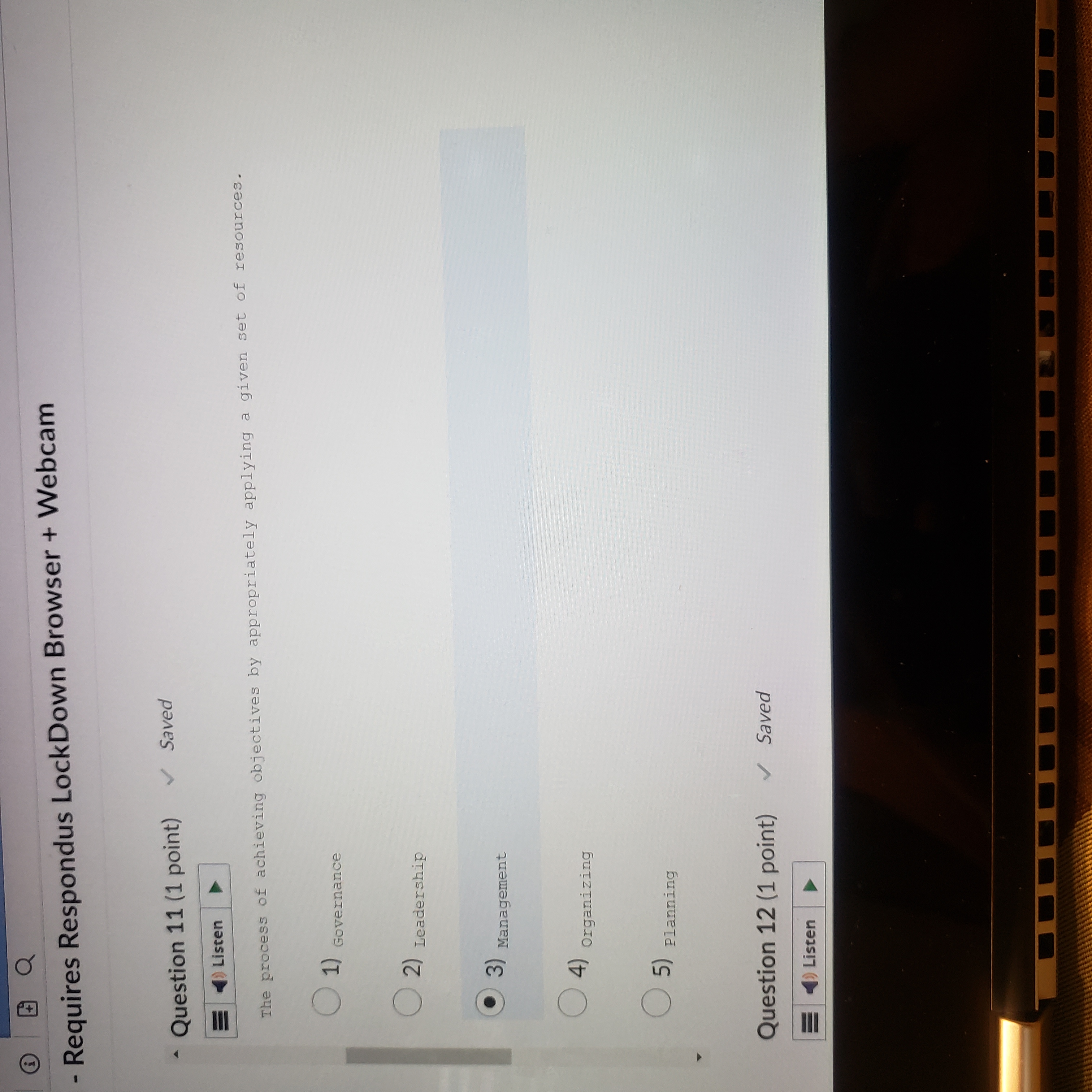
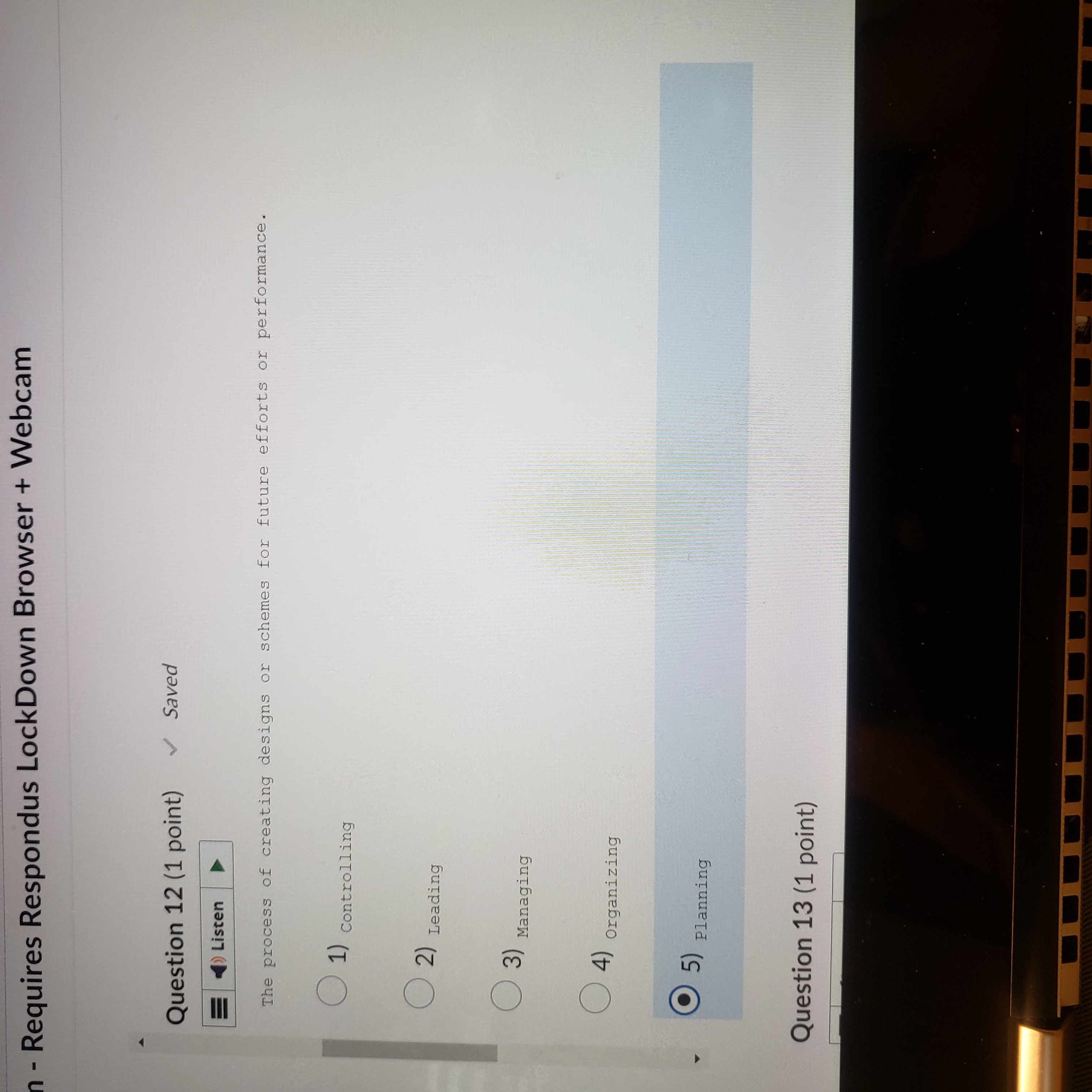
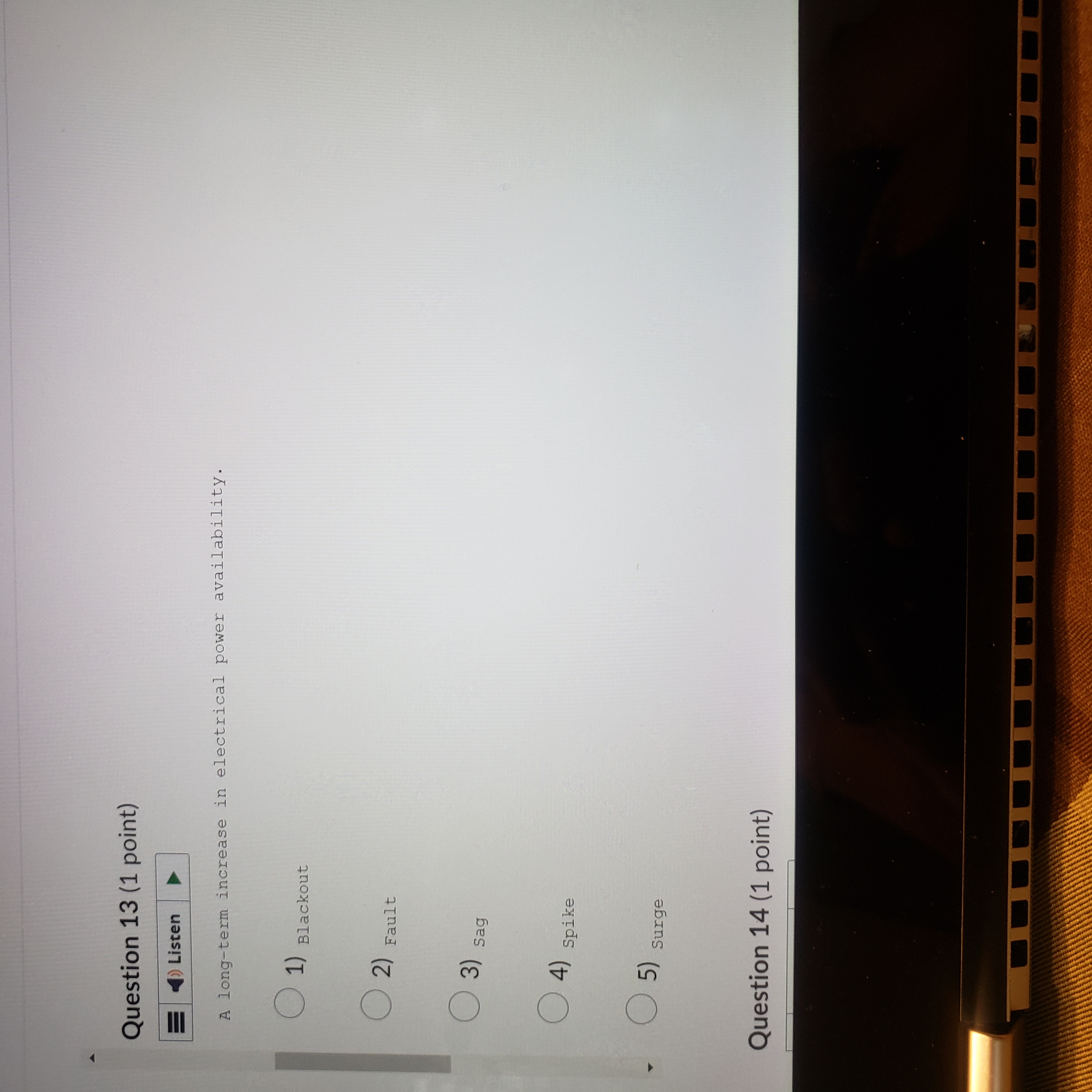
Exam - Requires Respondus LockDown Browser + Webcam Question 10 (1 point) Saved 21 ) Listen The process of monitoring progress and making necessary adjustments to achieve desired 24 goals or objectives. (1) controlling ( 2) Leading . 3) Managing (4) organizing (5) Planning Question 11 /1 mint) Saved- Requires Respondus LockDown Browser + Webcam Question 11 (1 point) Saved Listen The process of achieving objectives by appropriately applying a given set of resources. O 1) Governance ( 2) Leadership . 3) Management ( 4) )Organizing ( 5) planning Question 12 (1 point) Saved =)ListenQ Saved | I L CO44.4 ces Cor om g A c v o~ 2 - = v Question 12 (1 point) Question 13 (1 point) The Q e N % @ 5) Planning Question 13 (1 point) Listen A long-term increase in electrical power availability. (1) Blackout ( 2) Fault ( 3) sag ( 4) spike (5) surge Question 14 (1 point)Question 14 (1 point) Listen The average amount of time until the next hardware fault. (1) Maximum tolerable downtime (2) Mean time between failures ( 3) Mean time to diagnose ( 4) Mean time to failure ( 5) Mean time to repair Question 15 (1 point)Question 15 (1 point) Listen D An individual who manipulates the public telephone system to make free calls or disrupt services. ( 1) Cracker O 2) Hacker ( 3) H Hacktivist ( 4) Phreaker ( 5 ) Script kiddien - Requires Respondus LockDown Browser + Webcam Question 16 (1 point) = ) Listen The protection of all communications media, technology, and content. ( 1) Communications security ( 2) Cyber/ computer security ( 3) Information security ( 4) operations security ( 5) physical security Question 17 (1 point) all listenQuestion 17 (1 point) Listen The unauthorized duplication, installation, or distribution of copyrighted computer applications or data, which is a violation of intellectual property. 1) Back door (2) social engineering (3) software piracy ( 4) Spam ( 5 ) Spear phishing Question 18 (1 point)Question 18 (1 point) )Listen A person who accesses systems and information without authorization and often illegally. O 1) c Cracker ( 2) Hacker 3) Hacktivist (4) Phreaker (5) script kiddie Question 19 (1 point) = ) ListenQuestion 19 (1 point) Listen The set of responsibilities and practices exercised by the board and executive management with the goal of providing strategic direction, ensuring that objectives are achieved, ascertaining that risks are managed appropriately, and verifying that the enterprise's resources are used responsibly is known as Security (1) Governance ( 2) Leadership ( 3) Management (4) organizing ( 5) planningListen | The collection of pieces of non-private data that, when combined, may create information that violates privacy. Confidentiality ( 2) FOIA (3) Information aggregation (4) Liability ( 5) privacy Question 21 (1 point) = )Listen DQuestion 21 (1 point) =)Listen Formally sanctioned offensive operations conducted by a government or state against information or systems of another government or state. ( 1) Cracking ( 2) Cyberactivism 3) Cyberwarfare ( 4) Hacking (5) phreaking Question 22 (1 point)Question 22 (1 point) Listen A group of attacks whereby a person intercepts a communications stream and inserts himself in the conversation to convince each of the legitimate parties that the attacker is the other communications partner; some attacks of this type involve encryption. ( 1) Mail bomb ( 2) Man-in-the-middle ( 3) Pretexting ( 4) Rooting (5) spoofing Question 23 (1 point)Question 23 (1 point) Listen The process of influencing others and gaining their willing cooperation to achieve an objective by providing purpose, direction, and motivation. ( 1) Governance O 2) Leadership ( 3) Management ( 4) organizing (5) Planning Question 24 (1 point)Question 24 (1 point) = )Listen The policy document that guides the development and implementation of procedures regarding the collection, handling, and storage of items of potential evidentiary value, as well as the organization and conduct of related collection teams. ( 1) Apprehend and prosecute O 2) Evidentiary material ( 3) Evidentiary material policy ( 4) Forensics ( 5 ) Protect and forgetQuestion 25 (1 point) () Listen The U. S. -based international effort to reduce the impact of copyright, trademark and privacy infringement, especially via the removal of technological copyright protection measures . 1) Digital Millennium Copyright Act ( 2) Electronic Communications Privacy Act (3) Freedom of Information Act ( 4) Privacy Act ( 5) U.S. Copyright Law
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


